Cloud Computing Solutions
Здесь есть возможность читать онлайн «Cloud Computing Solutions» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Cloud Computing Solutions
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:3 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 60
- 1
- 2
- 3
- 4
- 5
Cloud Computing Solutions: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Cloud Computing Solutions»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
The main purpose of this book is to include all the cloud-related technologies in a single platform, so that researchers, academicians, postgraduate students, and those in the industry can easily understand the cloud-based ecosystems.
Audience
Cloud Computing Solutions — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «Cloud Computing Solutions», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
This kind of grid may contain servers, workstations, and data centers. All the components are acquired and used by a single department or administrative domain. When the need for resources increases, multiple cluster grids work together to make an enterprise grid. Multiple administrative domains may share the resources when they are in enterprise grids located in the same geographic location. Meanwhile, in contrast to enterprise grids, global grids are a compilation of enterprise grids. Each of them agree upon universal usage policies and protocols but it is not mandatory that executions will be the same. Users have the authority to use the distributed resources anywhere in the world.
1.3.3 Architecture of Grid Computing Environment
This subsection describes the layered grid architecture used to distinguish prerequisites for general classes of parts. Parts inside each layer share regular qualities yet can expand upon the capacities and practices given by any lower layer.
Figure 1.6depicts the layered framework, namely the fabric layer (interfacing local control), connectivity layer (communicating layer), resource layer (sharing single resources), collective layer (coordinates several resources), and application and protocol layer [11-18]. Each of the layers is discussed below.
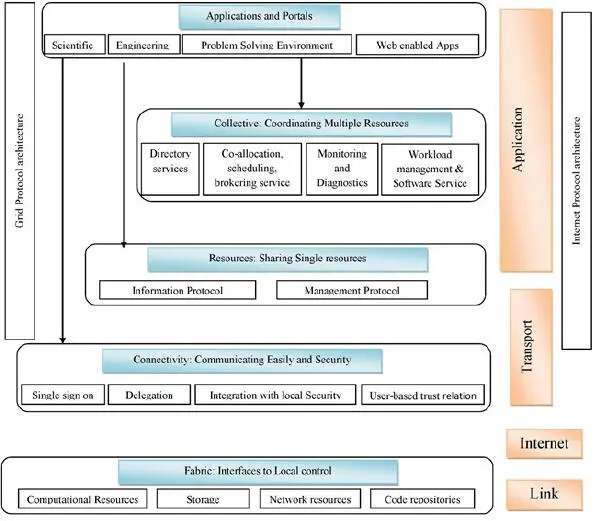
Figure 1.6 : Schematic diagram of layered grid architecture.
1.3.3.1 Fabric: Interfaces to Local Control
Fabric interface and local control provide the physical resources that are distributed and are the intermediate layer of grid protocols such as storage systems, computable artifacts, network resources, catalogs and sensors. A “resource” is defined as a logical part, like a computer cluster, distributed file system, or distributed computing pool; particularly in some areas, a resource execution might include internal protocol. In any case, these are not the concern of the grid framework.
Computational resources: Techniques are fundamental for initializing projects and for observing and governing the implementation of the subsequent processes. Administration instruments which permit screening and taking over the physical and computational resources designated for processes are required, as are time components approved ahead of time. Inquiry capacities are attractive for deciding equipment and programming qualities and pertinent state data; for example, current load and queue state due to scheduler-managed artifacts.
Storage resources: Methods are necessary for using and taking over files. Management methods that permit taking over the physical resources distributed and provisioned for information exchanges (network bandwidth, space, disk bandwidth, CPU) are very functional, and are an advanced reservation policy. For determining software and hardware characteristics, inquiry functions are required and an applicable load of data like bandwidth utilization and available storage is also needed for those reasons.
Network resources: Management methods that confer the authority of the resources which are assigned to network transfers (e.g., reservation, prioritization) might be fruitful. Inquiry functions are required for resolving network features and load.
Code repositories: This method for managing source and object coding is used by the specialized form of storage resource, e.g., a control system.
Catalogs: They are a particular type of repository that store resources and require a method for executing catalog query and update operations, e.g., a relational database.
1.3.3.2 Connectivity: Communicating Easily and Securely
Connectivity layer has validation and approval protocols which are required for grid specific network exchanges and furthermore characterizes center correspondence strategies. Correspondence protocols are required for the trading of information between texture layer assets. Correspondence necessities incorporate routing, transport and naming. Confirmation protocols are required for correspondence administrations for giving secure instruments to approve the validation of clients and assets. Connectivity layer gives validation administrations which have the accompanying qualities:
Single sign on: Clients must have the capacity to approve themselves (“sign on”) just once and after that they simply approach numerous grid assets depicted in texture layer.
Delegation: The user should have the ability to run a program for its own benefit, with the goal of finding out whether the program is fit to get the grid resources which the verified user is entitled to.
Integration with various local security solutions: All sites and resource suppliers ought to be incorporated with different nearby security arrangements. Grid security arrangements must have the capacity to consolidate with different nearby security arrangements and enable mapping to the local condition.
User-based trust relationships: In the event that the user has the privilege to utilize the artifacts from unmistakable locales or resource suppliers, the user ought to have the capability of using destinations together without requiring connection with the overseers of suppliers.
1.3.3.3 Resource: Sharing Single Resources
The resource layer lies above the connectivity layer correspondence and verification conventions to recognize conventions for the inception, checking, secure negotiation, accounting, control and payment of distributed operations of singular resources. Resource layer executes these conventions in the texture layer for controlling neighborhood resources. Two key classes of resource layer conventions could be striking:
Information protocol: These conventions are used in getting information of the structure and states of assets like the use governing policy, current load and its outline.
Management protocols: These protocols are used in negotiating access to shared physical resources, specifying resource requirements and monitoring tasks to be executed. A protocol might hold up monitoring the current state of an operation and while executing controlling operations.
1.3.3.4 Collective: Coordinating Multiple Resources
The following layers are engaged towards the protocols and services which are related along universal resource and cooperate with assembling of resources. This is the reason we called the following layer of the grid engineering the collective layer.
Directory services: Enables its clients to ask questions for artifacts by type, accessibility or load-sharing demand. Resource-level protocol is utilized in building indexes.
Scheduling, co-allocation and brokering service: This service enables members to ask for distribution of assignments of at least one physical resource for a specific reason and the scheduling of undertakings for appropriate resources.
Monitoring and diagnostic services: These specific applications screen asset designation, overload management, and additionally keep considerations regarding the assaults.
Data replication services: It supports the capacity management to expand the data received to execute and limit the reaction time and money.
Workload management systems: These systems deal with the utilization, depiction, status of the errand and multi-component work processes.
1.3.3.5 Application Layer
The end layer of grid framework is the application layer which interacts with the end users. According to the user applications, physical resources are provisioned and properly used by the applications.
Читать дальшеИнтервал:
Закладка:
Похожие книги на «Cloud Computing Solutions»
Представляем Вашему вниманию похожие книги на «Cloud Computing Solutions» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «Cloud Computing Solutions» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












