2 b) Acoustic Signal Processing [9]:In this method, the occurrence of the leak is treated as a fault in the wall of the pipe. The pressure difference profile inside a pipeline is usually from a higher-pressure potential to lower-pressure potential, this can be treated as an incident beam of light traveling from one end to the other end of the pipeline. A leak on the pipeline causes a disturbance in the pressure profile that can be seen a translucent substance in the path of the incident beam. Now, based on the time needed for the reflected beam to reach the pumping station, the exact position of leak is determined. A representation of the same is given in Figure 1.4.Since, the speed of sound wave propagation is in a single-phase, rigid pipe is found using the application of law of conservation of mass and comes as,Here, ν is the wave propagation speed in m/s, ρ is the density of fluid in kg/m3, Ee is the Young’s modulus of the piping material in N/m2, K is the bulk modulus of the liquid and ϕ is a factor of restraint based on the Poisson ratio.
3 c) Fiber Optic Method [10]:In this method, a helical strain of fibre optic cables runs along the length of the pipeline. The leak that is generated on the pipeline is seen as spikes in the strain profile of the fiber optic cable that is running along the pipeline. This strain profile is calculated using Brillouin Optical Time-Domain Analysis (BOTDA) [11]. BOTDA can be calculated using traditional mathematics and data analysis methods [12].
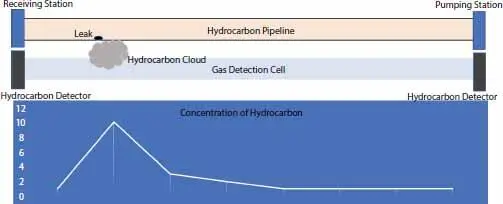
Figure 1.3 Vapor Sampling method of pipeline leak detection.
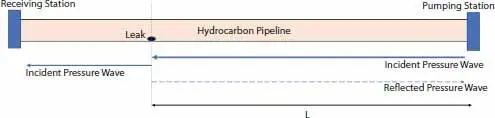
Figure 1.4 Acoustic method of leak detection.
We shall discuss in brief about three of the most common analytic and software-based technique used in pipeline leak detection. They are as follows:
1 a) Negative Pressure Wave method [13]:In this method, the drop in line pressure and speed profile is used to detect the leak, however, in this case, the process is heavily dependent on software techniques rather than hardware. The pressure wave is captured using sensors positioned in the upstream and downstream of the pipeline. The captured wave is then put through the extended Kalman Filters (EKF), used for non-linear systems to estimate the number of states required to model the pipeline system [14]. Extended Kalman filtering technique is used to estimate the state vectors that contain information about the segment of the pipeline, this combined with the virtual leakage rate gives an expression [15] that accurately derives the point of leak on the pipeline, provided that the initial conditions of the virtual leakage rate and that of the pipeline are same [16]. In addition, techniques like Haar Cascading are also done to do waveguide transformation/decomposition and analysis for detection of leakages [17].
2 b) Digital Signal Processing:This method uses process data such as pressure profile, flow profile, strain, entropy in flow, etc. to identify and analysis various features which help in identification and detection of leaks in pipeline systems.Features such as energy of the signal, entropy of the signal, zero crossings cut and energy distribution in decomposed wavelet is analyzed [18].Of these, zero crossings cut is the most significant, as it identifies the events where a high value (defined as 1.5 times the mean of the signal amplitude (positives only)) occurs immediately after a 0 or negative value). These features show us spikes in the flow data and which are then run through a Fast Fourier transform (FFT) for signal decomposition and transformation. This transformed signal wavelet or flow data is then run through a Neural Network, that classifies suitable data as leakages.A representation of the process is given in Figure 1.5.
3 c) Dynamic Modeling Approach:This is a method that is gaining popularity with the advancement of our understanding of the usage of classical and modern statistical techniques. We have already discussed the used of states of the fluid flow in the method that used EKF for feature extraction. Using the concepts of Fluid mechanics, the flow can be modelled in terms of partial differential equations, which in turn can be transformed into state space equations, these state space equations are used to determine the behavior (wave profile, pressure profile, flow profile etc.) of fluid and any disturbance can then be analyzed to detect leakages. In addition, computational fluid dynamics (CFD) is being used to model and detect leakages in pipes.
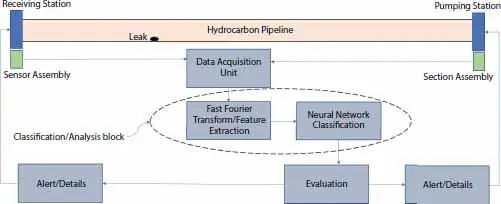
Figure 1.5 Digital signal processing based pipeline leakage detection.
1.3.2 Use of IIoT to Detect Pipeline Leak
Use of IIoT is gaining popularity with the advent of usage of more connected devices being used in industries day in and day out.
A typical IIoT based unit shall have all devices interconnected with each other. These devices are again connected to a network that terminates at a gateway. The gateway has a two way terminal connecting the analytics block with itself. The analytics block again has a two way terminal connecting it to the rules and controls unit.
In our case the pipeline is the system that has its upstream and downstream connected to each other. The sensors at the upstream, downstream and along the length of the pipeline are interconnected among each other and are also in turn connected to an edge gateway. This gateway connects the system to analytics and transform unit that is used to generate leads for the process. This connection is through an access network, which is typically a network that can handle high volume of uploads and downloads. After this the leads are sent to control unit which based on the leads generate controls or rules for the system, this is again through a network called the service network and has to be able to handle high volume of uploads and downloads.
A representation figure describing the usage of IIoT architecture in detection of leakage in pipeline custody transfer, is given in Figure 1.6,
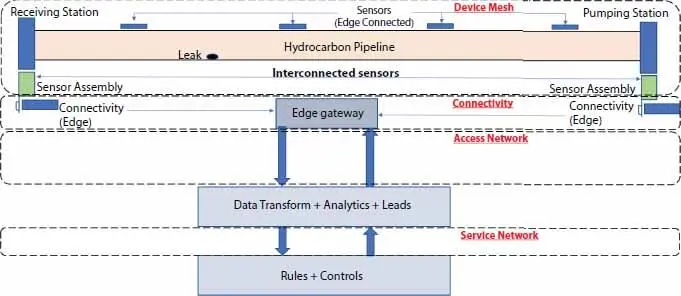
Figure 1.6 Industrial Internet of Things-based architecture for pipeline leak detection.
1.3.3 Use of Machine Learning Algorithms to Detect Pipeline Leak
Machine Learning and Data science has gained a lot of popularity in the last decade. In the earlier sections of the chapter, we demonstrated the usage of Neural Networks for detection of leaks in a pipeline, that itself was a pre cursor of introduction of machine learning in the field of leakage detection of pipeline transfer of hydrocarbon.
Several machine learning algorithms have started being used for detection of leaks. Advanced techniques such as Neural Networks [19] and Support Vector Machines [20, 21] have already been used and proved to have given excellent results. In addition, more advanced methods employing deep learning and convolutional neural networks [22] are also being explored, in fact application of Variational Autoencoders have already been tested and used.
We shall now discuss the technique of implementation of each of these methods (Neural Network and Support vector machine based) in brief, in addition, we shall also try to implement a novel strategy to use ensemble learning algorithms to detect leakages in pipelines [23].
Читать дальше
















