Then write " info "
Msf> info
Then write " set DOMAIN Microsoft.com"
Msf> set DOMAIN Microsoft.com
Then write "run"
Msf> run
You can use Maltego tool. When you run the program, choose company stalker, write the name of the company ie Microsoft.com. It will brings the email of the domain. Take the domain Microsoft.com, then click run transform.
You can use piple search or facebook.
You can use the website truecaller website to find the person of certain phone number .
You can use metadata collector tools. Two tools used, metagofil, FOCA
Metagofil tool is in backtrack. For example write
#/pentest/enumeration/google/metagoofilo
#./metagoofil.py –d Microsoft.com -t doc,pdf -l 200 –n 50 –o microsoftfiles –f results.com
It will bring many emails and other information.
You need to change downloader.py to be
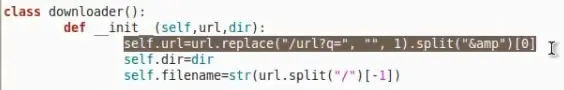
Use foca to download files from certain servers.
Use traceroute, tracert to traceout the connections in certain server.
There is tool called tcptraceroute can bypass firewalls.
You can use geospider as tracert tool.
You can use trout tool.
You can use visual ip trace.
You can use www.bing.comto see all the web sites on the web server. Write the Ip and you will get all websites in the same server.
To know the type of web server, we use whatweb tool in linux.
#./whatweb www.microsoft.com
We can use httprecon tool for same purpose to know the type of web server.
We can use the site news.netcraft.com to get all information about web server.
We can use the telnet command to know the type of web server
# telnet 192.168.1.1 80
# GET / HTTP / 1.0
We can use netcat in linux to know the type of web server.
# nc –n 192.168.28.139 80
# GET / HTTP / 1.0
We can use the tool httrack and wget for mirroring websites. You can use them to download and save websites.
We can use in backtack THCSSLCheck tool
# wine THCSSLCheck www.yahoo.com 443
Or use the tool sslscan
#sslscan www.cnn.com
To detect the load balancing, we use the tool lbd (load balance dector)
# ./lbd.sh www.yahoo.com
It will try to find whether it is load balancing server. It will find the type of server, whether dns or http. It will check the dns load balancing and the http load balancing. Then it will tell whether load balancing made by http or dns
You can detect the web application firewall. There is tool called wafw00f. The tool can detect some firewalls. Go to waffit in backtrack.
#./wafw00f.py www.contra.gr
Some websites can offer help in least time.Centralops.net can make service scan and network whois and domain whois and traceroute and find dns records. Other website can do the same purpose: network-tools.com and serversniff.net and mrdns.com.
On firefox, add passiverecon addon and you can get from it all information about the web site you are browsing.
Part 3: Scanning Methodology
Part 3 of Certified Ethical Hacker (CEH) Course
By
Dr. Hidaia Mahmood Alassouli
Hidaia_alassouli@hotmail.com
Part 3: Scanning Methodology
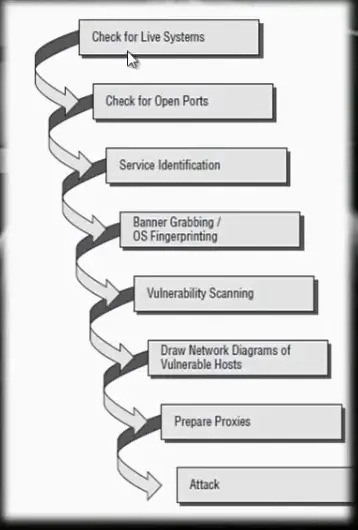
a) Scanning Methodology
The steps for hacking: Reconnaissance, Scanning, Gaining Access, Maintaining Access, Covering Tracks
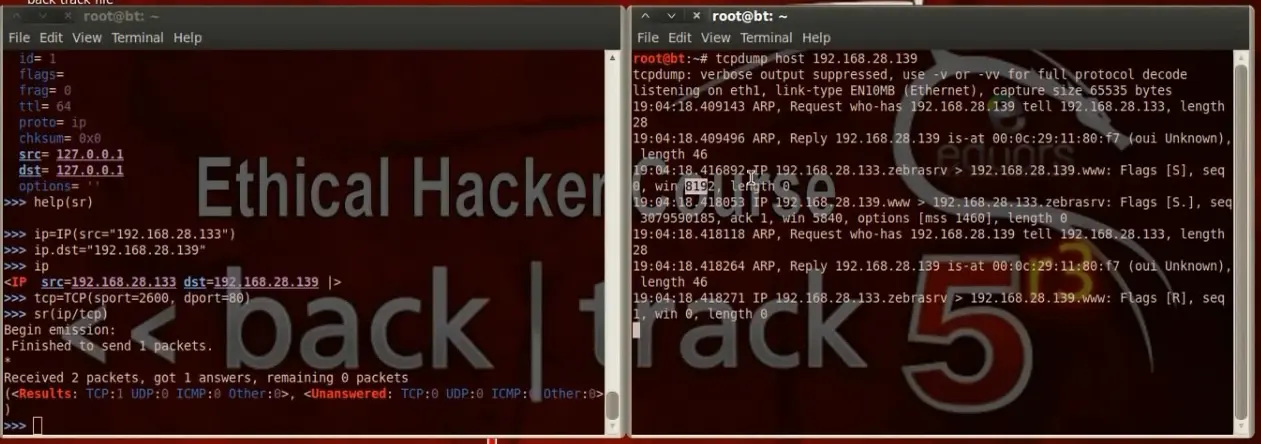
b) Understanding Packet Craft to Create Packet

