2.7.2 Increase User Autonomy
The value of the consent of the user to the processing of IoT powered data. This underlines the need for verification and preference for individual influence of sensitive data and hence for increased privacy. Not all data has to be selected. If the usage of data is incompatible with the meaning of experiences, a simple and easy-to-read alternative will be given to individuals. Similar claims have been made in the literature. As regards the freedom of individuals, in particular with regard to IoT privacy security (Kounelis et al . [21]), it is argued that only if a mixture of person and artifact retains the ability to make deliberate choices and decisions in architecture, and awareness and vigilance in the field of freedom and security, can the overall interactions maintain confidence and trust Figure 2.7.
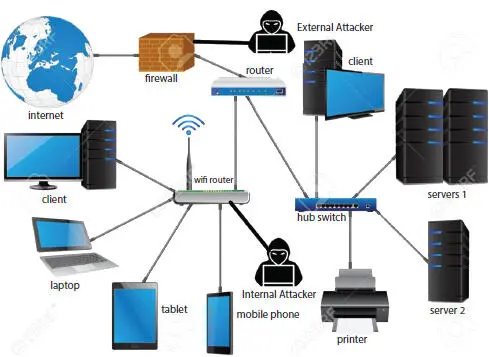
Figure 2.6Internal and external attacker on IoT Infrastructure.
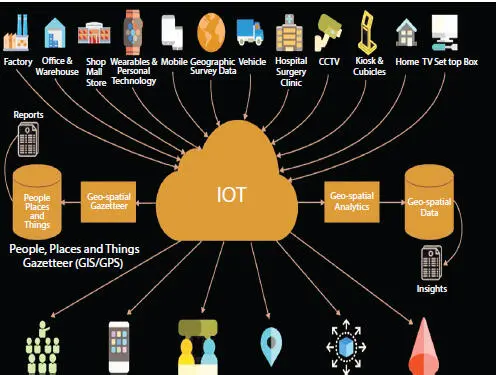
Figure 2.7Different data sources of IoT.
Earlier firewalls were high-ticket items of hardware that solely corporations would make use.The general public weren’t on the web, and if they were they were connected via a dial up that isn’t quick enough for many hacker’s functions. Consequently, hackers primarily attack United Nations organizations which with wider repositories of information available. At present, almost everyone has the ability to link to the website, and many hackers tend to concentrate on the house user since they are additionally capable of not securing their computers properly, which transform them into an unimpressive target. This in mind, yet strong home firewall technologies were built by developers to protect themselves. The house users’ firewalls are either a hardware or a cable.
Hardware firewall: A hardware firewall may be a bridge between your network association and the other blocked computers. In addition, these firewalls have an interconnected gateway that allows you to connect several devices to them so that anyone can join a network association. Such firewalls secure any single device linked to the Network Address Translation or NAT using a technology. Both secure computers, such as 192.168.1.X, that can not be reached via the network are secure by victimization and non-public data abuse. These internal data processors are then combined into one by the firewall. This allows the hardware firewall to accept all incoming requests you received and forward them to the internal PC received. This system, beyond machines, cannot be linked to the computers by the victimization of this technique.
Personal firewall: Any computer to be covered will be a Private Firewall kit that is installed into it. This kit then filters all input and generally outgoing traffic and makes only required or specifically allowed information. Computer firewalls are typically abundant in additional functionality than hardware models, but they have little capacity to connect the site connection with other network computers.
The decision on which form of firewall is based on what you want to use. Unless you want to just protect 1 pc, then mainly personal firewall kit is more than sufficient. When you want to protect many machines, a hardware-based solution is also of great benefit. Many people also say you can use a hardware firewall to save your network and a virtual firewall to secure your device. While sometimes this is not a good program, for other consumers it will be a prevention feature. When cash isn’t paired in nursing, instead through victimization will provide a degree of protection, as the bigger practicality found in personal firewalls.
Filtering is carried out once a firewall examines the passage of information and determines whether that information is permitted to be transmitted and received or if supported rules and filters that are created must be discarded. It is the firewall’s usually first operation, and the protection demands extremely the way it performs these functions. The general public believes that the firewall is the most significant firewall operation, specifically, the transfer of inward knowledge to the computers. However, the departing filtering also plays a key role in protecting your machine. You may have malware inserted on your PC while your data was not, and you will suddenly see that the PC package tries to transmit information to a foreign host someplace on the web after you install a firewall with departing filtering. Now, you don’t just understand this package, but the filtering stopped distributing non-public information.
These filters can be modified so that all PCs on the network can effectively transfer information into your device or probably apps on your computer. Nevertheless, your desires will be guided by these laws. You would need to open port for remote desktop-related communications protocol (port 3389) to allow the traffic to move through your firewall, for example if you want remote users to connect to the remote victimization device remotely. The following example of this can be found in the nursing when permission to access the computer behind the firewall is granted to a particular remote PC Figure 2.8.
It’s critical that your firewall doesn’t actually obstruct attempts to access your laptop, but it doesn’t even appear like your laptop exists on the network. You are in what is known as concealment mode after square measuring connected to the web and your laptop can not be detected by samples on the laptop. Hackers will see how the computer is scanned with special expertise and the findings on the site. If you calculate in a cover-up mode, the firewall does not return this information, but appears to be connected. This information is not really connected. Thanks to this hacker your laptop does not continue to hit, because they believe that you are not online.
There are actually a great number of firewalls with the ability to dam spyware, hijackers and adware. It helps you to shield your machine from interference of code which is marvelous to expose sensitive knowledge about what you do on the net or other programming activities. Ses square solutions are also packaged into firewall kit business versions.
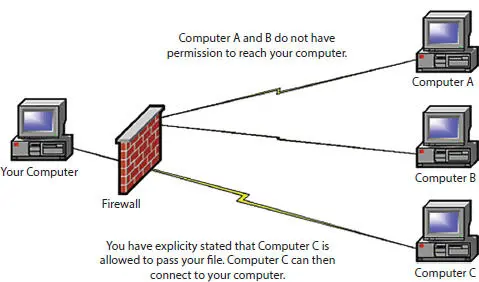
Figure 2.8Firewall that allows remote user access to a firewall device.
2.7.7 Integrity in Service
Integrity of operation is where the firewall controls the computer’s files to change them or how they are released. If such an alteration is detected, the user will be informed and the application will not be able to execute or transmit IoT information. Sometimes those improvements could have been used in an update, but now you will be told of it, if, it is changed by the malicious software.
2.7.8 Sensing of Infringement
Intruders use various techniques to breach the computer’s protection. Intrusion detection checks incoming system signature data and notifies you when these attempts are detected. With intrusion detection, you can see what a hacker wants to do to hack your computer.
Читать дальше















