At this stage is it clear that, in order to be able to flexibly allocate resources to a user, the frame header should be enriched with more bits used for control signaling. Specifically, these bits should describe how TDMA slots are allocated in the actual frame, preceded by that frame header. For simplicity, let us stick to the fact that each packet has a fixed duration 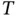 , equal to a TDMA slot, and the frame is composed of header and
, equal to a TDMA slot, and the frame is composed of header and 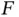 TDMA slots. Using the information in the frame header, Basil should be able to allocate any TDMA slot in the frame to any user. Thus, potentially, all slots of a given frame may be allocated to Zoya.
TDMA slots. Using the information in the frame header, Basil should be able to allocate any TDMA slot in the frame to any user. Thus, potentially, all slots of a given frame may be allocated to Zoya.
Let there be in total 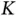 devices that have established links with Basil. In order to get a proper design of the frame header we need to address the following question: how many bits need to be added to the frame header in order for Basil to be able to make any possible flexible allocation of the
devices that have established links with Basil. In order to get a proper design of the frame header we need to address the following question: how many bits need to be added to the frame header in order for Basil to be able to make any possible flexible allocation of the 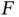 slots to
slots to 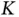 users? Assuming that no slot remains unallocated, there are
users? Assuming that no slot remains unallocated, there are 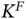 ways to allocate the slots. In order to be able to describe any of those allocations, the frame header should contain at least
ways to allocate the slots. In order to be able to describe any of those allocations, the frame header should contain at least
(1.4) 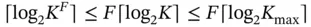
additional bits, where 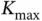 is the maximal possible number of active users in the system. The number
is the maximal possible number of active users in the system. The number 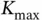 is known in advance and Basil is never expected to admit more than
is known in advance and Basil is never expected to admit more than 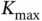 users. This assumption may look limiting, but is applied in practically all existing wireless systems. For example, some of the existing wireless standards impose that each device has a unique MAC identifier consisting of 48 bits, which means that the system design assumes
users. This assumption may look limiting, but is applied in practically all existing wireless systems. For example, some of the existing wireless standards impose that each device has a unique MAC identifier consisting of 48 bits, which means that the system design assumes 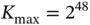 .
.
In order to get to the expression 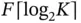 in (1.4), let us assume that the identity of each device that is active in the system is described by a fixed number of bits. Since there are
in (1.4), let us assume that the identity of each device that is active in the system is described by a fixed number of bits. Since there are 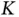 devices, the minimal number of bits to identify a device uniquely is
devices, the minimal number of bits to identify a device uniquely is 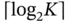 . If the user allocation is described by specifying the address of the device to whom the slot is allocated, then the header needs to use
. If the user allocation is described by specifying the address of the device to whom the slot is allocated, then the header needs to use 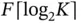 bits in total. The reader may object to the latter observation, since the number of connected users
bits in total. The reader may object to the latter observation, since the number of connected users 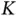 is variable, such that each time
is variable, such that each time 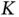 is changed, Basil needs to adjust the number of bits he uses to address the active devices. On the other hand, choosing
is changed, Basil needs to adjust the number of bits he uses to address the active devices. On the other hand, choosing 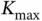 to define the length of the address may be very conservative and wasteful. However, in that case no additional signaling would be needed when the actual number
to define the length of the address may be very conservative and wasteful. However, in that case no additional signaling would be needed when the actual number 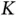 of users is changed.
of users is changed.
The most important implication from the previous discussion is: any flexibility in the allocation of the communication resources corresponds to additional signaling information or metadata that needs to be communicated between the base station and the devices . Thus the flexibility can offer better use of resources, but then the overall correct operation of the protocols becomes more vulnerable to the loss or errors in the metadata.
In order to make the most of the flexibility offered by the additional signaling bits, Basil should somehow know what is the most appropriate way to allocate the slots to the users in a given frame. For example, in an ideal case, Basil should allocate two slots to Xia only if he is certain that both slots will be filled with data to/from Xia. This is not a problem for downlink traffic from Basil to Xia, as Basil precisely knows how much data there is to send to Xia and can allocate the appropriate number of slots. More precisely, the data that can be allocated in this way should have arrived to the transmit queue of Basil before the header of the actual frame has started, such that the allocation can be announced in the header.
