1 Cover
2 Foreword
3 Acknowledgments
4 Acronyms
5 1 An Easy Introduction to the Shared Wireless Medium 1.1 How to Build a Simple Model for Wireless Communication 1.2 The First Contact 1.3 Multiple Access with Centralized Control 1.4 Making TDMA Dynamic 1.5 Chapter Summary 1.6 Further Reading 1.7 Problems and Reflections
6 2 Random Access: How to Talk in Crowded Dark Room 2.1 Framed ALOHA 2.2 Probing 2.3 Carrier Sensing 2.4 Random Access and Multiple Hops 2.5 Chapter Summary 2.6 Further Reading 2.7 Problems and Reflections Note
7 3 Access Beyond the Collision Model 3.1 Distance Gets into the Model 3.2 Simplified Distance Dependence: A Double Disk Model 3.3 Downlink Communication with the Double Disk Model 3.4 Uplink Communication with the Double Disk Model 3.5 Unwrapping the Packets 3.6 Chapter Summary 3.7 Further Reading 3.8 Problems and Reflections
8 4 The Networking Cake: Layering and Slicing 4.1 Layering for a One-Way Link 4.2 Layers and Cross-Layer 4.3 Reliable and Unreliable Service from a Layer 4.4 Black Box Functionality for Different Communication Models 4.5 Standard Layering Models 4.6 An Alternative Wireless Layering 4.7 Cross-Layer Design for Multiple Hops 4.8 Slicing of the Wireless Communication Resources 4.9 Chapter Summary 4.10 Further Reading 4.11 Problems and Reflections
9 5 Packets Under the Looking Glass: Symbols and Noise 5.1 Compression, Entropy, and Bit 5.2 Baseband Modules of the Communication System 5.3 Signal Constellations and Noise 5.4 From Bits to Symbols 5.5 Symbol-Level Interference Models 5.6 Weak and Strong Signals: New Protocol Possibilities 5.7 How to Select the Data Rate 5.8 Superposition of Baseband Symbols 5.9 Communication with Unknown Channel Coefficients 5.10 Chapter Summary 5.11 Further Reading 5.12 Problems and Reflections
10 6 A Mathematical View on a Communication Channel 6.1 A Toy Example: The Pigeon Communication Channel 6.2 Analog Channels with Gaussian Noise 6.3 The Channel Definition Depends on Who Knows What 6.4 Using Analog to Create Digital Communication Channels 6.5 Transmission of Packets over Communication Channels 6.6 Chapter Summary 6.7 Further Reading 6.8 Problems and Reflections Note
11 7 Coding for Reliable Communication 7.1 Some Coding Ideas for the Binary Symmetric Channel 7.2 Generalization of the Coding Idea 7.3 Linear Block Codes for the Binary Symmetric Channel 7.4 Coded Modulation as a Layered Subsystem 7.5 Retransmission as a Supplement to Coding 7.6 Chapter Summary 7.7 Further Reading 7.8 Problems and Reflections
12 8 Information-Theoretic View on Wireless Channel Capacity 8.1 It Starts with the Law of Large Numbers 8.2 A Useful Digression into Source Coding 8.3 Perfectly Reliable Communication and Channel Capacity 8.4 Mutual Information and Its Interpretations 8.5 The Gaussian Channel and the Popular Capacity Formula 8.6 Capacity of Fading Channels 8.7 Chapter Summary 8.8 Further Reading 8.9 Problems and Reflections
13 9 Time and Frequency in Wireless Communications 9.1 Reliable Communication Requires Transmission of Discrete Values 9.2 Communication Through a Waveform: An Example 9.3 Enter the Frequency 9.4 Noise and Interference 9.5 Power Spectrum and Fourier Transform 9.6 Frequency Channels, Finally 9.7 Code Division and Spread Spectrum 9.8 Chapter Summary 9.9 Further Reading 9.10 Problems and Reflections
14 10 Space in Wireless Communications 10.1 Communication Range and Coverage Area 10.2 The Myth about Frequencies that Propagate Badly in Free Space 10.3 The World View of an Antenna 10.4 Multipath and Shadowing: Space is Rarely Free 10.5 The Final Missing Link in the Layering Model 10.6 The Time-Frequency Dynamics of the Radio Channel 10.7 Two Ideas to Deal with Multipath Propagation and Delay Spread 10.8 Statistical Modeling of Wireless Channels 10.9 Reciprocity and How to Use It 10.10 Chapter Summary 10.11 Further Reading 10.12 Problems and Reflections
15 11 Using Two, More, or a Massive Number of Antennas 11.1 Assumptions about the Channel Model and the Antennas 11.2 Receiving or Transmitting with a Two-Antenna Device 11.3 Introducing MIMO 11.4 Multiple Antennas for Spatial Division of Multiple Users 11.5 Beamforming and Spectrum Sharing 11.6 What If the Number of Antennas is Scaled Massively? 11.7 Chapter Summary 11.8 Further Reading 11.9 Problems and Reflections
16 12 Wireless Beyond a Link: Connections and Networks 12.1 Wireless Connections with Different Flavors 12.2 Fundamental Ideas for Providing Wireless Coverage 12.3 No Cell is an Island 12.4 Cooperation and Coordination 12.5 Dissolving the Cells into Clouds and Fog 12.6 Coping with External Interference and Other Questions about the Radio Spectrum 12.7 Chapter Summary 12.8 Further Reading 12.9 Problems and Reflections
