All the nodes inside blockchain architecture create a consensus protocol. A consensus system is a set of network rules, and if everyone abides by them, they become self-enforced inside the blockchain.
To manage and protect the term privacy under blockchain technology, one must satisfy the subsequent requirements:
1 The links between the transactions must not be visible or discoverable.
2 The data of the transactions is merely and only known to their members.
The private or open blockchain must have an entrance control strategy or approval plan to fulfil the security prerequisites of blockchain, which fulfils the total straightforwardness of the blockchain information. Be that as it may, if the case is of an open setting, everybody can have an access to the blockchain with no limitations, the protection issues must be handled on the following factors:
1 Identity Privacy: Which alludes the intractability and unmanageability in the middle of the transaction contents and thus the original identities of their partakers stay sheltered, safe and secure about.
2 Transaction Privacy: In the following the transactional contents (e.g., amount or transacting patterns) can only be accessed and captured by the specified user(s), and kept secret, unknown and safe to the common or general public blockchain network [1, 4].
As it is referenced over, a transaction or a block of a blockchain contains the identity of the previous transaction, the addresses of its members or participants, values (trade), timestamp and unique mark of its sender. Due to its natural behavior or characteristic, it is possible to trace back and follow the flow of transactions to extract and collect the users’ physical identities or other common and additional private information through the tools techniques and also of data mining. In this section, it is referred towards the Bitcoin system as a typical instance to analyze the privacy threats for the blockchain network.
Users majorly/always create an alias when they hook up with the Bitcoin system. However, thanks to the general public and openness of blockchain, it’s possible to run a static analysis of the blockchain which allow us to track and unhide the masked users, that’s what de-anonymization is. Here, we have list out many attacks which will work under to de-anonymize the users’ real identities.
1.3.1 Analysis of Network
The blockchain majorly performs its work on the P2P network, which suggests that a node will share public its IP address when broadcasting the transactions. Researchers and scientist have identified three abnormal relay patterns for analyzing the network which could be mapped to Bitcoin addresses to IP addresses (i.e., multi-relayer & non-rerelayed transaction, single-relayer transactions and multi-relayer & rerelayed transactions).
1.3.2 Transaction Fingerprinting
Another major issue or threat that can cause problem to the data of transaction and for which the anonymity becomes problem is a transaction’s user-related features. Androulaki et al. have explained six characteristics that may portray a few highlights of transaction conduct, i.e., Random time-interval (RTI), hour of day (HOD), time of hour (TOH), time of day (TOD), coin flow (CF) and input and output balance (IOB). Abundance consideration on these characteristics may expand the odds to de-anonymize an individual client [1].
A denial-of-service assault might be a cyber assault and the most known and basic issue, where the noxious assailant attempts to look for or hack a machine or system asset being inaccessible to its customers by disturbing or ending web/network services of the host associated with the web or neighborhood server. The most well-known way or method to deal and handle with, be covered up by IP addresses or to hide the IP in P2P network is utilizing anonymity network systems (e.g., TOR).
A Sybil attack is another digital attack where the pernicious attacker and programmers destabilize the stature or notoriety system of a P2P network by making an outsized number of nom de plume or phony characters, utilizing them to understand a disadvantageous impact. Concerning the de-anonymization inside the blockchain, Bissias et al. broke down and judge that Sybil attacks could stop and break the decentralized anonymity protocol and can expand the likelihood to search out the clients’ genuine identities.
1.4 Transaction Pattern Exposure
Except some personal information, majorly all transactional information goes to the public network which can be used to get the statistical distribution, which may help to get some guidelines and regulations for the blockchain applications.
1.4.1 Transaction Graph Analysis
Under this the major focus is on discovering and analyzing some overall transaction features (e.g., daily turnover, exchange rate or transaction pattern) over time.
1.4.2 AS-Level Deployment Analysis
This technique aims to get the bitcoin network by recursively connecting to clients, requesting and collecting their lists of other connected or peer IP addresses. In this flow, one can obtain concrete and correct information and data on size, structure and distribution of the bitcoin’s core network.
1.5 Methodology: Identity Privacy Preservation
This part of the chapter presents a summarized overview of solutions that have been recently proposed by researchers aimed at maintaining and preserving privacy of the blockchain [1]. In a public blockchain, for example, in the digital currency or crypto currency Decreed, it is adviced and proposed that the clients’ address should have been adjusted and altered by creating another key pair for every session. Except that, there are three frequently-used systems and methods for safety and security and protecting anonymity in the blockchain and they summarized by: mixing services, ring signature, and non-interactive zero-knowledge proof.
As per the structure discussed in previous few sections the blockchains are linked with each other like sender or receiver of a transaction, therefore, by calculating and analyzing the public content (i.e., analytical attack), an individual can deduce some secret or privacy information or data to eliminate such attacks. One of the solutions is to confuse or blur the transaction’s relationships with the help of mixer (aka tumbler or laundry ) as shown in Figure 1.5. The first mixing service introduced by Chaum [1], allows the user to hide his content of communication as well as the participants of the communication. The same concept is shown below in pictorial manner.
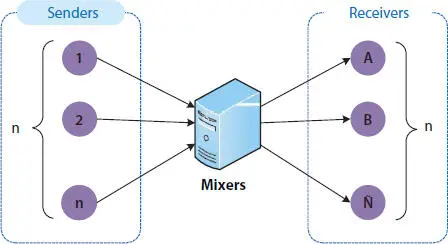
Figure 1.5Basic architecture of mixing services [1].
Assume that one element prepares a message M for delivery to another substance at address R by encrypting it with the receiver’s open key KR, appending and attaching the address R, and afterward encrypting the result with the intermediary’s open key KI. The left-hand of the accompanying expression means the cipher content, which is transferred to an intermediary:
KI (r0, KR (r1, M), R) → KR (r1, M), R [1].
The symbol indicates the transformation of the cipher message by the intermediary into another cipher content appeared on the right-hand side. These transformations perform a decryption on the original cipher message by the intermediary with its private key. At that point the intermediary delivers the sub-cipher content to R who at that point decrypts it with his/her own private key. It is important to take note that r1 and r0 are random numbers which ensure that no message is transferred more than once [1].
Читать дальше













