In the netfilter implementation with iptables, this complexity disappears completely. For a service to be routed across the firewall host, but not terminate on the local host, only two rules are required: one each for the forward and the reverse directions in the forward chain. This is the obvious way to design firewalling rules, and will serve to simplify the design of firewall configurations immensely.
Figure 9.9: Datagram processing chain in netfilter
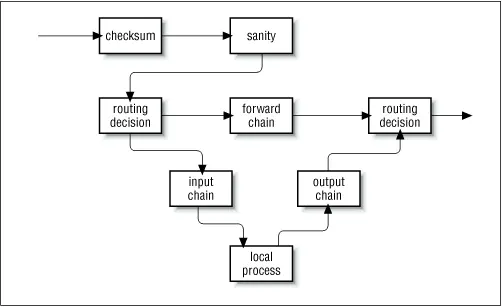
The PACKET-FILTERING-HOWTO offers a detailed list of the changes that have been made, so let's focus on the more practical aspects here.
Backward Compatability with ipfwadm and ipchains
The remarkable flexibility of Linux netfilter is illustrated by its ability to emulate the ipfwadm and ipchains interfaces. Emulation makes transition to the new generation of firewall software a little easier.
The two netfilter kernel modules called ipfwadm.o and ipchains.o provide backward compatibility for ipfwadm and ipchains. You may load only one of these modules at a time, and use one only if the ip_tables.o module is not loaded. When the appropriate module is loaded, netfilter works exactly like the former firewall implementation.
netfilter mimics the ipchains interface with the following commands:
rmmod ip_tables
modprobe ipchains
ipchains …
The iptables utility is used to configure netfilter filtering rules. Its syntax borrows heavily from the ipchains command, but differs in one very significant respect: it is extensible . What this means is that its functionality can be extended without recompiling it. It manages this trick by using shared libraries. There are standard extensions and we'll explore some of them in a moment.
Before you can use the iptables command, you must load the netfilter kernel module that provides support for it. The easiest way to do this is to use the modprobe command as follows:
modprobe ip_tables
The iptables command is used to configure both IP filtering and Network Address Translation. To facilitate this, there are two tables of rules called filter and nat . The filter table is assumed if you do not specify the -t option to override it. Five built-in chains are also provided. The INPUT and FORWARD chains are available for the filter table, the PREROUTING and POSTROUTING chains are available for the nat table, and the OUTPUT chain is available for both tables. In this chapter we'll discuss only the filter table. We'll look at the nat table in Chapter 11
The general syntax of most iptables commands is:
iptables command rule-specification extensions
Now we'll take a look at some options in detail, after which we'll review some examples.
There are a number of ways we can manipulate rules and rulesets with the iptables command. Those relevant to IP firewalling are:
- A chain
Append one or more rules to the end of the nominated chain. If a hostname is supplied as either a source or destination and it resolves to more than one IP address, a rule will be added for each address.
- I chain rulenum
Insert one or more rules to the start of the nominated chain. Again, if a hostname is supplied in the rule specification, a rule will be added for each of the addresses to which it resolves.
- D chain
Delete one or more rules from the specified chain matching the rule specification.
- D chain rulenum
Delete the rule residing at position rulenum in the specified chain. Rule positions start at 1 for the first rule in the chain.
- R chain rulenum
Replace the rule residing at position rulenum in the specific chain with the supplied rule specification.
- C chain
Check the datagram described by the rule specification against the specific chain. This command will return a message describing how the chain processed the datagram. This is very useful for testing your firewall configuration and we will look at it in detail later.
- L [chain]
List the rules of the specified chain, or for all chains if no chain is specified.
- F [chain]
Flush the rules of the specified chain, or for all chains if no chain is specified.
- Z [chain]
Zero the datagram and byte counters for all rules of the specified chain, or for all chains if no chain is specified.
- N chain
Create a new chain with the specified name. A chain of the same name must not already exist. This is how user-defined chains are created.
- X [chain]
Delete the specified user-defined chain, or all user-defined chains if no chain is specified. For this command to be successful, there must be no references to the specified chain from any other rules chain.
- P chain policy
Set the default policy of the specified chain to the specified policy. Valid firewalling policies are ACCEPT, DROP, QUEUE, and RETURN. ACCEPT allows the datagram to pass. DROP causes the datagram to be discarded. QUEUE causes the datagram to be passed to userspace for further processing. The RETURN target causes the IP firewall code to return to the Firewall Chain that called the one containing this rule, and continue starting at the rule after the calling rule.
Rule specification parameters
There are a number of iptables parameters that constitute a rule specification. Wherever a rule specification is required, each of these parameters must be supplied or their default will be assumed.
- p [!]protocol
Specifies the protocol of the datagram that will match this rule. Valid protocol names are tcp, udp, icmp, or a number, if you know the IP protocol number. [64] Take a look at /etc/protocols for protocol names and numbers.
For example, you might use 4 to match the ipip encapsulation protocol. If the! character is supplied, the rule is negated and the datagram will match any protocol other than the specified protocol. If this parameter isn't supplied, it will default to match all protocols.
- s [!]address[/mask]
Specifies the source address of the datagram that will match this rule. The address may be supplied as a hostname, a network name, or an IP address. The optional mask is the netmask to use and may be supplied either in the traditional form (e.g., /255.255.255.0) or in the modern form (e.g., /24).
- d [!]address[/mask]
Specifies the destination address and port of the datagram that will match this rule. The coding of this parameter is the same as that of the -s parameter.
- j target
Specifies what action to take when this rule matches. You can think of this parameter as meaning "jump to." Valid targets are ACCEPT, DROP, QUEUE, and RETURN. We described the meanings of each of these previously in the "Commands" section. You may also specify the name of a user-defined chain where processing will continue. You may also supply the name of a target supplied by an extension. We'll talk about extensions shortly. If this parameter is omitted, no action is taken on matching datagrams at all, other than to update the datagram and byte counters of this rule.
- i [!]interface-name
Specifies the interface on which the datagram was received. Again, the! inverts the result of the match. If the interface name ends with " + " then any interface that begins with the supplied string will match. For example, -i ppp+ would match any PPP network device and -i! eth+ would match all interfaces except ethernet devices.
Читать дальше




![Andrew Radford - Linguistics An Introduction [Second Edition]](/books/397851/andrew-radford-linguistics-an-introduction-second-thumb.webp)








