The implementation of an SDN controller can be centralized or distributed. In the centralized implementation, a single SDN controller centrally controls and manages all network devices, which would possibly lead to bottleneck. Distributed implementation of the SDN controller would overcome this issue. The CP may include multiple controllers, depending on the network size. This will help boosting the network performance.
SDN has strengthened applying programmatic principles on network, allowing network administrators to have precise, flexible, and innovative control of the network and thus reducing operational expenses.
The SDN architecture provides an opportunity to more efficient application of cognitive network concepts in a centralized system, leading to self-aware networks. The adoption of SDN-based systems highly depends on their success in providing solutions to problems that could not be solved by traditional network architectures and protocols [12].
Applying ML techniques with SDN is considered to be effective for the following reasons [13]:
The recent advanced developments in computing and the accompanying advanced processors, thus creating a new opportunity to apply promising learning techniques.
It is well known that ML algorithms depend on data. The SDN controller has a holistic view on the network and is able to collect different network data, simplifying the application of ML algorithms.
Based on the ability of the SDN to act in real time and deal with historical data, ML techniques can create intelligence in the controller unit, by conducting data analysis relying on analyzed data in decision-making and thus improving the network and its services.
The programmatically feature of SDN can help to find optimal solutions to network problems such as configuration and resource allocation. Thus, ML algorithms can be implemented in real time.
2.6 Cognitive Radio Networks
The Federal Communications Commission (FCC) defines cognitive radio as: “a radio that can change its transmitter parameters based on interaction with the environment in which it operates”.
The main features of cognitive radio are as follows [14]:
Awareness: CR is aware of its surrounding environment through the sensing capability.
Intelligence: CR is a programmable intelligent wireless communication system capable of learning from information collected from the environment.
Adaptivity: CR adapts to the variation of the radio spectrum conditions and application requirements by dynamically reconfiguring its operational parameters.
Dynamic Spectrum Access has been proposed for efficient utilization of radio spectrum. Spectrum bands are categorized as licensed and unlicensed bands. Licensed bands are used by licensed users, called Primary Users (PUs). They have the priority to use the spectrum. Unlicensed users, called Secondary Users (SUs) can use the licensed bands as long as the PUs are not temporally using it; or as long as the PUs’ can properly be protected. However, SUs should vacate the licensed bands immediately when a PU is detected to be active. This will significantly improve spectrum utilization. SUs detect the conceivable vacant bands, determine operational channel, and eventually adjust their parameters. Thus, efficient spectrum sensing techniques are key to the successful operation of CR networks.
In CR systems, SUs should be able to [14]:
Sense the spectrum bands and determine the possible channels as well as activity of PUs.
Decide on the quality of available channels that satisfy users’ requirements.
Share the available channels with other SUs.
Avoid harmful interference to PU who is starting to use the any channel by vacating the channels PU just start operating on.
The detection of PU’s presence is a major challenge in CR. This process needs complex sensing technologies. This complexity stems from the nature of the electromagnetic signals, the multipath fading, and the changing interference. Spectrum sensing for CR systems is a very interesting research area. Researchers try to develop quick and accurate methods to detect the PU’s activity.
The transmission cycle of a SU can be represented as seen in Figure 2.8. The sensing process is performed periodically using one of the sensing methods. During the sensing time, the SU does not transmit data. After sensing, SU can decide to transmit on the same channel or switch to another channel, depending on PU presence. The transmission continues until the next sensing period. Clearly, the sensing time should be as short as possible, but at the same time enough for accurate sensing. Therefore, there is a trade-off between protecting the PU’s QoS and improving the QoS of SUs.
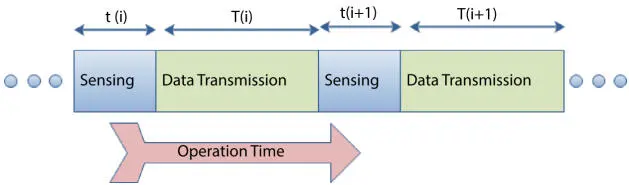
Figure 2.8The transmission cycle of SU.
The fundamental objective of sensing methods is to increase the positive detection probability and decrease the false detection probability of PUs. This leads to more protection of PUs and at the same time more utilization of the available spectrum. In this section, we present the main sensing methods. However, several other methods can be found in the literature.
1. Energy Detection
The most commonly adopted method because of its simplicity and the associated computation overhead. It requires short sensing interval. An energy detector is used to detect a narrowband channel. The detected energy is compared to a predefined threshold. If the measured energy is found to be larger than the threshold, then PU is judged to be active. The selection of the threshold is a challenge because the noise level is normally unknown.
2. Cyclostationary Feature Detection
This method aims at distinguishing between PUs’ signals, interference, and noise. This is achieved by identifying the cyclostationary features of signals, including modulation type, carrier frequency, and data rate. The implementation of this method needs sufficient prior information about these features of the PUs’ signals so that the method can use this knowledge as a base during the matching of measured features with those belong to PUs’ signals. Hence, sufficient number of samples is needed for accurate performance, leading to long sensing intervals.
3. Matched Filtering
This method is considered to be the most accurate method that achieves higher detection probability in short sensing intervals. The basic idea of this method is that the sensed signal is passed thought a filter that is matched to the PUs’ signals. Despite its accuracy, the method is considered to be impractical in cases wherein PUs transmit signals of different features.
2.7 ML for Wireless Networks: Challenges and Solution Approaches
In previous sections, we discussed various topics about recent trends in network configuration, control, and management. We indicated recent trends in network architecture design in order to respond to the requirements of large-scale networks. Large-scale networks feature a significant increase in the number of users and smart technology-based systems that have become an integral part of human life, especially with the vast amount of software applications that require high speeds and fast real time response. In addition to that, different applications emerged in the last years to allow easy and high quality communication between people. Such applications have become an important tool used even by the largest media stations.
In the following sections, we review and discuss important challenges in wireless networking that can be better tackled, exploiting ML approaches. The application of ML in wireless networking aims at reducing human interaction and creating a self-driven network, that are able to optimize and configure themselves. We focus on recent published research and try to shed light on important research aspects of the present and future. Our goal is to assist readers to identify the scientific areas and specific issues that need further research and exploration. We divide the discussion into three parts. In the first part, we focus on Cellular networks, while the second part focuses on wireless local area networks (WLANs). The third part is devoted to cognitive radio networks.
Читать дальше













