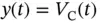1 Cover
2 Title Page Cyber‐physical Systems Theory, Methodology, and Applications Pedro H. J. Nardelli
3 Copyright
4 Preface
5 1 Introduction 1.1 Cyber‐Physical Systems in 2020 1.2 Need for a General Theory 1.3 Historical Highlights: Control Theory, Information Theory, and Cybernetics 1.4 Philosophical Background 1.5 Book Structure 1.6 Summary Exercises References
6 Part I 2 System 2.1 Introduction 2.2 Systems Engineering 2.3 Demarcation of Specific Systems 2.4 Classification of Systems 2.5 Maxwell's Demon as a System 2.6 Summary Exercises References 3 Uncertainty 3.1 Introduction 3.2 Games and Uncertainty 3.3 Uncertainty and Probability Theory 3.4 Random Variables: Dependence and Stochastic Processes 3.5 Summary Exercises References 4 Information 4.1 Introduction 4.2 Data and Information 4.3 Information and Its Different Forms 4.4 Physical and Symbolic Realities 4.5 Summary Exercises References 5 Network 5.1 Introduction 5.2 Network Types 5.3 Processes on Networks and Applications 5.4 Limitations 5.5 Summary Exercises References 6 Decisions and Actions 6.1 Introduction 6.2 Forms of Decision‐Making 6.3 Optimization 6.4 Game Theory 6.5 Rule‐Based Decisions 6.6 Limitations 6.7 Summary Exercises References
7 Part II 7 The Three Layers of Cyber‐Physical Systems 7.1 Introduction 7.2 Physical Layer, Measuring, and Sensing Processes 7.3 Data Layer and Informing Processes 7.4 Decision Layer and Acting Processes 7.5 Self‐developing Reflexive–Active System and Cyber‐Physical Systems 7.6 Layer‐Based Protocols and Cyber‐Physical Systems Design 7.7 Summary Exercises References 8 Dynamics of Cyber‐Physical Systems 8.1 Introduction 8.2 Dynamics of Cyber‐Physical Systems 8.3 Failures and Layer‐Based Attacks 8.4 Summary Exercises References
8 Part III 9 Enabling Information and Communication Technologies 9.1 Introduction 9.2 Data Networks and Wireless Communications 9.3 Artificial Intelligence and Machine Learning 9.4 Decentralized Computing and Distributed Ledger Technology 9.5 Future Technologies: A Look at the Unknown Future 9.6 Summary Exercises References 10 Applications 10.1 Introduction 10.2 Cyber‐Physical Industrial System 10.3 Cyber‐Physical Energy System 10.4 Other Examples 10.5 Summary Exercises References Note 11 Beyond Technology 11.1 Introduction 11.2 Governance Models 11.3 Social Implications of the Cyber Reality 11.4 The Cybersyn Project 11.5 Summary Exercises References 12 Closing Words 12.1 Strong Theory Leads to Informed Practices 12.2 Open Challenges in CPSs 12.3 CPSs and the Fourth Industrial Revolution 12.4 Building the Future Exercises
9 Index
10 End User License Agreement
1 Cover
2 Table of Contents
3 Title Page Cyber‐physical Systems Theory, Methodology, and Applications Pedro H. J. Nardelli
4 Copyright
5 Preface
6 Begin Reading
7 Index
8 End User License Agreement
1 Chapter 1 Figure 1.1 Illustration of a CPS. Sensors measure physical processes, whose ... Figure 1.2 Operation of smart meters that react to hourly electricity price....
2 Chapter 2 Figure 2.1 Illustration of the Maxwell's demon thought experiment. Figure 2.2 Truth tables and logic gates of AND, OR and NOT operations.
3 Chapter 3 Figure 3.1 (a) Dominoes set; (b) example of a game.Figure 3.2 Example of a frequency diagram related to the observations of the...Figure 3.3 Domino tile in horizontal position: one number at the left side, ...Figure 3.4 Example of a frequency diagram related to the observations of the...Figure 3.5 Example of a frequency diagram related to the attribute 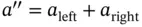 with
with 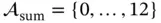 ...Figure 3.6 Example of a probability mass function diagram related to the ran...Figure 3.7 Poisson random variable considering two different client arrival ...Figure 3.8 Maxwell–Boltzmann probability density function of the random vari...Figure 3.9 Example of a random process. The number of persons in a queue, me...Figure 3.10 Markov chain representing a random variable
...Figure 3.6 Example of a probability mass function diagram related to the ran...Figure 3.7 Poisson random variable considering two different client arrival ...Figure 3.8 Maxwell–Boltzmann probability density function of the random vari...Figure 3.9 Example of a random process. The number of persons in a queue, me...Figure 3.10 Markov chain representing a random variable 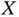 defined by the dif...
defined by the dif...
4 Chapter 4Figure 4.1 Relation between entropy functions and mutual information for two...Figure 4.2 Tree representing yes‐or‐no questions to resolve the uncertainty ...Figure 4.3 Diagram of a general communication system by Shannon.Figure 4.4 Car in a highway and level of processes.
5 Chapter 5Figure 5.1 Euler's approach to prove that the problem has no solution.Figure 5.2 Example of an undirected network with 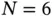 nodes and
nodes and 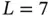 links.Figure 5.3 Example of different network topologies.Figure 5.4 Example of a WS network.Figure 5.5 Map of the Berlin S‐Train.Figure 5.6 Snapshot of the spatiotemporal propagation of flu using Nextstrai ...Figure 5.7 World airline routes.
links.Figure 5.3 Example of different network topologies.Figure 5.4 Example of a WS network.Figure 5.5 Map of the Berlin S‐Train.Figure 5.6 Snapshot of the spatiotemporal propagation of flu using Nextstrai ...Figure 5.7 World airline routes.
