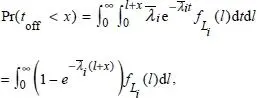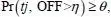The parameters that will be predicted at the period t + 1 are channel availability and the average channel availability time.
1.4.1.2.1. Probability of channel availability at period t + 1
In a CRN context, according to the analytical model defined in Song and Xie (2012), the predicted probability that a candidate channel i is inactive at time t can be expressed as follows ( equation [1.1]):
[1.1] 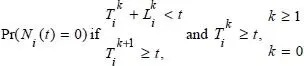
where 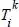 represents the arrival time of the k th packet and designates the length of the k th PU packet (data from one primary user) on the channel i . Ni ( t ) represents the state of the channel, which is a random binary variable with values 0 and 1 representing, respectively, the inactive and the occupied states.
represents the arrival time of the k th packet and designates the length of the k th PU packet (data from one primary user) on the channel i . Ni ( t ) represents the state of the channel, which is a random binary variable with values 0 and 1 representing, respectively, the inactive and the occupied states.
The probability that the channel i is in active at an instant t can be obtained by equation [1.2]:
[1.2] 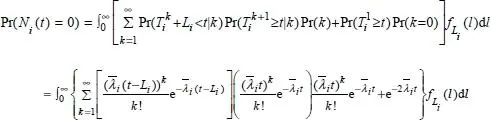
where 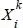 represents the interarrival of the PU packets. Supposing that the PU packets arrive following a Poisson process (Wang and Wang 2008), distributed exponentially with the average packet arrival rate per second λi , the length of the PU packet following fLi (l) .
represents the interarrival of the PU packets. Supposing that the PU packets arrive following a Poisson process (Wang and Wang 2008), distributed exponentially with the average packet arrival rate per second λi , the length of the PU packet following fLi (l) .
Based on the prediction above, the candidate channel i is considered inactive for the following time interval when Pr ( Ni ( t ) = 0) ≥ τ H, where τ His the probability threshold for a channel to be considered inactive at the end of the current frame.
1.4.1.2.2. Average channel availability time
In an intelligent radio context, we used the model suggested by Song and Xie (2012) to predict the average channel availability time at instant t . The OFF period represents the period the channel is unavailable. For the i th channel, the cumulative distribution function (CDF) over the duration of the OFF period is given by equation [1.3]:
[1.3] 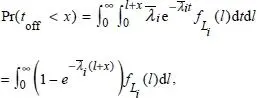
where t offrepresents the duration of the OFF period.
In order to support at least one SU packet (data from a secondary user), the probability that the inactive duration of the i th channel is longer than a transmission time of the frame η should be greater than or equal to θ (see equation [1.4]):
[1.4] 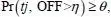
where θ is the probability threshold for a channel to be considered inactive for the next packet transmission.
1.4.1.3. Object characteristics
An object is characterized by the emission power PTx and state of its battery. The battery state or its remaining life (expressed in hours) can be calculated (Grace et al. 2009) on the basis of the battery’s capacity, its tension, its emission power and the constant K, which represents the power required for signal treatment.
1.4.1.4. Network monitoring module
In the M-RAN context, the network monitoring module provides information on the available access networks. These available access networks have different characteristics in terms of bandwidth, delay, loss rate, channel occupation rate and energy expenditure. The information collected (Carneiro et al. 2009) is analyzed to take a specific decision based on the services required.
The input metrics needed by the suggested multicriteria decision-making module include the characteristics of the access network or radio channel, the characteristics of the object, application requirements, users’ QoS preferences and the energy constraints and user sensitivity to some bands that could interfere with medical equipment in an e-health context, for example. All this information is stored in the databases. We distinguish types of input parameters: the measured, predicted and static parameters. The detection module for the intelligent radio and the monitoring module in the M-RAN context provide measured parameters. The prediction module will be responsible for predicting channel availability and the average duration for which they are available. The static parameters include fixed characteristics of the network or radio channel, user preferences and application requirements. The application needs we retain are linked to the QoS required by the application, such as the minimal bandwidth, the maximum delay allowed, the maximum jitter tolerated m and the maximum packet loss rate tolerated.
1.4.1.6. Multicriteria decision-making module
Depending on the needs of the application (data type, transmission urgency), the spectrum availability and the remaining battery life, the multicriteria decision-making module will select the most appropriate access network or radio channel to ensure transmission. This module considers both the energy constraints and the QoS and will be detailed in section 1.4.2.
To ensure decision stability, which is an important criteria (Wang et al. 2014), and to avoid inefficient or unhelpful transfer decisions in both the contexts considered (M-RAN or CRN), we suggest using a waiting time (timer) between the selection and execution stages. At the end of this time, the device checks that the following conditions are still valid: (1) the network/candidate channel is still detected by the object, and (2) this candidate’s score (network/channel) is still higher than that of the current network/channel. If these conditions are verified, then the transfer (network or channel) is run, otherwise it is canceled and the selection process restarts from the beginning.
As this wait can be an obstacle to continuity of service, a compromise needs to be found. So, we suggest adjusting this waiting time depending on the context of the decision.
1.4.1.7. Module for running vertical handover/spectrum handoff
The running stage refers to establishing the connection with the new access network (M-RAN context) or changing channel/transmission parameters (CRN context). In the M-RAN context, three cases are possible so long as the old link is released before (Hard Handover), during (Seamless Handover) or after (Soft Handover) the new link is established.
1.4.2. Decision-making flowchart
The decision-making module, detailed in section 1.4.1, makes it possible to select the most appropriate access network (M-RAN) or the radio channel (CRN). This selection depends on many contextual parameters, which include characteristics of the radio environment, application needs, object capacities, etc. In our case, selecting an access network or CR channel means selecting all the parameters that characterize transmission. In fact, an access network can be considered as one candidate channel among others. This is a key element for guaranteeing that our suggestion functions in all possible cases (as Figure 1.2 shows). The n candidate networks/channels detected are written C 1, C 2, C 3, …, Cn . On each channel ( Ci ), it is possible to transmit with the help of m modulations M 1, Mj , Mm . Each Ci channel (Figure 1.2) is characterized by the probability of availability Ai , the occupation rate Oi , the bandwidth, the delay, the loss and the energy cost. Each channel is also characterized by one or more transmission models (MOD i,m , where i designates the channel and m designates the modulation and coding).
Читать дальше

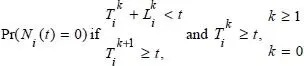
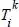 represents the arrival time of the k th packet and designates the length of the k th PU packet (data from one primary user) on the channel i . Ni ( t ) represents the state of the channel, which is a random binary variable with values 0 and 1 representing, respectively, the inactive and the occupied states.
represents the arrival time of the k th packet and designates the length of the k th PU packet (data from one primary user) on the channel i . Ni ( t ) represents the state of the channel, which is a random binary variable with values 0 and 1 representing, respectively, the inactive and the occupied states.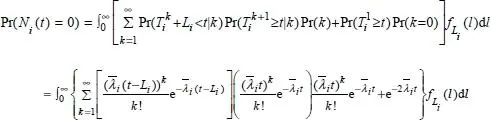
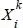 represents the interarrival of the PU packets. Supposing that the PU packets arrive following a Poisson process (Wang and Wang 2008), distributed exponentially with the average packet arrival rate per second λi , the length of the PU packet following fLi (l) .
represents the interarrival of the PU packets. Supposing that the PU packets arrive following a Poisson process (Wang and Wang 2008), distributed exponentially with the average packet arrival rate per second λi , the length of the PU packet following fLi (l) .