Perry Carpenter - The Security Culture Playbook
Здесь есть возможность читать онлайн «Perry Carpenter - The Security Culture Playbook» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:The Security Culture Playbook
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:4 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 80
- 1
- 2
- 3
- 4
- 5
The Security Culture Playbook: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «The Security Culture Playbook»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
The Security Culture Playbook
really
The Security Culture Playbook
The Security Culture Playbook — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «The Security Culture Playbook», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
Part 3: Transformation
Here is where the proverbial rubber meets the proverbial road. Part IIIis about doing the work. It's about transformation. We'll walk you through the Security Culture Framework, a process that Kai developed over 15 years ago for getting a handle on security culture so that it can be improved. Since its creation, this process has been adopted by organizations and governments around the world. And, because anything worth managing is worth measuring, we'll take a deep dive into how to scientifically measure security culture across seven dimensions, and we'll give an overview of the Security Culture Survey, a tool that Kai and his team created over a decade ago. Since that time, it's been honed into a finely tuned scientific instrument that's been used to collect and analyze the largest security-culture-related dataset on earth. We'll also discuss culture-related gotchas, sticking points, and more. In the last bit of Part III, you'll hear from a number of security experts as they discuss security culture, and we'll leave you with some valuable tools and insights that so you can immediately leverage everything from this book. You'll be able to discuss security culture with confidence, measure maturity, gain executive support, and more.
Reader Support for This Book
We've also created a resource site for this book where we'll upload new worksheets, research studies, and other useful security culture-related information. It's at SecurityCultureBook.com.
How to Contact the Publisher
If you believe you've found a mistake in this book, please bring it to our attention. At John Wiley & Sons, we understand how important it is to provide our customers with accurate content, but even with our best efforts an error may occur.
In order to submit your possible errata, please email it to our Customer Service Team at wileysupport@wiley.comwith the subject line “Possible Book Errata Submission”.
How to Contact the Authors
We appreciate your input and questions about this book! Connect with Perry or Kai on LinkedIn at www.linkedin.com/in/perrycarpenterand www.linkedin.com/in/kairoer.
Part I Foundation
Welcome to the journey! In Part I, we introduce the concept of security culture, why it is important, and (most importantly), the fact that you can measure and improve your culture. There's a lot to cover, so let's get started. But even before you turn to the first page of Chapter 1, we think it's important to give you a definition of security culture.
Security Culture: The ideas, customs, and social behaviors of a group that influence its security.
Chapter 1: You Are Here
Chapter 2: Up-leveling the Conversation: Security Culture Is a Board-level Concern
Chapter 3: The Foundations of Transformation
Chapter 1 You Are Here
The greatest danger in times of turbulence is not the turbulence—it is to act with yesterday's logic.
Peter Drucker
“Security culture” has become a hot topic of late. If you are a cybersecurity or business leader, you've no doubt seen the term appear in online articles, security presentations, and even a few vendor pitches. It's become a buzzword (or buzz phrase , if you want to be picky) du jour. Unfortunately, most of the time it is little more than a phrase uttered with gravitas, but devoid of real meaning.
Security culture is often confused with security awareness, the implementation of security processes, or even the use of security tools by end users. That initial misidentification becomes even more confusing because each of those things can feed into, or become an artifact of, security culture—but they are not in and of themselves security culture. Security culture is something different, something unique that is undeserving of the confusion that all too often surrounds it. And you know that; otherwise, you wouldn't be reading this book.
Our purpose here is to add precision and clarity to the topic. And, although we could easily fill several hundred pages with great content about security culture, that's not what this book is about. This book, dear reader, is a no-nonsense, (hopefully) no fluff, and (definitely) no BS guide to what security culture is, how to measure it, and how to shape and strengthen it within your organization.
Why All the Buzz?
For decades, security programs focused on diligently deploying technology-based defenses aimed at keeping cybercriminals at bay. The industry focused on firewalls, intrusion detection and prevention systems (IDSs/IPSs), endpoint protection platforms (EPPs), secure email gateways (SEGs), and more. In truth, the technology has gotten very good. Despite all the focus and spend on security tools, however, the data breach problem is not going away. In fact, it's accelerating faster than the industry can effectively manage via traditional approaches. Figure 1.1analyzes the amount of money spent on security products since 2007 versus the number of data breaches that occurred each year. The conclusion is clear: The current industry approach is not working.
