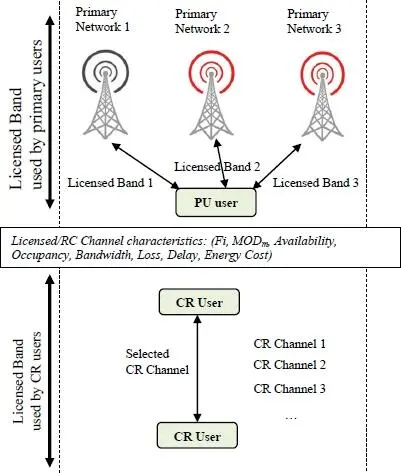
Figure 1.2. General context of decision-making
The suggested multicriteria decision-making module is based on the concept of utility to reduce the complexity of such a decision. The utility function used to calculate the scores is U (x) =1− e–αx with x the parameter of the decision vector and α its corresponding weight ( α > 0). For x ≥ 0, U ( x ) ∈ [0, 1].
The suggested selection algorithm is formed of the following stages. The first stage consists of verifying the availability of the different channels detected to eliminate poor candidates that have an availability probability below a defined threshold or whose availability time is less than a given duration. This preselection makes it possible to avoid unhelpful score calculation. At the second stage, the channels selected during the first stage are classed according to their energy scores. At the third stage, the decision-making module calculates the QoS score for each selected channel. After having calculated scores linked to QoS and to energy, the total score is calculated for each channel selected depending on the weight given to each aspect considered: QoS and energy. This is stage 4. The attribution of weight to criteria should reflect the importance of each decision-making criteria depending on the overall context (application, battery, etc.). Finally, the selected channel will be the candidate with the highest total score.
1.4.2.1. Stage 1: selecting available access networks/CR channels
In the M-RAN context, this processing stage is very simple. In fact, each access network detected is available. However, in a CRN context, this stage requires the following processing. First of all, it involves checking the availability of the current channel k and determining the probability Pr( Ck ( t ) = 0) that the channel k will be inactive at instant t . The secondary user should switch to a new channel when the availability of the current channel is lower than the probability threshold ( equation [1.5]):
[1.5] 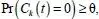
where Ck ( t ) represents the current channel k , which is a binary random variable with the values 0 and 1 representing the inactive and the occupied states, respectively.
τL is the probability threshold below which a channel is considered occupied and the secondary user should be allocated a spectrum handoff (Song and Xie 2012), that is, the current channel is no longer considered inactive at the end of transmission from the frame.
Then, for each channel i detected, it remains to determine the probability of inactivity and the average availability of the channel for the next period.
The candidate channel i is considered inactive for the next period when Pr ( Ci ( t ) = 0) ≥ τH , where τH is the probability threshold for a channel to be considered inactive at the end of the current frame (Song and Xie 2012). Thus, the preselected channels are those that have a probability 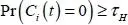 and an average duration of availability higher than a threshold
and an average duration of availability higher than a threshold 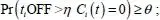 ti OFF represents the duration of the OFF period of the channel i .
ti OFF represents the duration of the OFF period of the channel i .
To support at least one SU frame, the probability that the activity duration of the i th channel will be longer than one transmission time of the frame η should be higher than or equal to θ . θ is the probability threshold for a channel to be considered inactive for the next frame transmission (Song and Xie 2012).
Thresholds τL and τH are not fixed arbitrarily. The choice of these thresholds can have an impact on the number of channels filtered during this stage. For this, we will choose both these thresholds depending on the radio context, again, such as the noise that characterizes this environment or the inactivity of primary users. For example, when there are very few channels considered available, we can lower the value of τL = τH . On the contrary, if these channels are very numerous, the value of τL = τH will be increased further. This will make it possible not only to select the channels with a high probability of availability, but also to reduce the number of candidates for which the decision-making module should run the remainder of the processing (calculation of different scores and decisions). Thus, making the right choice from among these thresholds will directly impact the efficiency of the approach retained as well as its global cost (CPU, memory, energy, etc.). We note that in some cases, τL could be different from τH .
1.4.2.2. Stage 2: classifying channels depending on the energy cost of the transmission models
Our aim is to minimize energy consumption by choosing the channels that use least energy. To do this, we classify the candidate channels depending on their energy score.
On each Ci channel, it is possible to transmit with the help of m modulations Mm . (MOD) im designates the transmission models possible on each channel Ci , where i represents the channel and m designates the modulation schema and the coding. Because the transmission power of the object has an impact on energy consumption, we suggest evaluating the transmission cost of the transmission models per available channel (MOD) im . This makes it possible to select the channel that most reduces energy consumption and so prolongs the battery life. In fact, the higher the transmission power, the better the signal-to-noise ratio, but a higher transmission power also means greater energy consumption (Krief 2012).
To select the most appropriate channel, the multicriteria decision-making module suggested should (1) calculate the minimum transmission power needed to transmit correctly on a given channel Ci with a modulation Mm , toward the other pair that could be an access point (M-RAN context) or another object (CRN context ), and (2) eliminate the transmission models (MOD) im necessitating a minimal transmission power greater than the device’s maximum transmission power.
To avoid rerunning the calculations at each execution of the selection algorithm, we suggest making calculations upstream and to store them within each object or on a remote device (Fog, Cloud, etc.). In fact, the minimum transmission power for each possible transmission model (channel, modulation) is calculated for different distances and stored on a Fog or Cloud device accessible to the objects.
The energy score is calculated according to the energy cost of a candidate channel and the battery life of the IoT device. For a given modulation and coding schema, the energy cost of a candidate channel is the average energy consumed per bit for the transmission on the channel. The energy cost of data transmission from the application j on this channel i (written Ci,j ) is calculated depending on the band frequency, the uplink channel rate and the data flow from application (packet size and packet interarrival time). However, in the context of video streaming, other parameters can be considered to estimate this cost, such as video quality, the number of users and the quality of the channel (Zou et al. 2017).
Читать дальше


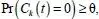
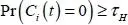 and an average duration of availability higher than a threshold
and an average duration of availability higher than a threshold 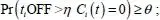 ti OFF represents the duration of the OFF period of the channel i .
ti OFF represents the duration of the OFF period of the channel i .