6 Chapter 6Figure 6.1 Examples of centralized, decentralized, and distributed networks....Figure 6.2 Rectangle with a fixed perimeter of length 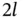 .Figure 6.3 Area of a rectangle considering a fixed perimeter of 20 m. The ma...Figure 6.4 Random access in wireless networks.Figure 6.5 Spatial throughput in wireless networks as a function of the prob...Figure 6.6 Game in the extensive form.Figure 6.7 Dove and hawk game in the extensive form.Figure 6.8 Example of the implementation of the alarm system using logic cir...
.Figure 6.3 Area of a rectangle considering a fixed perimeter of 20 m. The ma...Figure 6.4 Random access in wireless networks.Figure 6.5 Spatial throughput in wireless networks as a function of the prob...Figure 6.6 Game in the extensive form.Figure 6.7 Dove and hawk game in the extensive form.Figure 6.8 Example of the implementation of the alarm system using logic cir...
7 Chapter 7Figure 7.1 Electric circuit with direct current: a constant voltage source 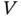 ...Figure 7.2 Dissipated power measured in watts as a function of the constant ...Figure 7.3 Data layer with four cyber elements: three representing the dissi...Figure 7.4 Numerical example of a realization of the stochastic processes
...Figure 7.2 Dissipated power measured in watts as a function of the constant ...Figure 7.3 Data layer with four cyber elements: three representing the dissi...Figure 7.4 Numerical example of a realization of the stochastic processes 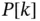 ...Figure 7.5 Self‐developing electric circuit: impact of decision rules and in...
...Figure 7.5 Self‐developing electric circuit: impact of decision rules and in...
8 Chapter 8Figure 8.1 Typical block diagram of (negative) feedback control.Figure 8.2 Example of a continuous‐time signal 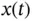 .Figure 8.3 Schematic of a system
.Figure 8.3 Schematic of a system 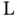 whose input signal is
whose input signal is 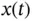 and output signal...Figure 8.4 RC circuit with an input signal
and output signal...Figure 8.4 RC circuit with an input signal 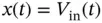 and an output
and an output 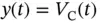
Читать дальше

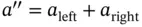 with
with 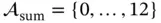 ...Figure 3.6 Example of a probability mass function diagram related to the ran...Figure 3.7 Poisson random variable considering two different client arrival ...Figure 3.8 Maxwell–Boltzmann probability density function of the random vari...Figure 3.9 Example of a random process. The number of persons in a queue, me...Figure 3.10 Markov chain representing a random variable
...Figure 3.6 Example of a probability mass function diagram related to the ran...Figure 3.7 Poisson random variable considering two different client arrival ...Figure 3.8 Maxwell–Boltzmann probability density function of the random vari...Figure 3.9 Example of a random process. The number of persons in a queue, me...Figure 3.10 Markov chain representing a random variable 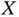 defined by the dif...
defined by the dif...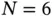 nodes and
nodes and 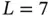 links.Figure 5.3 Example of different network topologies.Figure 5.4 Example of a WS network.Figure 5.5 Map of the Berlin S‐Train.Figure 5.6 Snapshot of the spatiotemporal propagation of flu using Nextstrai ...Figure 5.7 World airline routes.
links.Figure 5.3 Example of different network topologies.Figure 5.4 Example of a WS network.Figure 5.5 Map of the Berlin S‐Train.Figure 5.6 Snapshot of the spatiotemporal propagation of flu using Nextstrai ...Figure 5.7 World airline routes.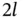 .Figure 6.3 Area of a rectangle considering a fixed perimeter of 20 m. The ma...Figure 6.4 Random access in wireless networks.Figure 6.5 Spatial throughput in wireless networks as a function of the prob...Figure 6.6 Game in the extensive form.Figure 6.7 Dove and hawk game in the extensive form.Figure 6.8 Example of the implementation of the alarm system using logic cir...
.Figure 6.3 Area of a rectangle considering a fixed perimeter of 20 m. The ma...Figure 6.4 Random access in wireless networks.Figure 6.5 Spatial throughput in wireless networks as a function of the prob...Figure 6.6 Game in the extensive form.Figure 6.7 Dove and hawk game in the extensive form.Figure 6.8 Example of the implementation of the alarm system using logic cir...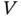 ...Figure 7.2 Dissipated power measured in watts as a function of the constant ...Figure 7.3 Data layer with four cyber elements: three representing the dissi...Figure 7.4 Numerical example of a realization of the stochastic processes
...Figure 7.2 Dissipated power measured in watts as a function of the constant ...Figure 7.3 Data layer with four cyber elements: three representing the dissi...Figure 7.4 Numerical example of a realization of the stochastic processes 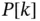 ...Figure 7.5 Self‐developing electric circuit: impact of decision rules and in...
...Figure 7.5 Self‐developing electric circuit: impact of decision rules and in...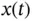 .Figure 8.3 Schematic of a system
.Figure 8.3 Schematic of a system 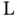 whose input signal is
whose input signal is 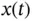 and output signal...Figure 8.4 RC circuit with an input signal
and output signal...Figure 8.4 RC circuit with an input signal 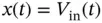 and an output
and an output