17 Bibliography
18 Index
19 End User License Agreement
1 Chapter 3 Table 3.1 Specification of the reception outcomes at Yoshi when Zoya and poss...
2 Chapter 6Table 6.1 A random sample of five consecutive channel uses.Table 6.2 Possible mapping of three data bits into two ternary symbols.
3 Chapter 7Table 7.1 Encoding rule for the simple code of rate 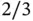 .
.
4 Chapter 9Table 9.1 Orthogonal codes allocated to the terminals.
1 Chapter 1 Figure 1.1 Communication model used in this chapter, referred to as a collisio... Figure 1.2 Illustration of two essential wireless features captured by the col... Figure 1.3 The problem of first contact when the mobile device Zoya is in the ... Figure 1.4 Rendezvous protocol for Zoya and Yoshi where both of them use half-... Figure 1.5 Downlink time division multiple access (TDMA). (a) Periodic equal a... Figure 1.6 Introduction of a header in the TDMA frame. (a) Periodic TDMA syste... Figure 1.7 Illustration of several ingredients required in a simple wireless T... Figure 1.8 Uplink transmission with a reservation frame. (a) Case when the all... Figure 1.9 Overlapped downlink and uplink frame for a full-duplex base station...
2 Chapter 2 Figure 2.1 Canonical scenario for random access protocols, where a number of u... Figure 2.2 An example of random access with probing. (a) Representation with a... Figure 2.3 A simple scenario for sharing the wireless spectrum between two col... Figure 2.4 Illustration of randomized spectrum sharing between two interfering... Figure 2.5 Transmission of a feedback packet 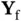 from Yoshi to Zoya for (a) a sl... Figure 2.6 Different multi-hop configurations that can arise if not all nodes ...
from Yoshi to Zoya for (a) a sl... Figure 2.6 Different multi-hop configurations that can arise if not all nodes ...
3 Chapter 3 Figure 3.1 Zoya and Xia communicate simultaneously with Basil. The left side d... Figure 3.2 Enhanced communication model with a strong and weak region. (a) Dep... Figure 3.3 Communication system with a strong/weak region around the base stat... Figure 3.4 Illustration of the use of SIC in the collision model. (a) Collisio... Figure 3.5 Strategies for communication in a collision channel without feedbac...
4 Chapter 4Figure 4.1 Introducing layering for a one-way wireless link. (a) Diagram of a ...Figure 4.2 Illustration of how layering deals with packets that can get out of...Figure 4.3 A simple layered model for two-way communication. Note that the arr...Figure 4.4 Packet exchange when the black box of the lower layer provides (a) ...Figure 4.5 An example of a layered structure for multiple terminals sending da...Figure 4.6 Scenario in which Zoya can establish a multi-hop connection to Xia....Figure 4.7 Protocol stacks: OSI versus TCP/IP.Figure 4.8 Example of clustered wireless networks. Each car represents a clust...Figure 4.9 Illustration of the points of convergence in different types of sys...Figure 4.10 A primer on wireless slicing for two services, broadband and low l...
Читать дальше

 .
.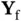 from Yoshi to Zoya for (a) a sl... Figure 2.6 Different multi-hop configurations that can arise if not all nodes ...
from Yoshi to Zoya for (a) a sl... Figure 2.6 Different multi-hop configurations that can arise if not all nodes ...










