1 ...7 8 9 11 12 13 ...20
1.4.2.2 5G Protocol Flaws Might Cause Security Flaws
As the hoopla continues to grow concerning the 5G network, some folks forget it’s not excellent. In late 2018, a search cluster disclosed that though the 5G network has higher security compared to the 3G and 4G networks, a few of the vulnerabilities in those earlier versions got carried over to 5G, too. As an example, one drawback permits hackers to observe the final neck of the woods of a definite transportable on the 5G network. It’s unclear; however, those problems could influence IoT devices. Maybe AI could get the image if an organization develops Associate in Nursing algorithmic rule that may spot the hacking tries that exploit that vulnerability.
1.4.2.3 5G Could Amend the Styles of Attacks Folks With IoT Devices
Another facet of 5G that folks’ remark frequently about is its property benefits which can open potentialities for people to simply use additional powerful, connected devices. This usage increase is a few things that worry Dr. Darren Williams, the chief executive officer and co-founder of cybersecurity company Black Fog. Williams asserts that 5G technology and the associated speedy increase in information might make it easier for hackers to orchestrate additional wide-scale attacks while not obviously noticed. Some of the reliable tips folks use currently to stay secured while on their IoT devices is staying valid when the “5G” network launches. As an example, it’ll forever be wise for people to arrange and style their networks for resilience. Moreover, it’s helpful for organizations to keep updated lists of all their IoT devices, together with technical details like IP addresses. But the potential security threats expose by the “5G” network for IoT devices could need IT professionals to adapt their strategies. Some may use AI to mitigate the risks. As an example, Black Fog uses twelve recursive layers of security to stop information exfiltration and different threats. The tool conjointly encompasses a learning mode that has reports concerning what it could have blocked, which however it doesn’t act on.
1.5 A Genetic Algorithm for 5G Technologies With Internet of Things
There is growing work of that knowledge process thanks to the modernization of good gadgets which have been produced for the maximum capacity of networking along with wireless features within the coming years. As with the successful launching of the fifth-generation connectivity, it should be able to handle the scalability of the interconnected network and growing quantity necessary strategies like quantifiability and output. In this paper, we outline network designing as an associate degree optimization drawback with the choice variables like transfer of the energy and the location in the fifth-generation wireless network. The chosen variables lent themselves to attention-grabbing implementation victimization with many heuristic approaches, like differential evolution (DE) algorithmic program and Real-coded Genetic algorithmic program (RGA).
The green space might be another phase that expects to defend Earth and add to lessening the overall warming with productivity improving the vitality utilization. In this manner, the need for vitality prudent remote systems has drawn significant consideration and spotlights on the need to hack operational costs and force utilization of the broadcast communications foundation in any place radio systems speak to concerning eightieth of vitality utilization. In addition, it’s wide remarkable that base stations (BSs) expend a major amount of the vitality in an extremely cell organize, which needs advancement of the transmission force and situation of a four-year college education identifying with unpracticed perspectives as shown in Figure 1.12. Luckily, 5G systems might want the position information and appropriately control the remote system styles and advancement. There are numerous approaches to search out exact area information in remote systems along with associated separations, speeds, edges, delays, and unsurprising client conduct [5] in 5G systems. The information acquired from area are mindful innovations that are regularly acclimated and address different issues by actualizing sharing and presenting ways to deal with the difficulties in 5G systems upheld by the client’s position. By getting a great deal of right information of the clients, power intensity is frequently improved by placing the extra base stations in an extremely reasonable position that bolstered the client’s conduct. Over-burden and postponement may likewise be decreased by exploitation area mindful information.
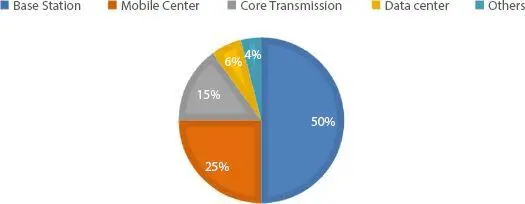
Figure 1.12The energy consumption ratio in cellular networks [10].
The system model assumes that we tend to reflect occupying the world of Km for 5G/LTE networks as the hoopla continues to grow concerning the 5G network, some folks forget it’s not excellent. The lesson learned here is that it shouldn’t anticipated that the 5G network is foolproof regarding security. The inclusion chance inside the space around the area with a limit is a littler sum than the SINR (Signal to Interference Noise Ratio). The SINR is determined by exploiting it, any place the MHA gain, the transmission power, and talk about with the obstruction and clamor, severally. Consider the following equation

1.5.2 The Planned Algorithm
The application of EAs like GA, DE, and RGA may be a random exploration technique for finding each strained. At liberty optimization issues, that area unit supported the survival of the fittest. This procedure drives the biological evolution, in such a fashion that a population of individual solutions is deceivingly changed. At every part, EA probabilistically selects promising people from this population to be folks and so uses them to supply their offspring for the next generation using crossover and mutation mechanisms. As such, the appliance of EA provides satisfactory solutions to NP-hard optimization issues. To boot, EA is additionally accustomed to solve several practical problems like finding associate degree optimum position for a bachelor’s degree in an exceedingly given space of interest. First State approach in simulation results. Associate degree illustrative example is shown within Figure 1.13. As the hoopla continues to grow concerning the 5G network, some folks forget it’s not excellent. In late 2018, a search cluster disclosed that though the 5G network has higher security compared to the 3G and 4G networks, numerous the vulnerabilities in those earlier versions got carried over to 5G, too. As an example, one drawback permits hackers to observe the final neck of the woods of a definite transportable on the 5G network. It’s unclear; however, those problems could influence IoT devices. Maybe AI could get the image if an organization develops Associate in Nursing algorithmic rule that may spot the hacking tries that exploit that vulnerability. But the lesson learned here is that folks shouldn’t anticipate that the 5G network is foolproof regarding security. Specialists already recognize that issues exist. The queries that stay are whether the 5G protocol can get improved, and if not, what adverse impact can the problems have?
As shown in Figures 1.13 and 1.14, the authors write up an algorithm that offered the changed RGA methodology for allocating the best positions of the long run 5G base stations. Figure 1.15 indicates the working example of transmission algorithm mentioned in Figure 1.14. The changed RGA has achieved sufficiently higher performance in terms of transmitting power-saving and total connected users for 5G networks with providing the best coverage. The changed RGA has found success with the tidy higher configuration by scrutinizing with standard Delaware and RGA to find the correct location and to adjust the varying ability level further to coverage constraints. In the current and future work they are going to study the best BSs (Base Stations) and their price relating to frequency level victimization a complicated Semitic deity. We are going to conjointly investigate the written record evolution of the energy within the normal of satisfactory QoS (Quality of Services).
Читать дальше














