Because of the achievement of customer organizational systems and the need to help hearty and scalable back-end networks, IoT operational frameworks must use strong advancement (DevOps) strategies and tools. DevOps blends sprint improvement work on Scrum or Kanban with a sharp understanding of events as an oversimplified term.
3.9 IoT Security Innovation Cryptographic Basics
The key subject of this chapter is IoT implementers: people who create or integrate IoT (consumer or industry) goods in their enterprises. It provides a context for the development of cryptographical protection for IoT implementations [21]. This aspect diverges somewhat from deeper themes of history in applied cryptography and encryption, while the rest of this book is committed to realistic application and advice. This knowledge may be common sense to some professionals, but even security-conscious systems have acknowledged that these backgrounds are important in terms of the many cryptographic and deployment insecurities that still happen today. The risks are compounded by the fact that various businesses who are traditionally ignorant of safety (such as home appliance suppliers) begin to connect themselves to the network and find it necessary to link their goods to IoT. In the meantime, they make some preventable mistakes that may harm their clients [22].
3.10 Cryptographic Primitive Forms and Implementations in the IoT
An interesting aspect of the IoT is the exponential growth of the seller’s goods as an operating charge that buyers often compensate for such rights (for instance, as in exorbitant clinical imaging frameworks). It explains how IoT equipment is leased to consumers following the way it is used for charging purposes [23].
Multiple IoT system forms are ordered from customers and then identified with the vendor’s cloud base to track their design development products just as the record changes are. Such products are out of the third-birthday festivity ODM that plays with the IoT framework some of the time. At that point, the OEM contains such operation when cryptography is considered by a huge number of people, it’s encryption that a lot of the bells ring. They understand that even if it were, information must remain “mixed” with the objective so unauthorized actors would not unravel and decipher it. Various distinct natives are included in true cryptography, whether they represent one of the previous IA destinations to a significant or complete degree. Technology experts experienced in advanced cryptography and convention preparation may only perform or track a stable update and connect cryptographic natives to accomplish a wider, more complicated security target. Indeed, even the smallest mistake can preclude the achievement of the security objective(s) and cause costly vulnerabilities [24]. There are other options to ruin the use of cryptography than to gain ownership of the business.
Just as in in any situation, cryptography is used in detachment. Instead, it includes critical protection capabilities utilized in communications at high levels and in different conferences. Bluetooth, ZigBee, SSL/TLS, and a host of conventions, for example, show basic cryptographic natives and techniques for including communications, message decoding, and traditional actions (for instance, how to deal with a bombed message uprightness check) [25].
Conditional claims occur between the two entities within the framework of the supplier’s agreement (MSA). Also, certain carriers will offer subordinate administrations that may be linked to their IoT gadget administration, in any case, when completed in the purchaser scenario. The use of solid improvement task (DevOps) strategies and time is vital for IoT organizational structures, considering the achievement of customer operating frameworks as well as the need to encourage vigorous and flexible back-end foundations. DevOps, as an oversimplified term, combines an ordered enhancement feature on Scrum or Kanban with a keen knowledge of tasks.
3.11 Encryption and Decryption
Encryption is the most widely recognized encryption service since it is used for encrypting or disguising data for unintended parties not to read or display [26]. In other terms, it is used to secure the secrecy of eavesdroppers’ knowledge and to enable only the expected parties to decode it as shown in Figure 3.2.
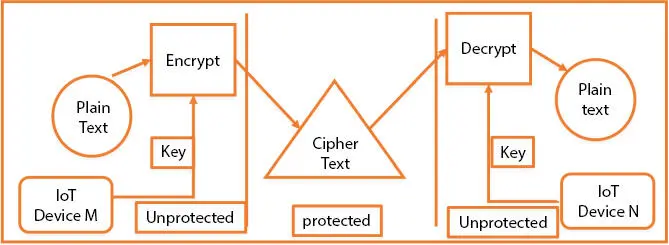
Figure 3.2 Encryption and decryption process.
Algorithms may be used for symmetric or asymmetric encryption. The cryptographic key and vulnerable details that cipher the encryption algorithm are always given. Information is safe until it is in this state from eavesdroppers. The receiver requires a key to decode the details it gets. Vulnerable data is referred to as plain text and ciphertext is considered protected details. The above scenario indicates that the listener is at risk if the information is decrypted before IoT Device B. This raises the question of the ability of the AR endpoints somewhere in the touch stack and the entire encoding. System security engineering will pre-scan for point-topoint codes and end-to-end encodes communication functionality in its vulnerability models. This could be the wrong environment, since most encrypted protocols only work point-to-point, allowing gateway spreading and the managing of several intermediate structures that can be extremely dangerous [27].
End-to-end decoding at session and device layers is more distinguished in the existing web consistency context due to large information losses until cycles are decrypted by the mediator. The case in point is the electrical industry as well as its systematic usage of insecure SCADA protocols. The installation of secure communication gates is normally needed for security updates (where recently extra encoding is performed). Another secure end-to-end method requires the tunnelling of dangerous protocols [28]. Device protection implementations can specifically clarify for and encode security protocols in use where plain text data is stored (in storage or transit) and where it needs to be re-encoded (encrypted) to cypher text. End-to-end cryptography can usually be supported as far as possible. In other words, it must always be assisted to adopt a stable by default role.
A. Symmetric Encryption
Symmetric encryption clearly means the use of a cryptographic key by the sender and recipient (unscrambled). Depending on the mode, the calculation that can be decrypted and encrypted is reversible according to the diagram:
As shown in Figure 3.3, an alternate symmetric key is used in different conventions for any movement leading. For example, Machine A will encode Device B along these lines using the X key.
Notwithstanding the cryptographic key and the data taken care of by the figure, modes outside a single figure are essentially different strategies for bootstrapping a figure to run on progressive parts (obstructions) of plain text and figure material information. The ECB (Electronic Code Book) is a basic figure that works all at once on a single square of a plain text or a figure article. Despite the likelihood that refurbished squares of indistinguishable plain text will have an indistinguishable figure material layout, the ECB mode figure without anyone else is used once and a while, rendering blurred data powerless for a disastrous traffic inquiry. In ECB mode, no IV is fundamental, just the symmetric key and the information to be included. Square figures can be used in square tie modes and current/counter modes of the previous ECB, which have been tested immediately.
Читать дальше













