Access control (AC)
Awareness and training (AT)
Audit and accountability (AU)
Security assessment and authorization (CA)
Configuration management (CM)
Contingency planning (CP)
Identification and authentication (IA)
Incident response (IR)
Maintenance (MA)
Media protection (MP)
Physical and environmental protection (PE)
Planning (PL)
Personnel security (PS)
Risk assessment (RA)
System and services acquisition (SA)
System and communications protection (SC)
System and information integrity (SI)
Program management (PM)
NOTEThe latest revision of NIST 800-53, Rev. 5, was released in September 2020.
NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF), first published in 2014, is a collection of standards, guidelines, and best practices to manage cybersecurity risk. As of this writing, NIST CSF v1.1 is the current version and was released in 2018. NIST CSF was initially developed with a focus on industries considered “critical infrastructure” — industries such as banking, energy, and communications. It has since become a go-to controls framework for companies of all sizes and across all business sectors.
The NIST CSF aligns with controls and best practices in NIST 800-53 and other control frameworks, but was designed to be a more flexible and understandable option for private-sector companies to adapt. The NIST Cybersecurity Framework consists of five core functions, each with multiple subdivisions NIST calls categories. (See Figure 1.2.)
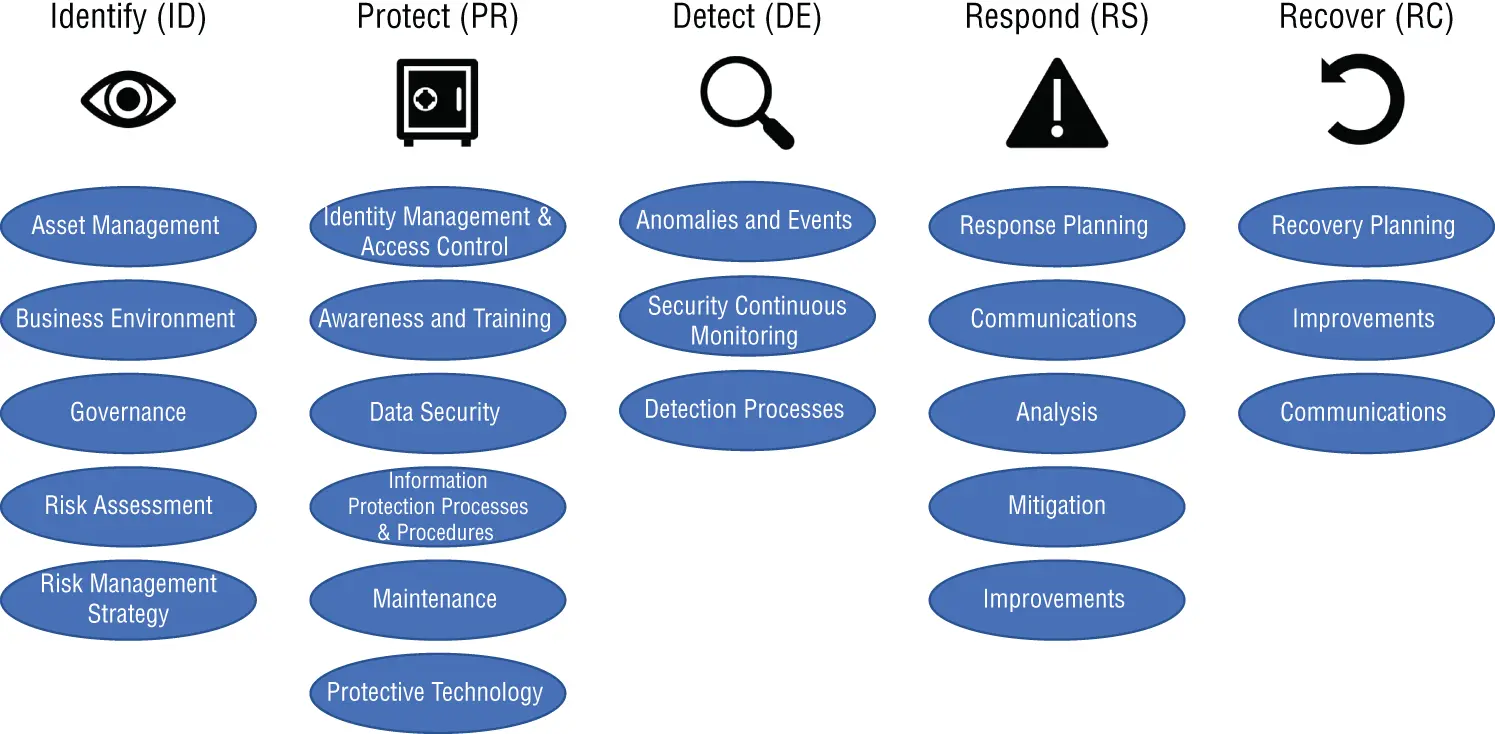
FIGURE 1.2 NIST Cybersecurity Framework
The five core functions within NIST CSF are intended to be performed simultaneously and continuously to form a culture of assessing and addressing cybersecurity risk. NIST defines the purpose of each of the five core functions as follows:
Identify (ID): Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
Protect (PR): Develop and implement appropriate safeguards to ensure delivery of critical services.
