Figure 2.3 Integration of cloud computing and IoT.
2.5 The Concepts That Rules Over
2.5.1 Artificial Intelligent
This unifying theme is the idea of thought processes and reasoning addressing the behavior which measures the success in terms of fidelity to human performance with an ideal concept of rationality referring to the study of computation that perceives reasons and act. This study of ours cognitively works with the basics of our latest technological artifacts of this artificial intelligence in a relative approach to machine learning theories and algorithms being play backed upon with reasons. It is a formal analysis of propositional logic [22]. This is what we have put up in our study.
2.5.2 Overview of Machine Learning
Machine learning which is deduced as a structural study in presenting the theme as a substantial field of artificial intelligence which has an objective of empowering the systems with the capability of using data to learn and develop without the process of being programmed explicitly.
Machine learning algorithms can be categorized as follows.
2.5.2.1 Supervised Learning
It is one of those learning methods, which makes over the models which are being trained using marked data. The goal of this learning technique is to train the model in such a way that we can predict the output when it is being applied upon with given new data over it. Here, both input and desired output data pave path for future events predictions [23]. For accurate predictions, the fed data is labeled or tagged as the perfect presumption. The schematic representation of output prediction or classification represented in Figure 2.4.
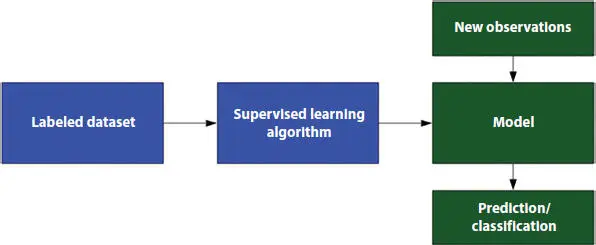
Figure 2.4 Supervised learning.
2.5.2.2 Unsupervised Learning
Unsupervised learning is one those finest learning techniques being a diversified part of machine learning methods in which the unlabeled input data infers the patterns desired [24]. There is no provision of providing training data, and hence, the machine is made to learn by its own. But at the same time, it is also taken care of that the machine must be able to do the data classification without any information about the data is being given beforehand.
The objective of unsupervised learning is to find out the structural prospective and patterns from the data which given as input. It does not require any kind of supervision for training the model. Rather, it makes out the patterns from the data on its own. The structure of this learning process can be referred from Figure 2.5. The basic ideology behind this is to expose the machines to a greater volume of different data and allow it to learn from the provided insights which happened to be unrecognizable previously to recognize the hidden patterns.
Like that, there are no necessarily defined outcomes as deduced from unsupervised learning algorithms. Instead, it reciprocates what is the indifference feature from the provided data set.
The machine requires to be programmed in such a way that it learns on its own. The machine needs to understand and get on with distinctive insights from both structured as well as unstructured data.
It may also so happen that the unsupervised learning model may provide less accurate results as in comparison to supervised learning technique.
It includes various algorithms such as Clustering, K-Nearest Neighbor (KNN), and Apriori algorithm.
Figure 2.5 Unsupervised learning.
2.5.3 Applications of Machine Learning in Cyber Security
Threats upcoming and classification
Scheduled security task, automations, and user analysis optimization
Network risk scoring
2.5.4 Applications of Machine Learning in Cybercrime
Unauthorized access
Evasive malware
Spear phishing
2.5.5 Adherence of Machine Learning With Cyber Security in Relevance to IoT
Along with machine learning, cyber security systems perform a proper analysis of patterns and learn the ways to help associate the ways of prevention of liked attacks and reciprocate to the changing behavior. At the same time, it can help the cyber security teams to be proactively involved in prevention of threats and reactively responding to the real-time active attacks. It can also lessen the amount of time spent on scheduled tasks and enable the users and the related organizations in any similar aspects for resource utilization more strategically. Machine learning can take over cyber security in a simpler and effective way which seems to be more proactive but less expensive. But it can only perform if the underlying data supporting machine learning gives a clear image of the environment. As they say, garbage in, garbage out [25]. As of the concerned study, the explicit description is much flexible with respect to the chang es carried out in the conditional algorithm in the utility functions that can be reflected by the identical data nodes in evaluating the decision network strong enough to accommodate the observational reflections in cyber metric network zones, which when applied will definitely go on for a substantial proliferation of safety and security in going at par with IoT devices in excellence.
As of a debated verse, these days that internet is hardly a secure environment itself that makes IoT devices even less so, but with technical knowhow and implementing those technical aspects, we can make a turnover to make it a differentiable in its context. There have been several high-profile events, involving the use of IoT devices as nodes in wider botnet attacks that highlight IoT’s vulnerability. With one of the finest examples being the Mirai malware which runs over the largest DDoS attack that targeted French cloud computing site OVH and even lighter in the particular year. Besides, along with the advent of maturity, security will tend to be a market differentiator.
A company selling web cameras which provides lifelong security upgrades may accumulate greater sales than a rivalry company which never does [26]. Further, many risks are enliven with both home and enterprise. IoT makes up the following non-exhaustive list:
Secured data issues
Risk of being safe personally and publicly physical safety
Privacy issues like home devices being hacked
Growth of IoT devices being followed by data storage management
2.5.6 Distributed Denial-of-Service
A distributed denial-of-service (DDoS) attack can be enumerated as a malevolent attempt to disrupt the congestion within target server, amenity, or network by profusing the target and its neighboring architectural infrastructure with a rush of internet traffic.
A DDoS attack can be enumerated as an initiative toward attacked traffic.
From the greater level, a DDoS attack is just like a congestion, which can prohibit the regular accessibility within the desired destination that seeks an attacker to have authority of the network of the machines over the web to perform an attack.
Computer systems and various other machines (like IoT devices) are thrushed with malwares, making over each one into a zombie or bot. The attacking host has the overall control over the group of zombies or bots, which is termed as botnet. Once a botnet has been set up, the attacking agent is capable of directing the machines by passing the latest instruction to each bot directed by a method similar to that of a remote control. At the same time, if the IP address of a victim is on target reflected by the botnet, each bot will reciprocate by prolifering the requests to the targets, thereby causing the target server to potentially overflow requests to the targets, leading denial of service to normal traffic. This is all because each particular bot is a legitimate internet instrument in which disintegrating attack traffic from normal traffic becomes difficult approach [27].
Читать дальше