Using scapy tool to send a packet

c) Understanding the ping sweep technique.
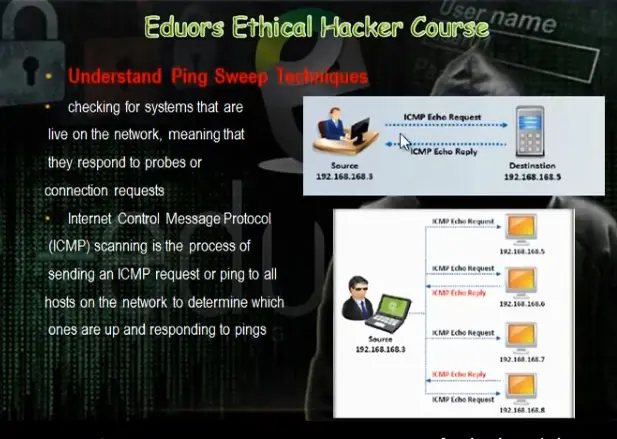
It will find which devices are actives in the network. There are many tools to make ping sweep: angry and hping and nmap.
Use nmap
#nmap –sn 192.168.28.0 /24
Use hping
Use in windows angry tools
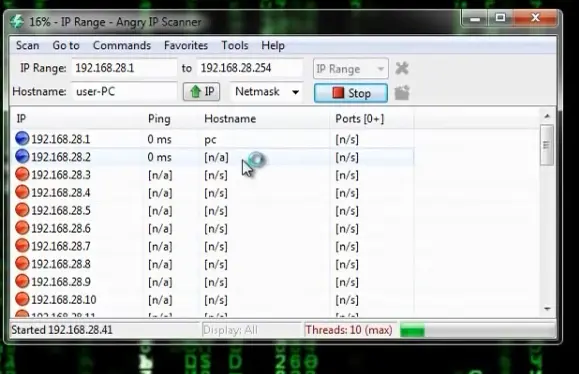
Use the nmap to know the open ports in a host

#nmap –sT 192.168.152.130 -p 80
Use the nmap to make scan on all ports
#nmap 192.168.152.130
Use the metasploit for same purpose
#msfconsole
Msf> search scanner/portscan
Msf> Use auxiliary/scanner/tcp
Msf> Info
Msf> Set RHOSTS 192.168.28.139
Msf> Set PORTS 1-1000
Msf> run
The problem if there is firewall we will not get results. In stealth scan or half open scan
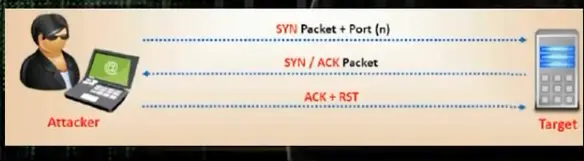
# nmap –sS 192.168.28.13 -p 80
Use the metasploit for same purpose
#msfconsole
Msf> search scanner/portscan
Use auxiliary/scanner/syn
Info
Set RHOSTS 192.168.28.139
Set PORTS 1-1000
Run
We can use the ACK to know the unfiltered ports on firewall

# nmap –sA 192.168.28.138 -p138
It will tell you it is unfiltered port in the firewall
Use the metasploit for same purpose
#msfconsole
Msf> search scanner/portscan
Use auxiliary/scanner/ack
Info
Set RHOSTS 192.168.28.139
Set PORTS 3380-3390
Run
It will tell you the unfiltered ports
The FIN scan is another way of scan. The computer sends FIN packet and if the host answered it, it is open port otherwise it is closed port

# nmap –sF 192.168.28.138 -p1-1000
The XMAS scan is another way of scan. The source machine sends FIN and URG and PUSH and if the destination did not answer, then the port open and if it did answer with RST then the port close.

# nmap –sX 192.168.28.138 -p80
Here the source machine sends TCP packet with NO flag set. If the destination did not answer, then the port open and if it did answer with RST then the port close.

# nmap –sN 192.168.28.138 -p80
Читать дальше

