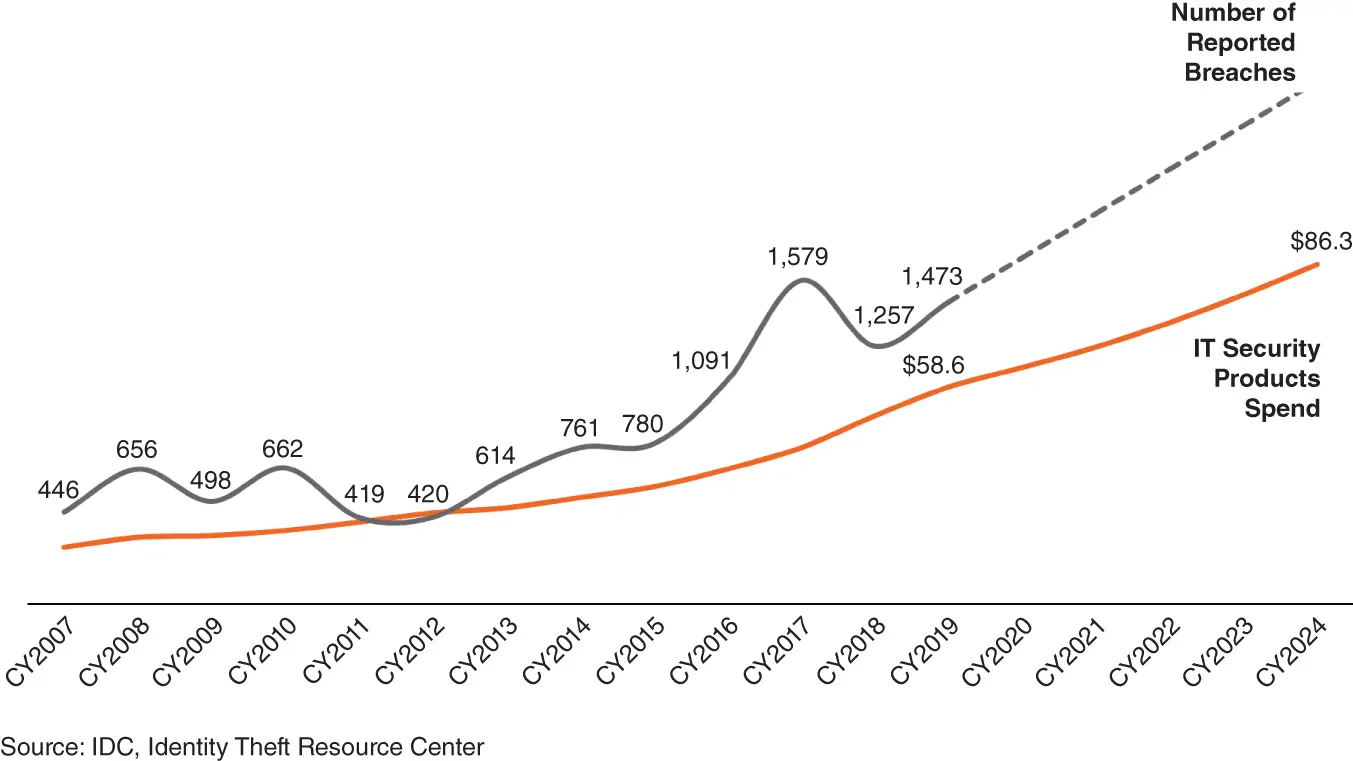
Figure 1.1Organizations globally have invested massively on cybersecurity, yet breaches continue to increase.
And here's where the buzz about security culture comes in. Leaders are realizing two things:
Technology-based defenses have gotten so good that attackers are being pushed to hack humans rather than spending weeks, months, or years researching and developing effective attacks to defeat technology-based defenses.
Humans are now the primary attack vector. As such, it's imperative to strengthen the human layer of security.
These two realizations (illustrated in Figure 1.2) have led to a growing interest in human layer defense. This isn't to replace any of the technology-based layers—those are still needed. But this is to strengthen a much-needed additional defensive layer.
