(2.7) 
where 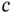 is the propagation speed, equal to the speed of light. We can soften the propagation assumption and enrich our collision model by assuming the following: the communication range is
is the propagation speed, equal to the speed of light. We can soften the propagation assumption and enrich our collision model by assuming the following: the communication range is 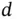 , but the range within which the carrier can be sensed, called the sensing range, is larger, say
, but the range within which the carrier can be sensed, called the sensing range, is larger, say 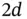 . The rationale can be drawn from the analogy with speech: as Yoshi goes away from Zoya, after some distance he can hear that she is speaking, but cannot understand the words. If Zoya and Yoshi are terminals that are situated at the opposite ends of Basil's cell, then the distance between them is
. The rationale can be drawn from the analogy with speech: as Yoshi goes away from Zoya, after some distance he can hear that she is speaking, but cannot understand the words. If Zoya and Yoshi are terminals that are situated at the opposite ends of Basil's cell, then the distance between them is 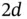 and the duration of the minislot should be chosen to be
and the duration of the minislot should be chosen to be 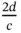 . In practice, it gets more complicated as not all signals travel over a straight line, as some of the waves that carry wireless information are reflected and arrive later.
. In practice, it gets more complicated as not all signals travel over a straight line, as some of the waves that carry wireless information are reflected and arrive later.
We remark that carrier sensing is well suited for ALOHA type protocols, where collisions are avoided. On the other hand, the random access protocols based on splitting tree are good at resolving collisions once they occur, such that the gains that CSMA introduces in splitting tree type protocols are rather modest, as the main effect of CSMA is to decrease the probability of occurrence of a collision.
2.3.3 Feedback to the Transmitter
The way we have described the system operation in Figure 2.4assumes that a transmitter, Zoya or Xia, knows perfectly if their packet has been received successfully or was subject to collision. On the other hand, collision or success is a phenomenon that occurs at the receiver, such that it is the receiver that needs to inform the transmitter about the outcome. In addition, Zoya's transmitter is half-duplex and she cannot detect the collision with Xia while transmitting, although Xia is within the communication/interfering range and her signal reaches Zoya. In fact, due to the use of half-duplex transmission, after sending the packet, Zoya should go into receiving mode. In this mode she waits for a packet from Yoshi that carries feedback to inform her whether the packet reception outcome was successful or not. This feedback packet from Yoshi, denoted by 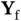 , can, in principle, carry a single bit of information, either acknowledging (ACK) the packet reception or sending a negative ACK (NACK). The latter is sent in the case there is a collision and thus an incorrect reception. The feedback packet is, generally, much shorter than the data packet.
, can, in principle, carry a single bit of information, either acknowledging (ACK) the packet reception or sending a negative ACK (NACK). The latter is sent in the case there is a collision and thus an incorrect reception. The feedback packet is, generally, much shorter than the data packet.
Figure 2.5(a)shows the transmission of the feedback packet 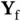 from Yoshi for the case when the channel is slotted. Differently from the slotted model used before, where the slot duration was equal to the packet duration, here the slot duration is longer than the duration of Zoya's packet. The remainder of the slot, after the end of Zoya's packet, is reserved for Yoshi to transmit the ACK message
from Yoshi for the case when the channel is slotted. Differently from the slotted model used before, where the slot duration was equal to the packet duration, here the slot duration is longer than the duration of Zoya's packet. The remainder of the slot, after the end of Zoya's packet, is reserved for Yoshi to transmit the ACK message 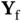 , while Zoya is in a listening mode. Referring to Figure 2.4(a), Yoshi receives
, while Zoya is in a listening mode. Referring to Figure 2.4(a), Yoshi receives 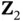 successfully and sends
successfully and sends  ACK. The packet
ACK. The packet 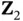 is not received correctly and Yoshi sends
is not received correctly and Yoshi sends 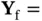 NACK. If we assume that all nodes are in each other's communication range, then at the same time when Walt sends NACK to Xia, collision occurs at the receiver of Zoya, as well as that of Xia. As a result, Zoya does not receive the NACK. To avoid this type of situation, one can use randomized contention for sending the feedback packets, which is a contention that occurs in addition to the contention used for data packets. Nevertheless, in our communication model, Zoya can receive NACK also implicitly , through the absence of ACK. In other words, the mere existence or absence of
NACK. If we assume that all nodes are in each other's communication range, then at the same time when Walt sends NACK to Xia, collision occurs at the receiver of Zoya, as well as that of Xia. As a result, Zoya does not receive the NACK. To avoid this type of situation, one can use randomized contention for sending the feedback packets, which is a contention that occurs in addition to the contention used for data packets. Nevertheless, in our communication model, Zoya can receive NACK also implicitly , through the absence of ACK. In other words, the mere existence or absence of 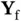 can be understood as a single bit of information sent from Yoshi to Zoya. If Yoshi does not receive the data packet correctly, he “sends” NACK by not transmitting
can be understood as a single bit of information sent from Yoshi to Zoya. If Yoshi does not receive the data packet correctly, he “sends” NACK by not transmitting 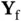 .
