Thomas Limoncelli - Time Management for System Administrators
Здесь есть возможность читать онлайн «Thomas Limoncelli - Time Management for System Administrators» весь текст электронной книги совершенно бесплатно (целиком полную версию без сокращений). В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: Старинная литература, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Time Management for System Administrators
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:4 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 80
- 1
- 2
- 3
- 4
- 5
Time Management for System Administrators: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Time Management for System Administrators»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
Time Management for System Administrators — читать онлайн бесплатно полную книгу (весь текст) целиком
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «Time Management for System Administrators», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
However, on a network with 100 or so hosts, this will find suspect machines very quickly.
We now have a very simple tool we can use during a worm attack. This doesn't replace a multi-thousand-dollar Intrusion Detection System or a good antivirus/antispyware/antiworm system, but it sure can help you pinpoint a problem when it is happening. Best of all, it's free, and you learned something about shell programming.
If you'd like to hone your shell programming skills, here are some mini projects you can try:
tcpdump outputs some informational messages to stderr. Is there a way to stop it from outputting those messages? If not, how could we get cleaner-looking output?
Turn this one-line command into a shell script. Put this in your bin directory so you can use it in the future.
Take the shell script and expand it so that you can specify which NIC to sniff or other options you find useful.
tcpdump can be programmed to only gather ARP "who-has" packets, so you can eliminate the grep command. Learn enough about tcpdump to do this.
tcpdump has the ability to replace the functionality of head -100. Learn enough about tcpdump to do this. Is it the exact same thing as head -100? Is it better or worse?
awk is a complete programming language. Eliminate the "grep" as well as the "head" arguments using awk . Why do you think I chose to do it in three processes instead of just letting awk do it all?
Using Microsoft Excel to Avoid Writing a GUI
Writing the GUI for an application can be 90 percent of the battle. Here's a lazy way to make the user interface: maintain the data in Microsoft Excel, but write a macro that uploads the data to a server for processing.
Once, I created an entire application this way. We had a web site that listed various special events. I was tired of updating the web page manually, but I knew the secretary wasn't technical enough to maintain the web site herself.
I started planning out a user interface that would let anyone do updates. It was grand—a big MySQL database with a PHP frontend that would let people log in, do updates, add new events, and so on. The system would then generate the web pages listing the events automatically. It was wonderful on paper, and I'm sure if I'd had 100 years to write the code, it would have been great.
Instead, I realized that only one person would actually be doing updates. Therefore, I gave her access to a spreadsheet that captured all the information that needed to be collected and to a macro that would save the file twice: once on the server as a tab-separated file and again as an XLS file. A process on the server would parse the tab-separated file and generate the web page automatically.
You can see the spreadsheet in Figure 13-2.
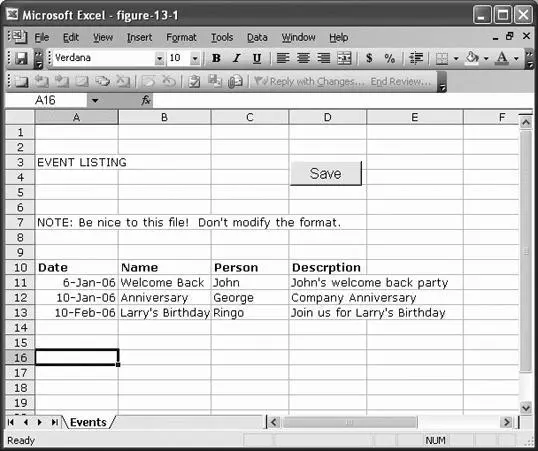
Figure 13-2. Event spreadsheet
Making the button takes a few steps.
First, use the macro recorder to do what you want:
Record the macro: Tools → Macro → Record New Macro.
Name the macro "Save."
Perform the actions to save the file as a tab-separated file on the network file server.
Save the file as an MS Excel Workbook ( .xls ) in your file area.
It is important that the last place you save the file is the richest format (Workbook) because this choice sets the default save format. If someone saves the file using File → Save, you want it to default to this format.
Click Stop on the macro record toolbar.
Next, create a button and attach the macro to it:
View the Forms toolbar: View → Toolbars → Forms.
Click on the Button (looks like a plain rectangle).
Draw a button where you want it to appear in the spreadsheet.
When asked, select the macro created earlier.
If you need to edit the button later, Ctrl-click it.
Now, test this by clicking the button. Voilà! It works! Check the dates on the files to make sure that the file really got saved twice. (Yes, it may ask you twice whether it's OK to replace the file. Click Yes.)
If you want to clean up the macro a bit, that's easy, too. In fact, one of the first things I did was edit exactly where the file gets saved:
Go to the macro editor: Tools → Macro → Macros.
Select the macro we just created and click Edit.
Save and exit when you are done.
Tip
In Microsoft macros, the line-continuation symbol is the underbar (_).
The final macro looks like this: Sub Save() ' ' Macro recorded 5/22/2005 by Thomas Limoncelli ' ActiveWorkbook.SaveAs Filename:= _ "Y:\calendar\EventList.txt", FileFormat:= _ xlText, CreateBackup:=False ActiveWorkbook.SaveAs Filename:= _ "Y:\calendar\EventList.xls", FileFormat:= _ xlNormal, Password:="", WriteResPassword:="", _ ReadOnlyRecommended:=False _ , CreateBackup:=False End Sub
Now that I have the tab-separated version being stored on a file server, it was easy to create a script that could pick up that file, extract out the useful lines, and generate the web page from it.
I have since used this technique in many situations in which I didn't want to have to write a user interface and the user already had MS Excel.
Letting Others Do Privileged Operations
Often we are asked to create a way for normal users to do things typically permitted only by an administrative account such as root . This can be quite dangerous and should be done with great care.
In Unix/Linux, there is a program called sudo that lets system administrators give a person the ability to run a command as another user. It is very restrictive, requiring the system administrator to configure it to specify exactly which user(s) can run which command(s) as which other user.
For example, you can configure it to permit a particular person to run a command as root . You can rely on sudo to make sure that only the people you specify have the ability to run this command as root , but it is important that the program check the parameters to make sure that privileged users are able to overstep their bounds.
Warning
Any kind of system that lets "normal" people do "privileged" operations is a risky system to build. Computer security history is fraught with well-meaning programmers accidentally creating security holes that let people run any command as root or administrator .
If you aren't sure what you are doing, research security books and FAQs for advice.
For example, if it requires root to run the Unix mount command to access a CD-ROM. It is a bad idea to configure sudo so that the person can run the mount command as root with any parameters. He could crash the system or break security. It is much better if you configure sudo to let the person run a new command (say, mountcd ) as root . This command will make sure that he has specified the particular CD-ROM drives that the user is permitted to mount (with a logical default), and mounts that drive. You also want to give him an ( unmountcd ) command.
I like to build three layers when I automate something for other people:
Layer 1. A program that does the basic task.
Layer 2. A program that the user will run, with sudo , that collects her input, validates it, makes sure she isn't trying to do anything fishy, and then calls the first program.
Layer 3. A more user-friendly way to access these previous layers, such as a web interface or menu program.
For example, at one company, we had a process for pushing a new version of the company web site to the world. It involved three different web servers (actually they were virtual servers on two different machines, but those details aren't important).
Читать дальшеИнтервал:
Закладка:
Похожие книги на «Time Management for System Administrators»
Представляем Вашему вниманию похожие книги на «Time Management for System Administrators» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «Time Management for System Administrators» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












