Perry Carpenter - The Security Culture Playbook
Здесь есть возможность читать онлайн «Perry Carpenter - The Security Culture Playbook» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:The Security Culture Playbook
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:4 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 80
- 1
- 2
- 3
- 4
- 5
The Security Culture Playbook: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «The Security Culture Playbook»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
The Security Culture Playbook
really
The Security Culture Playbook
The Security Culture Playbook — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «The Security Culture Playbook», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
Much of the cybersecurity narrative revolves around technology. We talk about firewalls being bypassed, data being leaked, or servers being hacked; we show images of cybercriminals in dark rooms surrounded by screens filled with indecipherable computer code. When that's the picture of cybersecurity that our people get, it is very easy for them to feel overwhelmed. Making human-layer vulnerabilities and defenses a frequent and explicit part of your organization's cybersecurity conversations paves the way for more human-centric policies, processes, and technologies.
By consistently referring to the importance of the human layer, you can reinforce the need to engage people. It gives everyone the message that your people share a proactive role helping protect the organization. It opens up more meaningful conversations and helps pave the way to gain buy-in for initiatives that will help foster a stronger security culture.
What's the Cost of Not Getting This Right?
Organizations can't afford to neglect the importance of the human side of cybersecurity. As we mentioned in Chapter 1, organizations have been investing more and more each year trying to combat cybercrime and data breaches, and yet the breaches keep on coming. In fact, as we showed in Figure 1.1, the rise in breaches is outpacing the global spend on cybersecurity “solutions.” Why is that spend not paying off? The reason becomes clear when you look at where the security spend is going.
Figure 2.1illustrates the problem well. We know that 85 percent of data breaches are being caused by social engineering or human error (Verizon, 2021). But, when you look at organizational spending on security, it becomes clear that leaders have been placing their faith (as reflected by spend) in the wrong areas. Organizations have been focusing on an outdated perimeter-based model of security—one that virtually ignores the human element or hopes that technology-based defenses will suddenly become effective at addressing social engineering and human error in a meaningful way.
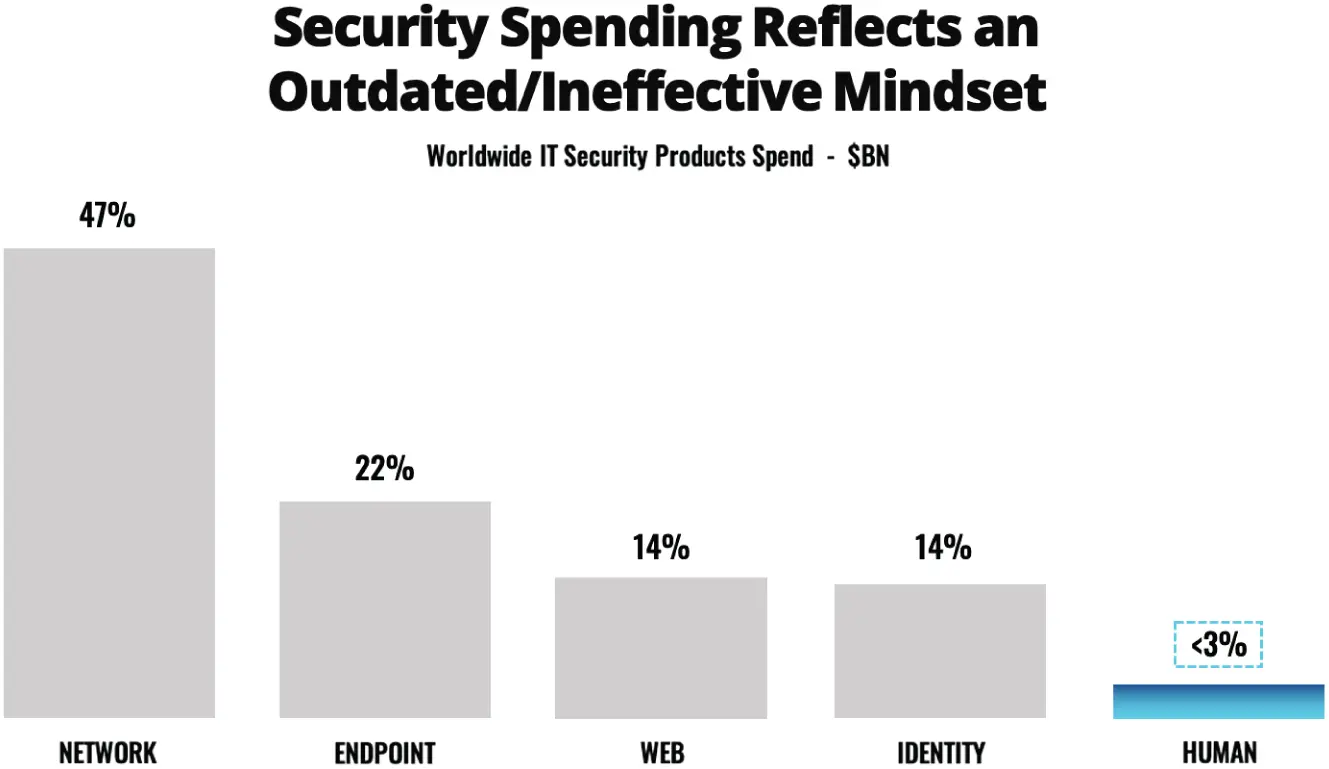
Figure 2.1Cybersecurity spending has effectively ignored the main cause of data breaches
Does the Breach Problem Mean Security Awareness Has Failed?