.
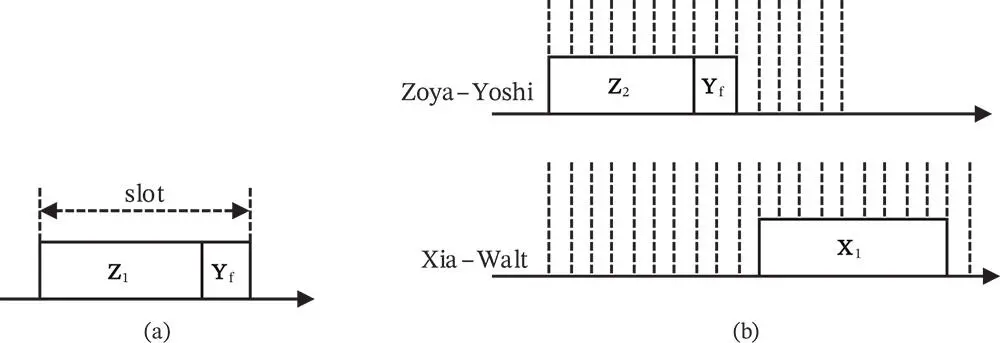 Figure 2.5 Transmission of a feedback packet
Figure 2.5 Transmission of a feedback packet 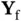 from Yoshi to Zoya for (a) a slotted channel, (b) carrier sensing.
from Yoshi to Zoya for (a) a slotted channel, (b) carrier sensing.
Figure 2.5(b)shows how the transmission of a feedback packet would operate in a CSMA setting. As in CSMA the basic time unit is a minislot and not a slot; we cannot say that the end of the slot is reserved for transmission of a feedback packet. Note that Yoshi, after receiving 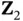 , does not wait for an idle minislot and he immediately sends
, does not wait for an idle minislot and he immediately sends 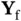 to Zoya. Xia, and potentially other contending transmitters, will detect that the medium is busy and postpone her transmission to start after
to Zoya. Xia, and potentially other contending transmitters, will detect that the medium is busy and postpone her transmission to start after 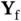 is followed by an idle slot. We can interpret this as if the feedback packet has a higher priority over a data packet sent by another node.
is followed by an idle slot. We can interpret this as if the feedback packet has a higher priority over a data packet sent by another node.
This observation reveals the inherent capability of the CSMA mechanism to introduce different priority classes. In the simplest case, there can be two classes of traffic: high and low importance, respectively. Then the protocol can be designed such that a high-priority data uses a single minislot for carrier sensing, while low-priority data uses two minislots for carrier sensing. Let, for example, Zoya send a high-priority packet that corresponds to some data for critical control system managed by Yoshi, while Xia sends to Walt data from, for example, an entertainment service. After the busy medium is released, then Zoya will always be the first to start a transmission after a single idle minislot, while Xia will defer her transmission. On another note, this property of CSMA can be misused by a malicious user. For example, the CSMA protocol can be specified such that the minimum idle time before the transmission is 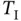 . However, a malicious user can set his device to wait for a time less than
. However, a malicious user can set his device to wait for a time less than 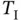 and in this way always gain an advantage in accessing the shared medium.
and in this way always gain an advantage in accessing the shared medium.
Читать дальше


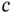 is the propagation speed, equal to the speed of light. We can soften the propagation assumption and enrich our collision model by assuming the following: the communication range is
is the propagation speed, equal to the speed of light. We can soften the propagation assumption and enrich our collision model by assuming the following: the communication range is 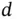 , but the range within which the carrier can be sensed, called the sensing range, is larger, say
, but the range within which the carrier can be sensed, called the sensing range, is larger, say 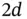 . The rationale can be drawn from the analogy with speech: as Yoshi goes away from Zoya, after some distance he can hear that she is speaking, but cannot understand the words. If Zoya and Yoshi are terminals that are situated at the opposite ends of Basil's cell, then the distance between them is
. The rationale can be drawn from the analogy with speech: as Yoshi goes away from Zoya, after some distance he can hear that she is speaking, but cannot understand the words. If Zoya and Yoshi are terminals that are situated at the opposite ends of Basil's cell, then the distance between them is 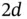 and the duration of the minislot should be chosen to be
and the duration of the minislot should be chosen to be 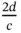 . In practice, it gets more complicated as not all signals travel over a straight line, as some of the waves that carry wireless information are reflected and arrive later.
