Risk analysis should always begin with a vulnerability assessment (discussed in Chapter 6, “Security Assessment and Testing”) and a threat analysis (discussed in the section “Understand and Apply Threat Modeling Concepts and Methodologies” later in this chapter). This stage of risk assessment is focused on evaluating the likelihood of identified threats exploiting weaknesses (i.e., vulnerabilities) in your environment and determining the impact to your assets if that happens. Likelihood describes the probability that an event will occur, and impact defines how disastrous the event would be if it were to happen.
Likelihood can be identified by evaluating each threat and assessing the probability that the threats might actually exploit a vulnerability, or weakness. For example, you might determine that the risk associated with a destructive fire is relatively low if you have redundant fire suppression systems that are tested monthly; if you have mechanisms in place to detect and extinguish fires and if you are testing those mechanisms regularly, then the likelihood, or probability, of a fire destroying everything is reduced. Similarly, you might identify insider threat as high likelihood if you've contracted with a large organization without conducting thorough background checks — in this situation, there is a greater probability that something bad will happen.
Impact can be identified by establishing the value associated with each potentially affected asset and determining how that value will be destroyed or otherwise affected by an adverse event. An asset's value can be both quantitative (i.e., determined by its cost or market value) or qualitative (i.e., determined by its relative importance to you or your organization). By establishing an asset's value, you can better determine the impact of that asset's security being compromised — this allows informed decision-making when determining how much to spend on safeguarding a given resource, as you never want to spend more protecting an asset than the asset itself is worth.
 Quantitative Risk Calculation
Quantitative Risk Calculation
Risk analysis can be either qualitative or quantitative (or a combination of the two). Qualitative risk analysis avoids the use of numbers and tends to be more subjective. Quantitative risk analysis is far more precise and objective, because it uses verifiable data to analyze the impact and likelihood of each risk. Quantitative risk calculation involves making measurements to mathematically determine probability (likelihood) and impact. Qualitative risk analysis involves assigning less precise values (like critical, high, medium, and low) to likelihood and impact.
While some risks can be hard to quantify, keep in mind that qualitative analysis can often be vague, imprecise, and even misleading. For example, pandemics were a pretty “low” probability of occurrence prior to 2019, but COVID-19 demonstrated that the overall risk associated with pandemics could be very high.
One important concept in quantitative risk analysis is annualized loss expectancy (ALE), which is a metric that helps quantify the impact of a realized threat on your organization's assets. ALE is measured in dollars and is the product of single loss expectancy (SLE) and annual rate of occurrence (ARO), which are each discussed here:
SLE is a measure of the monetary loss (calculated in dollars) you would expect from a single adverse event. In other words, SLE estimates how much you would lose from one occurrence of a particular realized threat. SLE is calculated by multiplying an asset's value (AV) by its exposure factor (EF). EF is the estimated percentage of loss to a specific asset if a specific threat is realized.
ARO is the estimated annual frequency of occurrence for a given adverse event. In other words, ARO is the number of times that you expect a particular risk event to occur every year.
Here are the two formulas to keep in mind:

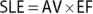
During risk evaluation, you compare the results of your risk analysis to your organization's established risk profile or risk tolerance (i.e., how much risk your organization is willing to take on). In doing so, you are able to determine the best course of action for each of your identified risks. We cover the various options for risk response in the following section.
Once you identify and assess your organization's threats, vulnerabilities, and risks, you must determine the best way to address each risk; this is known as risk treatment (or risk response ). There are four main categories of risk treatment, as we describe in the following sections: avoid, mitigate, transfer, and accept. Each of these are ultimately leadership/management decisions that should have CISSP input and awareness.
Risk avoidance involves eliminating an identified risk by stopping or removing the activity or technology that causes the risk in the first place. Organizations use risk avoidance when a particular risk exceeds their acceptable risk tolerance, but complete avoidance is often difficult to achieve without business disruption. While this type of risk treatment can often mean simply not doing something, policies that ban the use of removable media or personal cloud storage services are avoidance steps that require upfront investment and action.
Risk mitigation (sometimes called risk reduction or risk modification ) is a strategy that involves reducing the likelihood of a threat being realized or lessening the impact that the realized threat would have on the organization. Risk mitigation is the most common treatment option for identified risks and involves implementing policies and technologies to reduce the harm that a risk might cause. Moving from single-factor to mutifactor authentication is an example of a mitigation treatment for sensitive data access.
Risk transference (also known as risk assignment ) involves shifting the responsibility and potential loss associated with a risk onto a third party. Insurance is the most common form of risk transference. For example, if a company loses customer data due to a cyber breach, the company may rely on their cyber insurance to cover any monetary losses associated with the breach. In this case, the breached organization has transferred financial risk to their cyber insurer, but the company still must manage through some level of reputational risk. It's hard to completely transfer all risk, so many people instead use the term risk sharing . Using cloud-based services or managed security services is a great example, because risk is split between you, as the customer, and the third-party provider.
Risk acceptance unsurprisingly involves accepting the risk associated with a particular threat. Risk acceptance is the way to go if avoiding, mitigating, or transferring the risk would cost more than the expected losses of the realized threat. In theory, a risk should be accepted only if it is completely within an organization's risk tolerance. In practice, organizations are often forced to accept potentially painful risks associated with normal business operations.
Читать дальше

 Quantitative Risk Calculation
Quantitative Risk Calculation