Graphical system- and process-monitoring tools that come with Fedora include the following:
► vncviewer — AT&T's open source remote session manager (part of the Xvncpackage), which can be used to view and run a remote desktop session locally. This software (discussed in more detail in Chapter 15, "Remote Access with SSH") requires an active, background, X session on the remote computer.
► gnome-nettool — A GNOME-developed tool that enables system administrators to carry out a wide range of diagnostics on network interfaces, including port scanning and route tracing.
► ethereal — This graphical network protocol analyzer can be used to save or display packet data in real time and has intelligent filtering to recognize data signatures or patterns from a variety of hardware and data captures from third-party data capture programs, including compressed files. Some protocols include AppleTalk, Andrew File System (AFS), AOL's Instant Messenger, various Cisco protocols, and many more.
► gnome-system-monitor — This tool is a simple process monitor offering three views: a list view, a moving graph, and a storage status overview. To access it, choose Applications, System Tools, and select the System Monitor entry (see Figure 12.3).
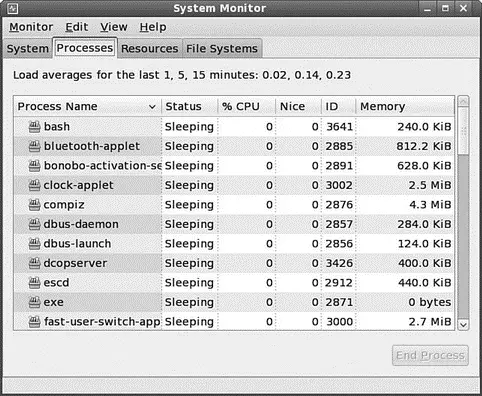
FIGURE 12.3 The Process Listing view of the System Monitor.
From the Process Listing view (chosen via the Processes tab in the upper-left portion of the window), select a process and click More Info at the bottom left of the screen to display details on that process at the bottom of the display. You can select from three views to filter the display, available in the drop-down View list: All Processes, My Processes (those you alone own), or Active Processes (all processes that are active).
Choose Hidden Processes under the Edit command accessible from the top of the display to show any hidden processes (those that the kernel does not enable the normal monitoring tools to see). Select any process and kill it with End Process.
You can change the nice value of the processes by selecting Edit, Change Priority. The View selection from the menu bar also provides a memory map. In the Resources tab, you can view a moving graph representing CPU and memory use (see Figure 12.4).
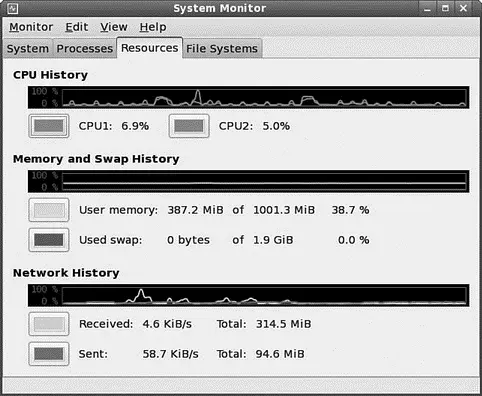
FIGURE 12.4 The Graph view of the System Monitor. It shows CPU use, memory/swap use, and disk use. To get this view, select the Resources tab.
Finally, you can see the status of your file system and storage devices by clicking the File Systems tab shown in Figure 12.5.
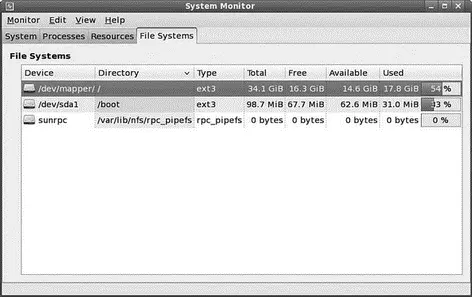
FIGURE 12.5 Keep a close eye on your free disk space.
KDE Process- and System-Monitoring Tools
KDE provides several process- and system-monitoring clients. Integrate the KDE graphical clients into the desktop taskbar by right-clicking the taskbar and following the menus.
These KDE monitoring clients include the following:
► kdf — A graphical interface to your system's file system table that displays free disk space and enables you to mount and unmount file systems with a pointing device
► ksysguard — Another panel applet that provides CPU load and memory use information in animated graphs
► http://and.sourceforge.net/— Home page of the AND auto-nicedaemon, which can be used to prioritize and reschedule processes automatically.
► http://sourceforge.net/projects/schedutils/— Home page for various projects offering scheduling utilities for real-time scheduling.
► http://freetype.sourceforge.net/patents.html— A discussion of the FreeType bytecode interpreter patents.
► http://www.ethereal.com/— Home page for the Ethereal client.
► http://www.realvnc.com/— The home page for the Virtual Network Computing remote desktop software, available for a variety of platforms, including Fedora Core Linux. This software has become so popular that it is now included with nearly every Linux distribution.
This chapter examines the practice of safeguarding data through backups, restoring that same data if necessary, and recovering data in case of a catastrophic hardware or software failure. After reading this chapter, you will have a full understanding of the reasons for sound backup practices. You can use the information in this chapter to make intelligent choices about which strategies are best for you. The chapter also shows you how to perform some types of data recovery and system restoration on your own and when to seek professional assistance.
Choosing a Backup Strategy
Backups are always trade-offs. Any backup consumes time, money, and effort on an ongoing basis; backups must be monitored, validated, indexed, stored, and new media continuously purchased. Sound expensive? The cost of not having backups is the loss of your critical data. Re-creating the data from scratch costs time and money, and if the cost of doing it all again is greater than the cost associated with backing up, you should be performing backups. At the where-the-rubber-meets-the-road level, backups are nothing more than insurance against financial loss for you or your business.
Your first step in formulating and learning to use an effective backup strategy is to choose the strategy that is right for you. First, you must understand some of the most common (and not so common) causes of data loss so that you are better able to understand the threats your system faces. Then you need to assess your own system, how it is used and by whom, your available hardware and software resources, and your budget constraints. The following sections describe each of these issues in detail, and also offer some sample backup systems and discuss their use.
Files disappear for any number of reasons: They can be lost because the hardware fails and causes data loss; your attention might wander and you accidentally delete or over write a file. Some data loss occurs as a result of natural disasters and other circumstances beyond your control. A tornado, flood, or earthquake could strike, the water pipes could burst, or the building could catch on fire. Your data, as well as the hardware, would likely be destroyed in such a disaster. A disgruntled employee might destroy files or hardware in an attempt at retribution. And any equipment might fail, and it all will fail at some time — most likely when it is extremely important for it not to fail.
A Case in Point
A recent Harris poll of Fortune 500 executives found that roughly two-thirds of them had problems with their backups and disaster-recovery plans. How about you?
Data can also be lost because of malfunctions that corrupt the data as it attempts to write to the disk. Other applications, utilities, and drivers might be poorly written, buggy (the phrase most often heard is "still beta quality"), or might suffer some corruption and fail to correctly write that all-important data you just created. If that happens, the contents of your data file would be indecipherable garbage, of no use to anyone.
Читать дальше








![Andrew Radford - Linguistics An Introduction [Second Edition]](/books/397851/andrew-radford-linguistics-an-introduction-second-thumb.webp)






