Smartphones and cell phones come with their own separate set of issues, for example, use while driving. Employers have used a variety of strategies when addressing this issue. Some have adopted the so-called Nancy Reagan approach (“just say no”), even as others have adopted policies permitting hands-free use of the phone while driving. The underlying issue is extremely important because the National Safety Council reported that, in 2016, more than 40,000 traffic fatalities occurred in the United States for the first time in 10 years. The National Safety Council also reported a 6% increase in auto crash deaths in 2016 compared with 2015. Distracted driving, including cell phone use and texting, accounted for 3,477 fatalities and 391,000 injuries in 2015 motor vehicle crashes, according to the National Highway Traffic Safety Administration. Some reports have asserted that these statistics materially underreport the incidence of distracted driving. But if an employer adopts a “no cell phone use while driving” policy, what happens if the CEO is in an accident while talking on a cell phone? Is such a policy an invitation to employees to simply ignore it?
Devices, like social media, present privacy, ownership, and responsibility issues for employers and employees that are not easily resolved. And as new technologies are introduced, these are unlikely to resolve controversies now underway in suits and EEOC proceedings — at least until self-driving cars become as common as today's smartphones.
Use of company computers and smartphones
The Fence-it-In Company (FII) is a manufacturer of metal and wood fences sold at large home improvement and hardware stores. The company provides its employees with internet access through a password-protected home page. The employee policy manual states that employees are not to use FII internet access for any personal purposes. FII does not track the internet use of its employees, but maintains blocks on for-pay, explicit, and common pirated content sites. You have just been hired as the new CFO, and in this position you are responsible for the HR function. You are concerned that FII's policies on internet access might not be strong enough.
What are some of the risks that FII is running?– FII is running a number of risks, including the following:Sending and receipt of personal email using FII internet accessUse of FII internet to access sites for purely personal purposes□ This can be a productivity issue as well as a legal issue.Disclosure or theft of company data on FII's network, including software FII licenses from othersUncertainty of whether FII's blocking function is effective or updated regularly□ Lack of monitoring increases this uncertainty.Employee downloads may bring viruses onto FII's network.Employee downloads of third-party content may violate copyright or trademark laws.
How should FII respond to these risks?– Here are some of the ways in which FII may respond to these risks:Monitor internet use by all employees on a historical (after-the-fact) basis.□ Real-time monitoring is a violation of the Espionage Act unless national security applies.Monitoring should encompass all company devices with internet access.□ An employee's expectation of privacy can be removed by the employee signing a disclosure agreement in which FII advises the employee of its intent to monitor internet use on all company devices.Examine cookies placed on the employee's computer.Install security software that prevents unauthorized downloads from third-party sites, and prevents unauthorized uploads from the FII network.Update all internet use policies and have all employees sign an acknowledgment and agreement to the updated policies. The policies should be clear that personal use of company computers or other devices to access the internet is prohibited; and that company networks, computers, and other devices connected to company networks (on-site or remotely) are property of the employer and should be used only for business purposes.□ This can be a productivity issue as well as a legal issue.□ Those policies should expressly provide that password protection does not, and should not, create an expectation of privacy on the part of the employee, and that employees have no privacy rights in emails, text messages, or voicemail messages that are sent using company computers or routed through company computers, networks, or smartphones.˚ The policies should make clear that unauthorized use of company computers or other devices, unauthorized access to FII data, and use of unauthorized software on FII computers or devices is prohibited and can result in severe disciplinary action up to and including termination. These policies should also provide that˚ company policies regarding harassment, discrimination, retaliation, and other prohibited forms of conduct apply to all types of electronic communications;˚ email and text messages can be reconstructed or recovered after being “deleted,” meaning that deletion will not eliminate a problematic email or text; and˚ employees will be notified of a potential or filed lawsuit or arbitration claim, which will trigger an obligation to preserve all related electronic communications and information, and employees must ensure that all electronic communications and information is thereafter preserved in accordance with the company's document retention policies.Ensure that FII's policies prohibit the use of company computers or other devices to send or receive email that contains content which is illegal, explicit, discriminatory, may be deemed harassment, may be deemed hate speech, is unwelcome, or otherwise violates company policies or company confidentiality.
According to a 2016 survey conducted by Harris Poll for CareerBuilder: 2
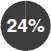 |
of employers had fired an employee for misusing company-provided internet. |
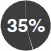 |
of employers monitor internet sites visited by employees. |
 |
of employees used their personal smartphones or tablets to shop using the internet during work hours. |
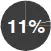 |
of employers fired an employee for holiday shopping on the internet during work hours. |
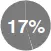 |
of employers fired employees for postings on social media. The survey did not provide a breakdown of the reasons for termination, for example, divulging company confidential information, use of offensive or harassing language about supervisors or colleagues, or other violations of company policies. |
The key to monitoring and best practices
If an employer chooses to monitor the internet use, email, text messages, instant messages, or tweets sent or received by employees using company-owned computers and devices, such monitoring should be performed only after the employee is expressly told that monitoring will occur. Best practices followed by most companies call for each new employee to sign an agreement or policy acknowledgment (APA) at the time the employee starts work.
The APA states that the employee acknowledges that the employer will monitor internet use, as well as email, texts, instant messages, and tweets sent or received by the employee (after the fact). The APA also advises the employee of the consequences of a violation of the agreement or policy. Getting a signed APA is key because this document “removes the expectation of privacy” that the employee may otherwise have in his or her internet activities and electronic communications. In turn, removal of that expectation will position the employer to prevail in any later litigation over unauthorized internet use or electronic communications that violate company policies.
Читать дальше

















