Now that we've covered all the types of cybercrimes, bad actors, and breach threats, let's discuss how a breach is typically carried out. It can be broken down into five main steps: research, intrusion, lateral movement, privilege escalation, and exfiltration. CEO John Chambers once said, “There are two types of companies: Those that have been hacked, and those who don't know yet that they have been hacked.”
Phase 1: ResearchThis phase can begin months before detection. For most attackers, it begins by finding out as much as possible about their target. Searches on LinkedIn and company websites for possible phishing targets are common. Their reconnaissance may include researching who the third parties and affiliates are, locating buildings and Wi‐Fi networks, and discovering information on security systems and any entry points. Like any good attacker, knowing where the target stores its valuables and how they protect them are key components of planning a hack. Once all this intelligence is gathered, the type of tools and methodology can then be determined, and their intrusion can begin.
Phase 2: IntrusionAs in the research phase, intrusion can take months before discovery. This phase involves the attacker being focused on breaking into the perimeter of the target, with a persistent foothold being their ultimate goal. Whether they used a phishing campaign to steal credentials or used hacking tools to crack into the network, attackers usually are able to do this and remain nearly invisible to the victim. Once they are inside the network, the attacker will work to ensure their access is long term in the anticipation of revisiting on a regular basis.
The five steps to a breach are shown in Figure 2.3below.
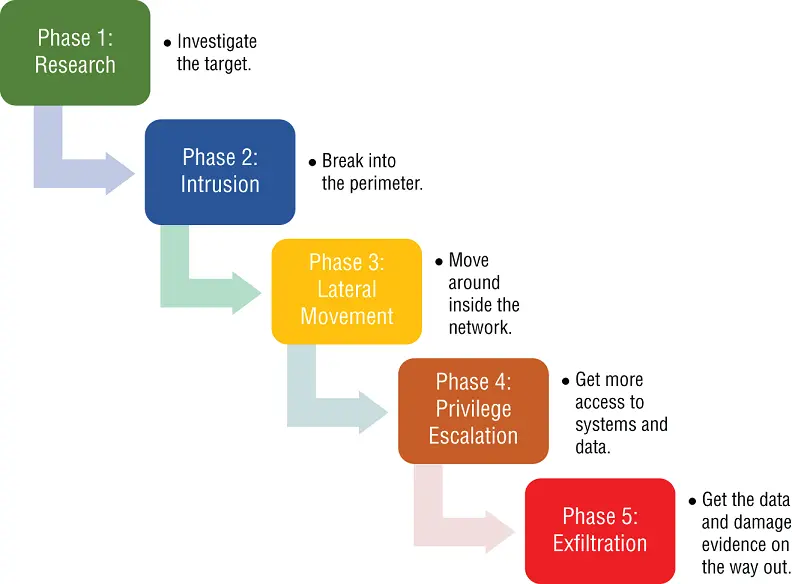
FIGURE 2.3The Five Steps to a Breach
Phase 3: Lateral MovementAfter the access becomes more persistent (the attacker has a solid foothold in the target network), the attacker's goal is to find and access more systems within the network. They will search files, databases, password files, sensitive data locations, and network mapping for this work. Most often, the attacker is impersonating an authorized user, so detection is difficult without robust countermeasures such as SIEM and IDS/IPS. This phase generally takes place months or weeks prior to detection.
Phase 4: Privilege EscalationThe majority or totality of sensitive information in most company networks is (or should be) protected behind layers of defense that require special access rights. In cases where these user accounts have elevated access, such as in the case of administrators or data owners, this is called Privileged Access . This type of access allows the attacker to get at the data needed, so they must find a way to escalate their initial access. Once this access is obtained, then the attacker will go after their internal targets: sensitive company documents, PII, mail servers, document systems, and other areas.
Phase 5: ExfiltrationIn this final phase, the attacker is in the home stretch. They have attained the intel necessary, broken into the network, looked around for the stuff to steal, gained access to those systems, and are now ready to steal it. They steal the data, sometimes damaging critical systems used to track their movements and disrupt operations. Some destroy any evidence with a ransomware attack at this point. Some linger in the network, if they think they are not detected, waiting for new opportunities to exploit their access. Once they have reached this stage, it is very difficult to stop the attack and the cost to the company increases the longer it goes undetected.
The Third‐Party Breach Timeline: Target
The discussion of the five phases for a breach can be best demonstrated by using Target as an actual example. In December 2013, it was announced that around 70 million payment card data records for Target's shoppers had been stolen through the point‐of‐sale (POS) system. In addition, over 11 GB of data was exfiltrated. The anatomy of how it occurred illustrates both the vulnerability of third parties and how an attacker goes through the five phases.
Research:HVAC vendors were likely targeted as this third party is used as a backdoor to gain access. An internet search could have produced information about how Target works with its vendors and likely would've shown vendor portals. Also easily found is the Microsoft study done on how Target uses its virtualization software, the MS Domain Name Server (DNS), its software for managing system configurations (Systems Center Configuration Manager [SCCM]), and other important intel about internal systems.
Analysis then shows a phishing email was sent to Target's HVAC vendor, Fazio Mechanical, with malware that was a password‐stealing bot. It is suspected that this software sent stolen credentials to the attackers.
Intrusion:Using the stolen credentials from Fazio Mechanical, attackers logged in to Target's systems via a vendor portal. Because they stole valid credentials, no alarms were sent. This type of credential from the vendor gave them the continuous access to make repeated attempts at the next steps for the breach.
Lateral Movement:Using the valid user credentials and a solid beachhead (i.e., a foothold within the target network), they now could leverage much of their research into what type of systems the target had running internally to the attacker's advantage. Along with their tools for hacking, knowing that they had SCCM and Microsoft's DNS, among other products, would have given them an advantage in looking for vulnerabilities to exploit. In addition, attackers likely would have deployed common network scanning tools to create a map to help them decide the next best steps for the lateral movement.
Privilege Escalation:As attackers moved laterally within the Target environment, the objective would be to find privileges that worked with the POS system. As they exploited these known vulnerabilities on the Microsoft and other systems they had identified in their reconnaissance, intrusion, and lateral movement phases, that data was leveraged to elevate themselves to be able to perform the last step.
Exfiltration:The malware was distributed to the POS machines in such a fashion as to suggest it was an automated update, indicating that the attackers had attained privileged access to the central system that updates those machines. Because the malware was custom written, virus scanners did not have their signature to detect it. As the payment cards were swiped, their data was stored in a system configuration file that was shared over well‐known ports. This data collection from all the different POS machines was then sent to a compromised server internal to Target's network. The data was then retrieved via a number of electronic “drop” locations worldwide. The Target team in India notified the Minneapolis team of the attack, but they took no action on the warning.
The breach itself took place from November 27 to December 15, 2014. Obviously, we do not know how long the research phase took for the attackers. What the timeline does show is how methodical and clever attackers can be when attempting to ambush a victim. In this case, leveraging the available public information not only got attackers access to the vendor portal, but also gave them candidates from the vendors so they could select one with lower access standards. This breach cost Target hundreds of millions of dollars in direct damage, lost revenue, and reputational costs. Many C‐level and lower‐level employees lost their jobs, including the CIO and CEO, while the board of directors was threatened with removal as well.
Читать дальше




![Stephan Orth - Behind Putin's Curtain - Friendships and Misadventures Inside Russia [aka Couchsurfing in Russia]](/books/415210/stephan-orth-behind-putin-s-curtain-friendships-a-thumb.webp)