At this point, you might be thinking something like, “But I bet most of those organizations that were breached weren't totally ignoring the human side of things. Surely they were doing some form of awareness training. So what gives? Doesn't that mean that focusing on humans hasn't been effective?”
That's a great question.
The answer isn't that focusing on humans has been ineffective; what's ineffective are the traditional methods of security awareness and training. Traditional awareness programs focused on sending people information about current threats, security best practices, and policy expectations, and then simply expecting people to magically do the right thing. Every parent or teacher knows that simply exposing people to information and expectations doesn't change behavior, but somehow the security industry duped itself into believing that it would work for us. Obviously it hasn't.
The entirety of this book is about taking real control of your human-layer defenses. This will require you to expand your thinking about what security awareness training should look like.
We'll begin that journey in Chapter 3, “The Foundations of Transformation”!
Let's think about this for a minute. Less than 3 percent of security spending is focused on the human layer, but more than 85 percent of breaches are traced back to humans. That stark contrast between the problem area and where organizations are focusing is shocking.
Less than 3 percent of security spending is focused on the human layer, but more than 85 percent of breaches are traced back to humans.
For decades, security leaders have known that humans are the most enticing and vulnerable attack surface; nonetheless, we, as an industry, have tried everything but doing the actual work needed to improve our situation.
And here we are.
Cybercriminals Are Doubling Down on Their Attacks Against Your Employees
Over the past few years, we've seen a meteoric rise in attacks seeking to bypass technology by targeting humans. And it's working. Ransomware continues to make headlines due to large-scale attacks like those that targeted Colonial Pipeline (Fung, 2021), JBS Foods (Reuters, 2021), and Kaseya (Hill, 2021). The recent global pandemic only added fuel to the fire. All of a sudden, organizations and employees were having to adapt to a new normal: working from home. Organizations scrambled to find ways to allow employees to work remotely and safely.
The added confusion and chaos of a global pandemic, employees facing new routines and dealing with new systems, and people feeling more stressed and less connected than ever have all come together to create an enticing playground for social engineers. And they are taking advantage of it.
The added confusion and chaos of a global pandemic, employees facing new routines and dealing with new systems, and people feeling more stressed and less connected than ever have all come together to create an enticing playground for social engineers.
How Bad Is the Problem of Ransomware?
Cybersecurity Ventures recently published its forecast for the growth of ransomware over the next 10 years. It's not good. By 2031, “[r]ansomware is expected to attack a business, consumer, or device every 2 seconds […] up from every 11 seconds in 2021” (Braue, 2021).
Here are a just a few points to help put the problem into perspective (as of 2021):
Over one-third of organizations globally have been hit by ransomware (International Data Corporation, 2021).
Of those hit, roughly 87 percent ended up paying the ransom (International Data Corporation, 2021).
We are now at a point where ransomware isn't just about making your data inaccessible; it's about exfiltrating the data, using it for extortion against multiple parties, and generally doing everything possible to gain leverage and destabilize your organization. You have no choice but to assume that a ransomware incident is a data breach (Sjouwerman, 2021).
Social engineering via phishing, vishing (voice phishing), smishing (phishing via text message), and social media are all on the rise (Phishlabs, 2021; Martens, 2021).
The global average cost of a data breach is $4.24 million (IBM, 2021).
The global average cost of a ransomware attack is $4.62 million (IBM, 2021).
The average per-record cost of a data breach is $161. That goes up to $180 if the record contains customer personally identifiable information (PII) (IBM, 2021).
All of this rises to the level of materiality. And material risk is one of the most important things that an executive team and board of directors is concerned with. This is why it is so important to make your human layer of defense a central part of your cybersecurity narrative.
Your People and Security Culture Are at the Center of Everything
Your people are the most important element of your cybersecurity program; ignore them at your peril. Technology will only get you so far. So it's time to elevate human-layer defense to the forefront of the conversation. And it's time to deliberately and methodically focus on security culture.
Human knowledge, beliefs, values, behaviors, expectations, and social pressures are involved in everything that matters within your organization:
Читать дальшеИнтервал:
Закладка:
Похожие книги на «The Security Culture Playbook»
Представляем Вашему вниманию похожие книги на «The Security Culture Playbook» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «The Security Culture Playbook» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












