Cyber Security and Network Security
Здесь есть возможность читать онлайн «Cyber Security and Network Security» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Cyber Security and Network Security
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:3 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 60
- 1
- 2
- 3
- 4
- 5
Cyber Security and Network Security: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Cyber Security and Network Security»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
Written and edited by a team of experts in the field, this is the most comprehensive and up-to-date study of the practical applications of cyber security and network security for engineers, scientists, students, and other professionals.
Cyber Security and Network Security — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «Cyber Security and Network Security», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
1.4.4 Data at Transit and SSL
We have proposed to use TSL (Transport Layer Security), an updated and more secure version of SSL having advanced encryption algorithms integrated in it, giving extra security.
Nowadays, the encryption algorithms are all of single level encryption and hackers can easily hack the single level encryption so we propose to use multi-level encryption. First, we will encrypt the data using DES encryption technique on which we apply AES encryption technique giving a second level of encryption. Even by acquiring the data, decrypting such levels is a difficult task [14].
1.4.5 Data Encryption at Rest
To store big data files which have been uploaded by the client or organization in cloud for their use are stored, using several encryption algorithms like IDA (Information Dispersal Algorithm), SHA-512, and AES-256 (Advanced Encryption Standard) combinedly. This encrypted data is stored into Amazon S3 by splitting it into several parts. This encryption happens in server side, i.e., within the cloud. When any client or organization needing the data, it will undergo a decryption process, i.e., IDA is used to synchronize the encrypted data and it is reconverted into the initial data using AES-256 and SHA-512.
1.4.6 Centralized Ledger Database
After analysis of data, the JSON document is stored in QLDB. As the documents arrive, they will be stored in the journal one after another. If any document is changed, then a copy of it is maintained in a ledger called history. The rest remain in the current ledger. So, whatever data is in QLDB even if it gets deleted or updated is stored in the ledger and is easily viewable. For verifying data in QLDB, a SHA-256 secure hash file is generated from where the integrity of the data can be verified.
1.4.7 NoSQL Database
An encrypted JSON document will be stored in the hosted NoSQL database. The database would be encrypted at rest. While fetching data from the database, the files will be decrypted after checking the authorization details. After verifying the user to authorize or not, files can be updated from the database. In this way, data breaching can be avoided to a great extent.
1.4.8 Linux Instance and Server Side Installations
The server side application is developed using Python Django. Python version 3.x is recommended for development. Our application is developed using Python 3.8. The suggested required libraries and their versions are also provided in Table 1.1.
Table 1.1 Libraries and their versions
| Cryptography | Encryption (like AES) |
| Django-dynamodb-sessions | For NoSQL |
| Dynamodb-json | DynamoDB Json |
| Boto3 | AWS SDK for Python (Boto3) to create, configure, and manage AWS services |
The EC2 that was set up during testing was a T2 instance of the Micro specifications with 1.0 GiB RAM and 1vCPU. The application was set up in the Linux environment, and a startup script was put in place so that it would spin up the application whenever the instance starts. The application took in responses in a form of Rest API calls, and thus, the server provisioned is set up under a security group with network ingress egress allowed on Port 80.
For secure shell connectivity to the server for maintenance and optimizing and security purposes, the SSH port is kept open in the security group. This enables the administrator to connect to the server instances over the public internet securely. RSA keys are also advised to be used for encrypted secure login.
In a public cloud service, the servers and the security groups can be set up inside a virtual private cloud within public subnets facilitating public facing servers within a secure sandboxed environment so that the whole operation runs securely. Whole setup can also be done using integrated platforms (platform as a service) such as infrastructure as a code such as cloud formation services. Figure 1.2shows home or my profile page from manager’s point of view.
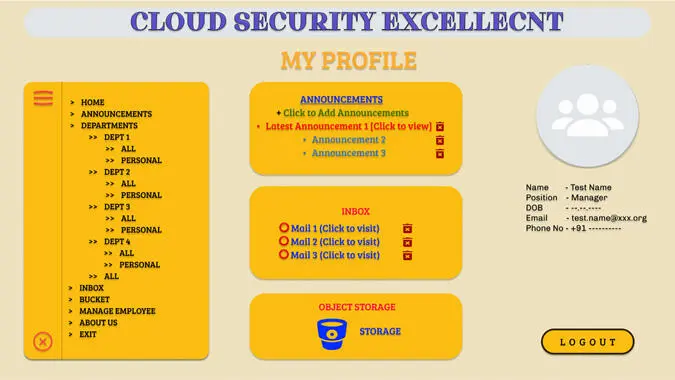
Figure 1.2 Home or my profile page from manager’s point of view.
