TIPIt is not unusual for individuals to have taken steps to harm the organization in the event that they were terminated. The most obvious forms of this are the theft of data by the terminated individual, who hopes to sell back the key to the organization (i.e., ransomware), use the information to begin or join a competing organization, or disclose the information to discredit the organization. Strong data security practices and a well-developed insider threat program are essential in defeating malicious activities by terminated employees. User and Entity Behavior Analytics (UEBA), for example, can help detect a disgruntled employee who is heading toward a rage quit.
Vendor, Consultant, and Contractor Agreements and Controls
Many organizations require expertise or talent that does not exist inside their organizations. These relationships may exist for goods or services, but both types of acquisition open the organization to risk. Information security policies should be in place to ensure that these relationships do not expose the organization's sensitive information to an unreasonable amount of risk. NDAs and other employment agreement policies play a big part in establishing expectations with third parties and can lead to additional compliance burden on the organization who must enforce them.
Compliance Policy Requirements
Responsibilities for compliance with applicable policies and regulations should be clearly documented and understood by all employees within an organization. In many cases, employees may be required to sign an attestation stating that they have reviewed and agree to comply with all company policies and applicable regulations.
Employees and other parties with access to systems and information must undergo initial and periodic training that includes security awareness and job-based training. Generally, annual recertification is a good way to ensure that all parties with access remain in compliance with employment policies.
Privacy Policy Requirements
Your organization's privacy policy is an explanation of your company's personal data collection and use practices. Privacy policies should link back to applicable privacy laws and regulations, such as HIPAA in the United States and GDPR (discussed later in this chapter) for companies that handle EU residents' information.
Your privacy policy should explain what kind of personal data is collected, how your organization will or won't use it, and how the personal data will be stored, maintained, and secured. The privacy policy should be made available to all personnel, and many organizations require a signed acknowledgment from each employee.
UNDERSTAND AND APPLY RISK MANAGEMENT CONCEPTS
The topic of risk management, and all the concepts within it, is at the heart of information security and is the core of every strong information security program. Risk management includes all the processes associated with identifying threats and vulnerabilities and quantifying and addressing the risk associated with those threats and vulnerabilities. Risk management processes provide a structured method for making security decisions such as purchasing and implementing security tools and hiring people. This section covers the key concepts behind risk management and guides you through applying these concepts in your organization.
Identify Threats and Vulnerabilities
In security, a risk is the potential for negative impact on the organization, its goals or objectives, or its assets (including people, systems, and data) due to a threat exploiting a vulnerability. You should note that there are dozens of definitions for each of these terms (i.e., risk, threat, and vulnerability) across different industries. We'll discuss these terms further, but it's important to understand that risk lies at the intersection of the three components shown in Figure 1.5.
NOTEThere are two classifications of risk that you should be familiar with: inherent risk and residual risk. Simply put, inherent risk is the risk present before any controls are applied, while residual risk is the level of risk that remains after controls are in place. The concept of security controls is discussed later in this chapter.
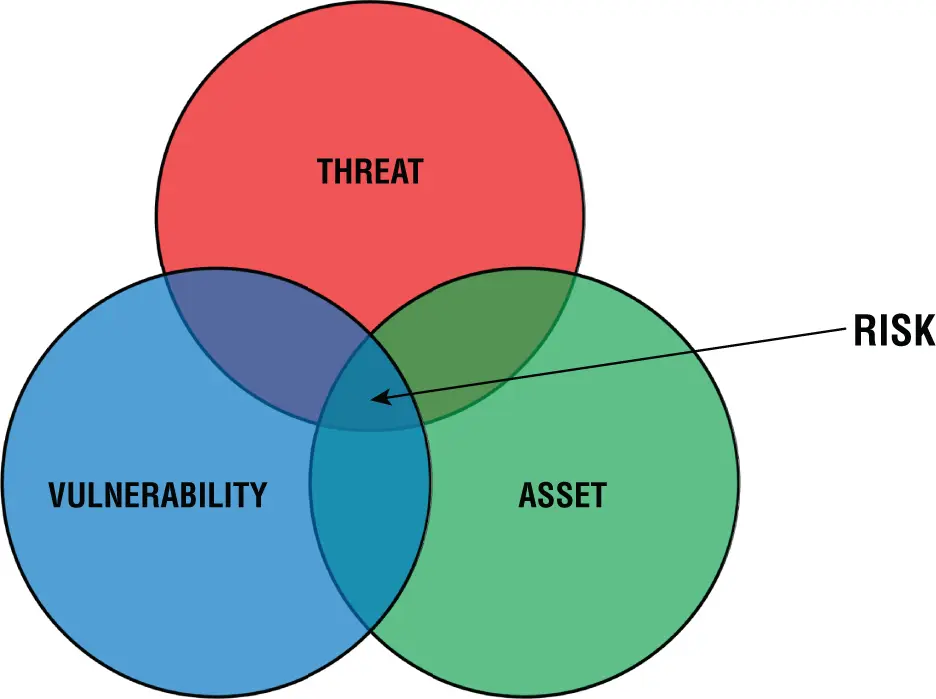
FIGURE 1.5 Relationship between threats, vulnerabilities, assets, and risks
A threat is a negative event that can lead to an undesired outcome, such as damage to, or loss of, an asset. A threat is posed by a threat actor , which is a person or entity that is capable of intentionally or accidentally compromising an asset's security. As security professionals, threats are the people and events that we work to protect our information and systems from.
Examples of security threats include the following:
A hacker who wants to encrypt your data and charge you a ransom for it
A disgruntled employee who wants to steal or sell corporate information
A fire or other natural disaster that may damage or destroy your datacenter
A vulnerability is a weakness or gap that exists within a system that may be exploited (by a threat actor) to compromise an asset's security or trigger a risk event. Vulnerabilities are the things within our systems that we try to fortify and improve.
Examples of security vulnerabilities include the following:
Unpatched software applications
Weak access control mechanisms (e.g., weak passwords)
Faulty fire suppression systems
An asset is anything of value, which may include people, property, and information. Assets are the things that we, as security professionals, are trying to protect. People assets may include your company's employees, contractors, and vendors, as well as your customers. Property assets include tangible things like servers and equipment, as well as intangible things like software code and other intellectual property.
Remember that risks are the intersection between threats, vulnerabilities, and assets, as shown in Figure 1.5. A risk assessment is the set of activities that involve identifying the threats and vulnerabilities that exist and determining the impact and likelihood of those threats exploiting the identified vulnerabilities.
There are numerous risk frameworks (as discussed in the “Risk Frameworks” section) that provide guidance on conducting risk assessments, but generally speaking, risk assessments include the steps shown in Figure 1.6.

FIGURE 1.6 Steps for assessing risk
NOTEThe NIST CSF and other modern risk frameworks are recognizing the need for the small to medium business (SMB) community to start with the first risk they identify and manage it, rather than going through the stepwise cycle in Figure 1.6. It's important that you consider your organization's resources and identify a risk management process that works for you.
The first step in a typical risk assessment process is to identify your assets and determine the value of those assets; this includes identifying and classifying your sensitive data, based on its sensitivity or value to your organization. During the risk identification phase, you find the systems, applications, and information that need protecting and then identify and describe the vulnerabilities and threats that pose a risk to each of those assets.
Читать дальше














