L.S. Wijesinghe, L.N.B. De Silva, G.T.A. Abhayaratne, P. Krithika, S.M.D.R. Priyashan, and Dhishan Dhammearatchi (2016) in their research paper mainly focus on how to combat cybercrimes, and also throw some light on how intelligent and effective the tool “agent” can be used in the detection and prevention of cyber-attacks. Cyber-attacks tend to have a huge impact on the IT industry when it comes to data theft, the data has become more vulnerable and prone to such threats and attacks due to the malicious activities going on for the agendas best known to the attackers.
Ramamoorthy R. (2010) in his paper discusses the various perspectives of cyber security. Because of ontinuously evolving new threats against enterprises, IT has made cyber security a “must look-into” issue. The systems administration team should devise ways to improve their cyber security with an automated, on-demand, real-time application security testing solution that makes comprehensive cyber security for applications simpler and more cost effective. Cyber security knows no borders. The author touches upon controlling server sprawl to increase operational efficiency and ease disaster recovery, virtualization clearly delivers end results.
Yasmin N., and Bajaj N. (2012) in their research paper present S-box Modification in DES. DES is Data Encryption Standards and S-box “substitution box” – a standard encryption device. Security is the main concern for organizations participating in information exchange. One of the essential aspects for secure communications is that of cryptography. As cybercrimes are causing serious financial losses, an existing system needs constant modifications to ensure that security levels are not compromised. It shows a higher degree of resistance against attack on relationship L i+1= R i. But a significant amount of mathematical knowledge and understanding the complete crypto system is required.
Cyber-attacks are expanding quickly, notwithstanding increased security measures. The attacks may be a malware, phishing attack, password theft, Trojan attacks, and so on. In order to avoid these cybercrimes robust cyber-security measures are needed. Emerging technologies like cognitive science, cloud computing, robotics, internet banking, and e-commerce urgently need to put in adequate safeguard measures in the domain of cyber security. With increasing use of Big Data, governing the decision-making by use of machine learning models, cyber security needs to be at the helm [10, 11].
The model proposes to add a layer of security to the multi-layered security approach. The proposed system architecture describe in Figure 1.2.
1 Suppose, while we are trying to log into our bank account using our credentials, a bot tries to crack the captcha.
2 Whenever it does so a machine learning model based on its ability to recognize patterns from the past would detect the presence of bots through active monitoring and predictive analysis.
3 If detected, it would terminate the current process and send out an alert.
4 If the bot is not present then it would continue the process and run the anti-virus software, in order to remove any other malicious files.
5 The Disaster recovery plan in the end would ensure that any important data is not lost and is backed up.
1.5.1 System Architecture
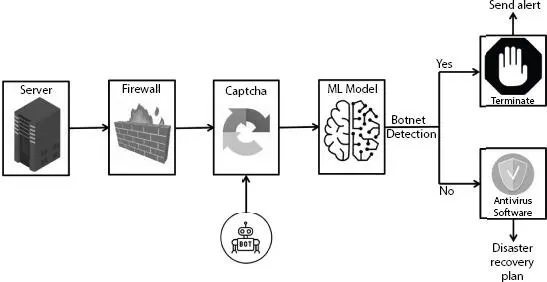
Figure 1.2 System architecture [11].
While we are embracing new ways of digital interaction and more of our critical infrastructure is going digital, the parameters of the transformation underway are not understood by most of us. A better understanding of the global cyberspace architecture is required.
AI finds its applications in almost every field of science and engineering. AI models need precise safeguards in digital security and new technologies to battle antagonistic machine learning, retain confidentiality, and secure organized learning, and so on. In this chapter, the authors examined specific approaches in AI that are promising and proposed a system of preventing certain types of cyber-security attacks.
1. Alex Roney Mathew, Aayad Al Hajj, Khalil Al Ruqeishi (2010), Cyber Crimes: Threats and Protection, International Conference on Networking and Information Technology, Manila.
2. Cerli and D. Ramamoorthy (2015), Intrusion Detection System by Combining Fuzzy Logic with Genetic Algorithm, Global Journal of Pure and Applied Mathematics (GJPAM) , vol. 11, no. 1.
3. L.S. Wijesinghe, L.N.B. De Silva, G.T.A. Abhayaratne, P. Krithika, S.M.D.R. Priyashan, DhishanDhammearatchi (2016), Combating Cyber Using Artificial Intelligence System, International Journal of Scientific and Research Publications , vol. 6, no. 4.
4. Naveen Kumar, Prakarti Triwedi, Pramod Singh Rathore, “An Adaptive Approach for image adaptive watermarking using Elliptical curve cryptography (ECC)”, First International Conference on Information Technology and Knowledge Management pp. 89–92, ISSN 2300-5963 ACSIS, Vol. 14 DOI: 10.15439/2018KM19
5. Pramod Singh Rathore, “An adaptive method for Edge Preserving Denoising,” International Conference on Communication and Electronics Systems, Institute of Electrical and Electronics Engineers & PPG Institute of Technology (2017). Proceedings of the 2nd International Conference on Communication and Electronics Systems (ICCES 2017) : 19-20 October, 2017.
6. R. Hill (2010), Dealing with cyber security threats: International cooperation, ITU, and WCIT, 7th International Conference on Cyber Conflict: Architectures in Cyberspace.
7. Onashoga, S. Adebukola, Ajayi, O. Bamidele and A. Taofik (2013), “A Simulated Multiagent-Based Architecture for Intrusion Detection System”, (IJARAI) International Journal of Advanced Research in Artificial Intelligence , vol. 2, no. 4.
8. S. Dilek, H. Çakır and M. Aydın (2015), Application of Artificial Intelligence Techniques to Combating Cyber Crimes: A Review, International Journal of Artificial Intelligence & Applications (IJAIA) , vol. 6, no. 1.
9. S. Singh and S. Silakari (2009), A Survey of Cyber Attack Detection Systems, IJCSNS International Journal of Computer Science and Network Security , vol. 9, no. 5
10. Singh Rathore, P., Kumar, A., & Gracia-Diaz, V. (2020). A Holistic Methodology for Improved RFID Network Lifetime by Advanced Cluster Head Selection using Dragonfly Algorithm. International Journal of Interactive Multimedia and Artificial Intelligence, 6 (Regular Issue), 8. http://doi.org/10.9781/ijimai.2020.05.003
11. Dr. Ritu Bhargava, Pramod Singh Rathore, Rameshwar Sangwa, February 18 Volume 4 Issue 2, “An Contemplated Approach for Criminality Data using Mining Algorithm”, International Journal on Future Revolution in Computer Science & Communication Engineering (IJFRSCE) , pp. 236–240.
1 *Corresponding author: siroyanavani@gmail.com
2
Privacy Preserving Using Data Mining
Chitra Jalota* and Dr. Rashmi Agrawal
Manav Rachna International Institute of Research and Studies, Faridabad, India
Abstract
On the one hand, data mining techniques are useful to extract hidden knowledge from a large pool of data but on the other hand a number of privacy threats can be introduced by these techniques. The main aim of this chapter is to discuss a few of these issues along with a comprehensive discussion on various data mining techniques and their applications for providing security. An effective classification technique is helpful to categorize the users as normal users or criminals on the basis of the actions which they perform on social networks. It guides users to distinguish among a normal website and a phishing website. It is the task of a classification technique to always alert users from implementing malicious codes by labelling them as malicious. Intrusion detection is the most important application of data mining by applying different data mining techniques to detect it effectively and report the same in actual time so that essential and required arrangements can be made to stop the efforts made by the trespasser.
Читать дальше