In our proposed model, the managerial role in the organization is the administrator of the system suggested. The name of the roles in our proposed model may vary and can be changed according to the enterprise specifications, but the logic behind the operations is suggested to be kept the same. The manager has the highest access privilege than the other users in the system. Here, he/she can control document transactions and user managements monitoring and tracking the access granted to the respected users. From the Profile page of the manager, he/she can create or delete (CRUD) any announcements, and small synopsis of unread or latest communications are also viewed in the home page.
The data of the announcement, or the communications that are being sent, are sent in the JSON format by the client machines which are encrypted using DES encryption first and then AES over it. After going through the public internet and reaching the server endpoint, the encrypted data packet is decrypted. Further, the data is analyzed for infections or malware. If the data is found to be free of such things, then the JSON data is analyzed. If the content key in it contains the value “announcement”, then the data within is saved in the Announcement Table in the NoSQL database. Here, in our proposed model, we use DynamoDB because of its high scalability, serverless structure, and single-digit millisecond latency. Similarly, the “communications” would be saved over in the Communications table in the same database.
The proposed Json file structure would be like the following:
{
content: “announcement”,
data: [‘this is an array of string and objects’],
data-type: ‘text/html’
}
After clicking on the Logout button, the users are disconnected from the server and sent back to the Login page. No further actions can be carried out by that particular user’s identity unless he or she logs back in. Figure 1.3shows home or my dashboard page from employee point of view.
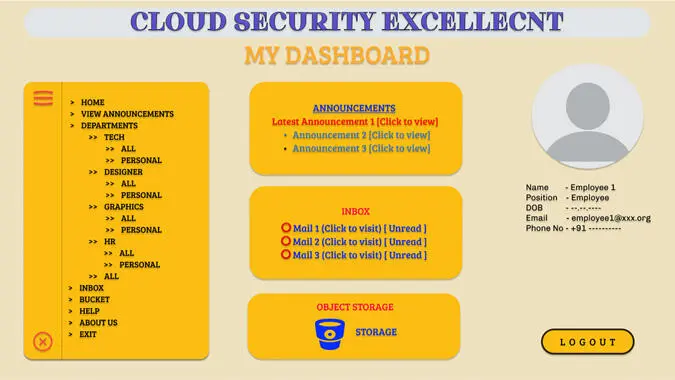
Figure 1.3 Home or my dashboard page from employee point of view.
Here, it shows the profile of the employee in the organization from where he/she can view the profile, get necessary updates (i.e., from Announcements, Inbox), and perform the job. From the Home or My Dashboard page, employees see the announcements, small synopsis of unread or latest mail. On clicking over the object storage, it will be redirected to storage or bucket page. From the navigation dashboard, employees can go to any page (only eligible pages) according to their choice. Apart from all these, users can also logout from the page by clicking on the Logout button at bottom right of the page. For the users to store object-based files, the users are authenticated and the client side of the software verifies the file and compresses it after encrypting. Here, we use double layer security, i.e., for the first layer we have used the DES encryption, over that a second layer of encryption, i.e., AES is applied over it. Further, encrypted compressed objects are sent over the public internet and are in a S3 bucket through the REST API that is put in place. After a new object is created over in the primary S3 Bucket, a serverless lambda function gets invoked and the encrypted compressed file is decompressed and decrypted accordingly. Further, after a series of actions verifying the authenticity of the file sent, the file is compressed and stored in another S3 Bucket from where it would be retrieved when required. A life cycle policy is put in place where the older objects which are not required frequently are transferred to an economical tier, and the other much older objects are transferred over to glacier object storages for archival purposes. Figure 1.4shows inbox page from manager’s point of view.
Читать дальшеИнтервал:
Закладка:
Похожие книги на «Cyber Security and Network Security»
Представляем Вашему вниманию похожие книги на «Cyber Security and Network Security» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «Cyber Security and Network Security» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