Detect (DE): Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
Respond (RS): Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
Recover (RC): Develop and implement appropriate activities to maintain plans for resilience and restore any capabilities or services that were impaired due to a cybersecurity incident.
The five core functions are divided into 23 categories, and these categories are further divided into a total of 108 subcategories. Each subcategory describes a specific security control or desired outcome. Visit www.nist.gov/cyberframeworkfor the complete list of subcategories and additional guidance on using the NIST Cybersecurity Framework.
CIS Critical Security Controls
The CIS Critical Security Controls (or CIS Controls) is a publication of 20 best-practice guidelines for information security. The publication was initially created by SANS Institute but was transferred to the Center for Internet Security (CIS) in 2015. Today, you may see these 20 critical controls labeled CIS CSC, CIS 20, Sans Top 20, or other variants.
CIS Controls v7.1 was released in April 2019, and identifies the basic, foundational, and organizational controls that CIS recommends mitigating the most common attacks against networks and systems. According to the Center for Internet Security, the 20 Critical Security Controls are as follows:
CIS Control 1: Inventory and Control of Hardware Assets
CIS Control 2: Inventory and Control of Software Assets
CIS Control 3: Continuous Vulnerability Management
CIS Control 4: Controlled Use of Administrative Privileges
CIS Control 5: Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
CIS Control 6: Maintenance, Monitoring, and Analysis of Audit Logs
CIS Control 7: Email and Web Browser Protections
CIS Control 8: Malware Defenses
CIS Control 9: Limitation and Control of Network Ports, Protocols, and Services
CIS Control 10: Data Recovery Capabilities
CIS Control 11: Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches
CIS Control 12: Boundary Defense
CIS Control 13: Data Protection
CIS Control 14: Controlled Access Based on the Need to Know
CIS Control 15: Wireless Access Control
CIS Control 16: Account Monitoring and Control
CIS Control 17: Implement a Security Awareness and Training Program
CIS Control 18: Application Software Security
CIS Control 19: Incident Response and Management
CIS Control 20: Penetration Tests and Red Team Exercises
NOTEThe controls and subcontrols within the CIS CSC break down into what are known as Implementation Groups. According to CIS, “Implementation Groups provide a simple and accessible way to help organizations of different classes focus their security resources, and still leverage the value of the CIS Controls program ….” In essence, these Implementation Groups help organizations prioritize controls and identify the subcontrols that are most reasonable for level of expertise and their risk profile. Visit www.cissecurity.orgfor more information on the CSC and their Implementation Groups.
Due Care and Due Diligence
Governance requires that the individuals setting the strategic direction and mission of the organization act on behalf of the stakeholders. The minimum standard for their governance action requires that they act with due care. Due care is a legal term used to describe the conduct that a reasonable person would exercise in a given situation. In business, due care is using reasonable care to protect the interests of your organization. More specifically, in regard to information security, due care relates to the conduct that a reasonable person would exercise to maintain the confidentiality, integrity, and availability of their organization's assets. This concept of “reasonable” can be a bit nebulous at first, but it is intended to protect a person or organization from accusations of negligence. In short, court decisions around the world have demonstrated that a person's actions can be assumed “reasonable” if a person of similar background and experience, confronted with the same situation would enact the same or similar actions. Examples of due care in security are activities like scanning and patching security vulnerabilities, enabling security logging, and writing restrictive firewall rules that enforce least privilege (discussed in Chapter 3, “Security Architecture and Engineering”).
Due diligence is another legal concept that relates to continually ensuring that behavior maintains due care. In other words, due diligence is the ongoing execution and monitoring of due care. In relation to information security, due diligence relates to the ongoing actions that an organization and its personnel conduct to ensure organizational assets are reasonably protected. Examples of due diligence in security are activities like reviewing security log output for suspicious activity and conducting penetration tests to determine if firewall rules are sufficiently restrictive.
The concepts of due care and due diligence are incredibly important in the legal and finance world, but they must also be understood by information security professionals. Exercising due care and conducting due diligence are required to avoid claims of negligence in court. The CISSP CBK aims to establish the set of knowledge and activities required of a “reasonable” security leader.
Читать дальше













