Understanding it with the help of a relevant example like work on the Google docs and wait for others to make the necessary changes if required the same scenario is in the decentralized architecture of the blockchain. Blockchain allows and permit us to make the relevant docs shared rather copied [2, 3]. This distributed piece of information (ledger) provides the trust factor and the security of data.
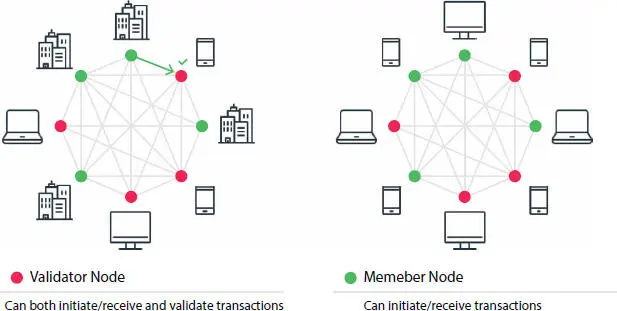
Figure 1.2The diagrammatic representation of the types of blockchain architecture [3].
Figure 1.3Figure states the types of blockchains in trend.
Whereas the exact different case is there in the centralized architecture, the information or ledger which was shared is now kept private and shared with the authentic and with those who have required and necessary authority to access the data, which means now the data/ledger is kept private and not shared globally.
Now what left the distributed architecture, in this type a local copy of the ledger is given to all the parties/entities, so that the major alterations are done by the high officials or the major party whereas the information of the ledger is being distributed within the complete locality.
Table 1.1 will make the concept more clear and transparent to understand.
Table 1.1A novel comparison among public, consortium, private blockchain.
| Property |
Public blockchain |
Consortium blockchain |
Private blockchain |
| Consensus determination |
All miners |
Selected set of nodes |
Within one organization |
| Read permission |
Public |
Public or restricted |
Public or restricted |
| Immutability level |
Almost impossible to tamper |
Could be tampered |
Could be tampered |
| Efficiency (use of resources) |
Low |
High |
High |
| Centralization |
No |
Partial |
Yes |
| Consensus process |
Permission less |
Needs permission |
Needs permission |
1.1.1 Public Blockchain Architecture
A public blockchain architecture states that the data or the ledger and access to the system is available to anyone who is willing to participate for instance Bitcoin, Ethereum, and Litecoin blockchain systems are public and can be accessed by anyone globally [2, 3].
1.1.2 Private Blockchain Architecture
An opposite situation to the public blockchain architecture, the private system is highly controlled and managed only by users from a specific organization or institution or the company or authorized users who have an invitation for participation.
1.1.3 Consortium Blockchain Architecture
This blockchain structure can consist of a few organizations [3]. In a consortium, procedures are set up and controlled by the preliminary assigned users. It a system that is ‘semi-private’ and has a group which controls it, but works across different organizations. In simple terms it can be said as a distributed blockchain architecture.
The following table provides a detailed comparison among these three blockchain systems [3]:
1.2 The Privacy Challenges of Blockchain
In the previous section, the basic introductory part of blockchain is discussed. In this part the requirement of privacy including different tools and techniques are going to be discussed.
As shown in Figure 1.4 in this section, a blockchain is a highly secure mechanism or technology which allows the user to make secure and safe transactions [1, 3]. It is a statement said by many engineers, scientist and researchers but how......?
To know about this said statement in detail, one should back track a blockchain and need to collect the required information about how this technique is too strong and safe for transactions. Here we also need to know if this technology is too tremendous then why was it being garbaged in 1991 and then again re-launched in 2004 [1].
The working paradigm of a blockchain:
Let’s have a closer and a deeper look at Figure 1.4 that illustrates what a block is in a blockchain.
Each block in a blockchain consists of:
certain data
the hash of the block
the hash from the previous block (HOPB).
The data stored in each block completely depends on the type of blockchain. For instance, in the Bitcoin blockchain structure, the block maintains data about the receiver, sender, and the amount of coins.
A hash is a unique set of alphanumeric codes which is auto generated by the algorithms and the functions of the blockchain (in general terms it can be treated as the fingerprint, long record consisting of some digits and letters). Each block hash is generated with the help of a cryptographic hash algorithm (SHA 256) [1]. As a result, this helps to identify each and every block in a blockchain structure easily. The moment a block (of blockchain) is created, it automatically gets connected or attaches a hash, while any changes made in a block either in the ledger field or anywhere it straightened affects the change of a hash too which makes the technology precisely highly safe and secure. In simple terms, the hashes help to detect any changes in blocks of a blockchain.
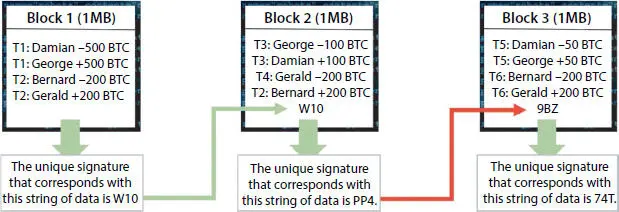
Figure 1.4The figure states the internal working paradigm of a blockchain.
The final element within the block is the hash which is from a previous block (refer to Figure 1.4). This creates a chain of blocks and is the main element behind blockchain architecture’s security [4]. As an example, assume a bock range from 1 till 46; block 45 points to block 46. The very first block in a chain is a bit special—all confirmed and validated blocks are derived from the genesis/creator block.
Any corrupt attempt provokes/results the blocks to change [4, 5]. All the assumed block’s hashes get changed resulting to the mismatch of hashes which then carry incorrect or invalid information and render the whole blockchain system invalid.
On the other hand, in theory, it could be possible enough to adjust or alter all the blocks with the help of strong computer processors (processors here means highly configured computers). However, there is a solution that eliminates this possibility called proof-of-work [1]. This allows a user to slow down the process of creation of new blocks. In the architecture of Bitcoin blockchain, it majorly takes around 10 min to determine or collects the necessary information of proof-of-work and adds a new block to the chain, but as it was discussed the block can only be added by the person which have the best computational system, here logical ability works rare rather than the system power, hence this work is done by miners—special nodes within the Bitcoin blockchain structure. The miners who win in the race get to keep the transaction fees from the block that they verified as a reward [1, 4].
Each new user (node) joining the peer-to-peer network (a network which have internet connection to share files and folders) of blockchain receives a full copy of the system. Once a new block is created, the detail of it is sent to each node within the blockchain system [4]. Then, each node verifies the information of the block and checks whether the information/data stated there in the block is correct. If everything is alright, the block is added to the local blockchain in each node.
Читать дальше















