As this book specifically addresses user-initiated loss (UIL), including malice and other potential forms of loss, you need to not just understand the concept of risk management as a whole, but also consider it in the context of mitigating the risk that is inherent in users.
This means you need to open your mind to potentially changing workflows and reducing some capabilities of users within your organization. While there may be some pushback against doing this, the reality is that while you are removing the ability of users to initiate loss, you are also simplifying the process and making it more efficient at the same time. In Chapter 1, we discussed the timers for cooking at McDonald's. Removing the discretion of the cooks delivers a more consistent product while reducing the potential stress for “eyeballing” properly cooked food and the inevitable reprimands when food is undercooked or overcooked.
In a traditional white-collar environment, there is usually concern about reducing the capabilities of an employee. However, the capabilities being removed are often those that are unneeded or unused. For example, many organizations provide employees with PCs and knowingly or unknowingly provide those employees with administrator access to their PCs. Having administrator access can enable the employee to potentially make more use of the PC, for example by giving them the ability to load new software, perform preventative maintenance, and so on. However, not all users will perform preventative maintenance how and when they should, and the software they load can create security vulnerabilities due to its source, its configuration, and so on. As a result, having users with admin access also opens the door to more ransomware attacks. In theory, the organization should have a process in place for acquiring software and performing maintenance (generally managed by a technology, security, or management department). Consequently, there are fewer benefits to users having administrator privileges, and those are outweighed by the potential loss.
These are the types of decisions that you have to make during the process of “stopping stupid.” You need to weigh the benefits of giving users specific capabilities against the potential loss those capabilities might cause. This requires a consideration of risk. The better you understand risk, the better you can make such determinations.
People normally assume that “risk” means the likelihood that something catastrophic is going to happen. In a manufacturing setting, it could mean that an error causes a major recall. From a safety perspective, it could mean that death or a major injury could happen to an employee or a client. From an IT perspective, it could mean that something causes a major network outage and takes down the organization. There is a fallacy that addressing risk merely means that you should try to prevent a disaster from occurring.
A smart risk reduction program looks at the breadth and depth of risks, large and small. The reality is that small risks, in aggregate, add up to major losses. This is the metaphorical death by 1,000 cuts, where a single cut is inconsequential, but with enough cuts, the loss of blood is deadly.
Risk can also include security concerns. The infamous WannaCry worm of 2017 was a worldwide ransomware attack that clearly had the impact to cripple enterprises. While regular malware does not usually have the devastating impact of WannaCry, in aggregate, all of the individual incidents combined add up to an impact that could potentially be as significant, if not worse than, WannaCry.
The concept of total quality management (TQM), discussed in Chapter 12, addresses the fact that small losses throughout a process add up to major losses. For example, if you have a manufacturing process that has 10 steps, and the defect rate is around 1% in each step, in total, your manufacturing process has a defect rate of roughly 10%. That is significant.
It is the same with all disciplines involving security and risk. A single incident involving a small loss may not be recorded. In organizations with strong safety programs, every injury reported, from a small cut to death, is recorded and tracked. However, in most organizations, few incidents are recorded and tracked. As we talk about risk management and security programs deserving more attention and resources, a significant way to begin to improve results is to record and track as many incidents as possible.
To address UIL, you need to understand where it comes from. You also need to know where and how to mitigate the loss, and even whether you want to do so in the first place. That might sound counterintuitive. Clearly, you want to mitigate loss as effectively as possible, but only when it makes sense to do so. It is possible that sometimes mitigating a particular loss is more expensive than to actually letting it happen.
To make these determinations, you need to understand how to approach them rationally. Unfortunately, there are many ways people react irrationally when it comes to loss. It is easy to get overwhelmed by anxiety and uncertainty when thinking about loss. It is also easy to be lulled into a false sense of security and ignore loss altogether, because a major loss seems so unlikely, while a minor loss seems unnecessary to worry about.
A similar problem is when organizations resign themselves to loss as a seemingly inevitable cost of doing business. This fallacy is where the sentiment of the user as the weakest link comes from. There is always something that can be done, but organizations, or more specifically, the people within the organization responsible for addressing the problem, don't know where to start or perceive it as useless to try.
To approach risk more rationally, it helps to think of it in terms of value, threats, vulnerabilities, and countermeasures and how they relate to each other. Figure 4.1represents these concepts as a high-level equation.
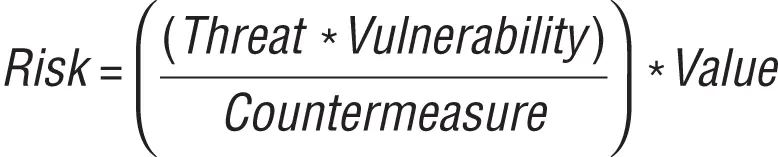
Figure 4.1 The risk equation
Looking at Figure 4.1, value is what is at stake. Threats are entities that will do you harm if given the opportunity. Vulnerability is a weakness that can result in harm if exploited. Countermeasures are efforts to mitigate a potential loss.
With specific regard to UIL, we want to differentiate between a threat and a vulnerability. For the purposes of dealing with UIL, you need to understand that a user is actually also a threat. As a threat, users cannot actually initiate loss unless there are vulnerabilities that allow them to do so. And even then, the threat can't successfully exploit those vulnerabilities unless there are insufficient countermeasures to prevent them from doing so.
In other words, yes, a user may have a moment of carelessness or malicious intent. However, the resulting action cannot result in loss unless there is both an environment that allows that user's action to initiate loss and insufficient countermeasures to mitigate that loss. When you understand and embrace the concept of risk from this perspective, you can begin to see UIL is clearly an addressable problem.
In the sections that follow, we will examine each of the elements of the risk equation, beginning with value.
NOTEThe risk equation discussed in this chapter is a high-level representation to help deal with risk on a conceptual level. It isn't a mathematical formula intended to be directly used with quantifiable figures. Although some disciplines, such as actuarial science, attempt to quantify risk for business purposes, that isn't our focus. We do, however, discuss practical metrics throughout the book, particularly in Chapter 10.
Читать дальше


![Сьюзан Кейн - Quiet [The Power of Introverts in a World That Can't Stop Talking]](/books/33084/syuzan-kejn-quiet-the-power-of-introverts-in-a-wo-thumb.webp)