However, making the right allocation is not that simple in the case of uplink transmission. Unless the packets of Xia arrive in a perfectly predictable way, Basil cannot always know a priori how much data Xia has to send during the upcoming uplink frame and therefore Basil has either to guess it or learn it. Consider the case in which Basil allocates two slots to Xia in the uplink frame. Then the frame header sent by Basil can be understood as a polling or an invitation to Xia to send. If Xia has only one packet to send, then the second allocated slot remains empty. Intuitively, polling should use cautious allocation of resources and minimize the number of empty responses. However, if this allocation is overly cautious, then the devices end up being inhibited in sending all their data. This can be based on a knowledge or prediction about the current demand for uplink traffic across the population of terminals that have active connections to Basil.
But, how is this knowledge obtained by Basil? Going back to the analogy with speech, one can think of a conference scenario, in which the chairman (Basil) gives word to the individuals from the audience (devices or terminals). The first difference with the TDMA communication scenario from above is that whenever an individual speaks, not only the chairman but all the people in the audience receive the data. On the contrary, in our setting a mobile device does not communicate directly with another device. Furthermore, there is another difference with the TDMA operation described previously, which is essential for protocol operation. This is the way in which the individuals signal to the chairman whether they have an “uplink traffic”, which can be done by raising a hand or pressing a button. As already mentioned several times, a raised hand or a pressed button represent an additional communication channel. So, we stick to the dark room analogy and ask: how can we imitate the raising of a hand in a dark room in which the only way to communicate is to speak? This question leads to the idea of reservation packets .
Читать дальше

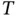 , equal to a TDMA slot, and the frame is composed of header and
, equal to a TDMA slot, and the frame is composed of header and 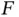 TDMA slots. Using the information in the frame header, Basil should be able to allocate any TDMA slot in the frame to any user. Thus, potentially, all slots of a given frame may be allocated to Zoya.
TDMA slots. Using the information in the frame header, Basil should be able to allocate any TDMA slot in the frame to any user. Thus, potentially, all slots of a given frame may be allocated to Zoya.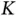 devices that have established links with Basil. In order to get a proper design of the frame header we need to address the following question: how many bits need to be added to the frame header in order for Basil to be able to make any possible flexible allocation of the
devices that have established links with Basil. In order to get a proper design of the frame header we need to address the following question: how many bits need to be added to the frame header in order for Basil to be able to make any possible flexible allocation of the 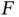 slots to
slots to 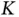 users? Assuming that no slot remains unallocated, there are
users? Assuming that no slot remains unallocated, there are 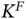 ways to allocate the slots. In order to be able to describe any of those allocations, the frame header should contain at least
ways to allocate the slots. In order to be able to describe any of those allocations, the frame header should contain at least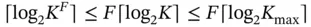
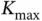 is the maximal possible number of active users in the system. The number
is the maximal possible number of active users in the system. The number 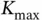 is known in advance and Basil is never expected to admit more than
is known in advance and Basil is never expected to admit more than 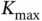 users. This assumption may look limiting, but is applied in practically all existing wireless systems. For example, some of the existing wireless standards impose that each device has a unique MAC identifier consisting of 48 bits, which means that the system design assumes
users. This assumption may look limiting, but is applied in practically all existing wireless systems. For example, some of the existing wireless standards impose that each device has a unique MAC identifier consisting of 48 bits, which means that the system design assumes 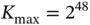 .
.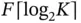 in (1.4), let us assume that the identity of each device that is active in the system is described by a fixed number of bits. Since there are
in (1.4), let us assume that the identity of each device that is active in the system is described by a fixed number of bits. Since there are 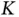 devices, the minimal number of bits to identify a device uniquely is
devices, the minimal number of bits to identify a device uniquely is 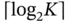 . If the user allocation is described by specifying the address of the device to whom the slot is allocated, then the header needs to use
. If the user allocation is described by specifying the address of the device to whom the slot is allocated, then the header needs to use 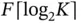 bits in total. The reader may object to the latter observation, since the number of connected users
bits in total. The reader may object to the latter observation, since the number of connected users 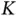 is variable, such that each time
is variable, such that each time 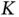 is changed, Basil needs to adjust the number of bits he uses to address the active devices. On the other hand, choosing
is changed, Basil needs to adjust the number of bits he uses to address the active devices. On the other hand, choosing 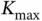 to define the length of the address may be very conservative and wasteful. However, in that case no additional signaling would be needed when the actual number
to define the length of the address may be very conservative and wasteful. However, in that case no additional signaling would be needed when the actual number 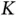 of users is changed.
of users is changed.