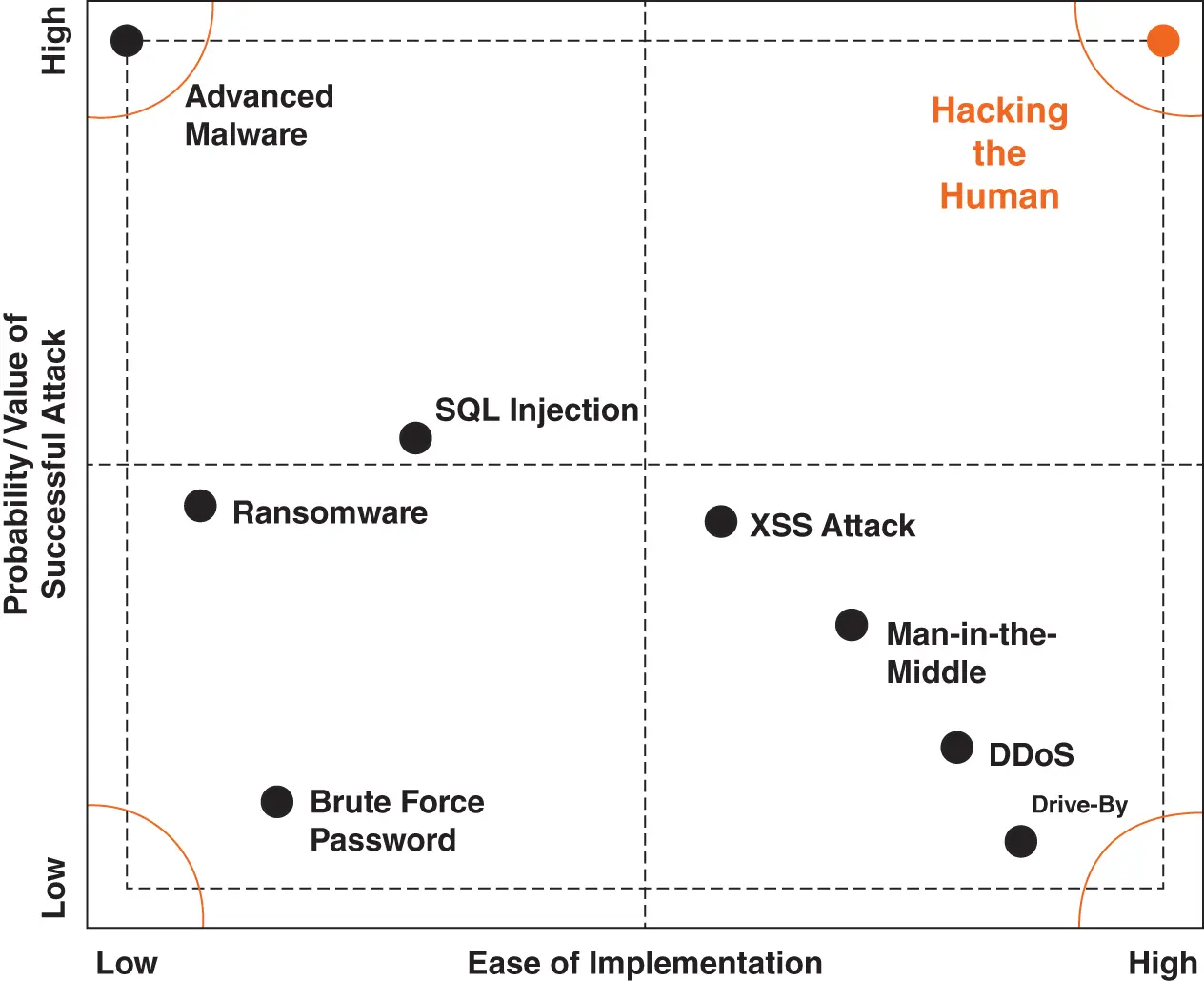
Figure 1.2Hacking the human yields the highest ROI for attackers.
The Technology-Based Defense vs. Human-Based Defense Debate: A False Dilemma
You've undoubtedly been presented with this dilemma before. Someone says that it's worthless to focus on the human side of security because, no matter what, there will always be someone who will fall for a phishing email or make some other error. In short, their argument is that the human defense isn't 100 percent effective, so it can't be relied on and doesn't deserve an investment of time, energy, or funding.
You'll even hear some make claims to the effect of, “only technology will help an organization prevent security issues.” This type of thinking has been prevalent in security circles for decades and has led to the situation that we're in right now, where the human layer has been neglected.
A quote from the preface of Bruce Schneier's book Secrets and Lies is fitting here. Bruce ends the preface with these words, “[a] few years ago I heard a quotation, and I am going to modify it here: If you think technology can solve your security problems, then you don't understand the problems and you don't understand the technology” (Schneier, 2000).
The following is an excerpt from Perry's book, Transformational Security Awareness: What Neuroscientists, Storytellers, and Marketers Can Teach Us About Driving Secure Behaviors (Carpenter, 2019). The excerpt does a good job summarizing why this is a false dichotomy. This shouldn't be presented as an either/or dilemma.
Читать дальшеИнтервал:
Закладка:
Похожие книги на «The Security Culture Playbook»
Представляем Вашему вниманию похожие книги на «The Security Culture Playbook» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «The Security Culture Playbook» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