. In practice, it gets more complicated as not all signals travel over a straight line, as some of the waves that carry wireless information are reflected and arrive later.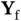 , can, in principle, carry a single bit of information, either acknowledging (ACK) the packet reception or sending a negative ACK (NACK). The latter is sent in the case there is a collision and thus an incorrect reception. The feedback packet is, generally, much shorter than the data packet.
, can, in principle, carry a single bit of information, either acknowledging (ACK) the packet reception or sending a negative ACK (NACK). The latter is sent in the case there is a collision and thus an incorrect reception. The feedback packet is, generally, much shorter than the data packet.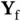 from Yoshi for the case when the channel is slotted. Differently from the slotted model used before, where the slot duration was equal to the packet duration, here the slot duration is longer than the duration of Zoya's packet. The remainder of the slot, after the end of Zoya's packet, is reserved for Yoshi to transmit the ACK message
from Yoshi for the case when the channel is slotted. Differently from the slotted model used before, where the slot duration was equal to the packet duration, here the slot duration is longer than the duration of Zoya's packet. The remainder of the slot, after the end of Zoya's packet, is reserved for Yoshi to transmit the ACK message 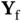 , while Zoya is in a listening mode. Referring to Figure 2.4(a), Yoshi receives
, while Zoya is in a listening mode. Referring to Figure 2.4(a), Yoshi receives 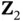 successfully and sends
successfully and sends  ACK. The packet
ACK. The packet 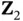 is not received correctly and Yoshi sends
is not received correctly and Yoshi sends 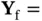 NACK. If we assume that all nodes are in each other's communication range, then at the same time when Walt sends NACK to Xia, collision occurs at the receiver of Zoya, as well as that of Xia. As a result, Zoya does not receive the NACK. To avoid this type of situation, one can use randomized contention for sending the feedback packets, which is a contention that occurs in addition to the contention used for data packets. Nevertheless, in our communication model, Zoya can receive NACK also implicitly , through the absence of ACK. In other words, the mere existence or absence of
NACK. If we assume that all nodes are in each other's communication range, then at the same time when Walt sends NACK to Xia, collision occurs at the receiver of Zoya, as well as that of Xia. As a result, Zoya does not receive the NACK. To avoid this type of situation, one can use randomized contention for sending the feedback packets, which is a contention that occurs in addition to the contention used for data packets. Nevertheless, in our communication model, Zoya can receive NACK also implicitly , through the absence of ACK. In other words, the mere existence or absence of 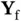 can be understood as a single bit of information sent from Yoshi to Zoya. If Yoshi does not receive the data packet correctly, he “sends” NACK by not transmitting
can be understood as a single bit of information sent from Yoshi to Zoya. If Yoshi does not receive the data packet correctly, he “sends” NACK by not transmitting 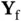 .
. Figure 2.5 Transmission of a feedback packet
Figure 2.5 Transmission of a feedback packet 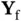 from Yoshi to Zoya for (a) a slotted channel, (b) carrier sensing.
from Yoshi to Zoya for (a) a slotted channel, (b) carrier sensing.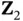 , does not wait for an idle minislot and he immediately sends
, does not wait for an idle minislot and he immediately sends 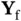 to Zoya. Xia, and potentially other contending transmitters, will detect that the medium is busy and postpone her transmission to start after
to Zoya. Xia, and potentially other contending transmitters, will detect that the medium is busy and postpone her transmission to start after 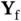 is followed by an idle slot. We can interpret this as if the feedback packet has a higher priority over a data packet sent by another node.
is followed by an idle slot. We can interpret this as if the feedback packet has a higher priority over a data packet sent by another node.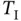 . However, a malicious user can set his device to wait for a time less than
. However, a malicious user can set his device to wait for a time less than 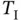 and in this way always gain an advantage in accessing the shared medium.
and in this way always gain an advantage in accessing the shared medium.










