John Scilieri: Your friendship and mentorship over the years helped me make all the right decisions. Thank you for the copy of The Obstacle Is the Way, which motivated me to take a risk that paid off and opened my eyes to Stoicism.
Eric Kough: You gave my resume on Monster.coma chance and opened countless doors for me. I'm forever in debt.
Joe Karolchik: It was a privilege to have you as a leader and mentor to learn from.
Victor Goltsman: I'm so grateful for the opportunity I had to work with you, and I try to apply every day what I learned from you.
Security Tinkerers: Thank you to each and every one of you. I am extremely fortunate to be in your company.
Chris Castaldo is an industry-recognized chief information security officer (CISO) and expert in building cybersecurity programs for start-ups. Chris's cybersecurity experience stretches over 20 years in start-ups, Fortune 1000s, and the US Government. He has scaled cybersecurity programs and teams from the ground up, and he also advises start-ups. Chris is a US Army veteran and a Visiting Fellow at the National Security Institute at George Mason University's Antonin Scalia Law School.
Introduction
ABOUT THIS BOOK
Chapter 1will discuss and get you comfortable with building a minimally viable cybersecurity program for a minimally viable product. You don't need to start with National Security Agency (NSA) level security on day one, and most founders reading this book won't even need it the day they ring the opening bell.
Chapter 2will help you think through and build your cybersecurity roadmap regardless of where you are starting in the start-up life cycle. While it may seem out of order – why wouldn't you plan your roadmap first? – not everyone starts at the point of needing a roadmap, with a defined and documented strategy. If you are a month into building your minimally viable product (MVP) and just received your legal documents officially forming your company, a three-year cybersecurity roadmap is going to take up time and then sit on the shelf.
Chapter 3is, in my opinion, the most important chapter in this book. If you read one chapter only, make it this one. Your credentials, which make up a username and password, are your keys to your digital self. These are most critical to protect as they underpin nearly all other systems in a cybersecurity program.
Chapter 4will explore the ever-changing world of antivirus that began nearly 40 years ago and is now called endpoint detection and response (EDR) or endpoint protection platform (EPP). EDR and EPP is an important layer to your cybersecurity program, one that might be difficult to delay beyond the formation phase of your start-up.
Chapter 5tackles the necessary evil that is our office network, how we connect to the Internet. It makes all of this possible and is also first to be blamed when we can't load our favorite cat video on our office Wi-Fi network.
Chapter 6we soar into the sky and take a look at the clouds. It is nearly impossible to not use a cloud-based product today and as a founder there is a very good chance you are building a cloud-based product or will use them to scale your start-up.
Chapter 7covers the actual basics and predecessor to all of this, information technology (IT).
Chapter 8covers an equally critical topic to Chapter 3: hiring. Making your first cybersecurity hire is a high-impact decision for your start-up. The wrong hire can have disastrous consequences. And making sure you know what you are actually looking for, being honest with yourself and founders, will pay back dividends. Cybersecurity is one of the most competitive fields for jobs and has been for nearly a decade now.
Chapter 9is a personal favorite of mine. Not everyone enjoys the negotiating challenges of working with a customer's general counsel on terms and conditions, or arguing the auditor's definitions of “was.” Being compliant can sometimes mean you can or cannot do business in an industry, country, or with a specific business. This is a chapter you shouldn't skip.
Chapter 10continues and builds on Chapter 9and dives specifically into government law and industry regulations. These, much like being compliant with a legal agreement, can stop a start-up in its tracks or open the doors to prospective partner, acquirers and customers.
Chapter 11will prepare you for the day when people ask you if your product is secure and how you protect their data. It's a good idea to start thinking about these answers now and then look at your answers and verify that you are actually doing that. Someone will eventually want to audit you. Being ready to comfortably and confidently talk about your cybersecurity program will build a lot of trust with investors, customers, and partners.
Chapter 12will discuss the inevitable data breaches. They are a part of doing business today and we build our cybersecurity programs to the antifragile so we improve when they happen.
Chapter 13dives further into the technical needs for start-ups that are developing a technical solution, and covers baking cybersecurity into the product you are building, not just your start-up.
Chapter 14looks at outside risks of doing business today. Third-party vendors, really any vendor, you use will bring some risk to your business. The reward must simply outweigh that risk. This chapter will help you understand how to quickly evaluate that risk.
Chapter 15will bring us back to where we started and set you and your co-founders on the way to building a secure start-up.
This book is written specifically for founders to take immediate and continuous actions in their start-up to bake in cybersecurity. After each chapter, I will summarize the contents and highlights of the most critical takeaways. Additionally, there will be action plans that you can take immediately and as your start-up scales to implement those suggestions.
These plans will be broken out into generalized phases in your start-up journey from founding to exit. Obviously, not every company takes the same path, so specific catalysts will be mentioned and grouped in a way that may seem contradictory.
1 FormationOne to three foundersNo additional full-time staffAngel or friends and family or bootstrap funding
2 ValidationFounders + Key Strategic HiresMVP existsLighthouse/marquee customersSeed round funding
3 GrowthFounders + Key Strategic Hires + Engineering TeamsSeveral customersA series and beyond
We'll use these generalized stages in the life cycle of a start-up to delineate specific milestones and actions that you should consider taking. So as your start-up and product mature, so does your cybersecurity ( Figure I.1).
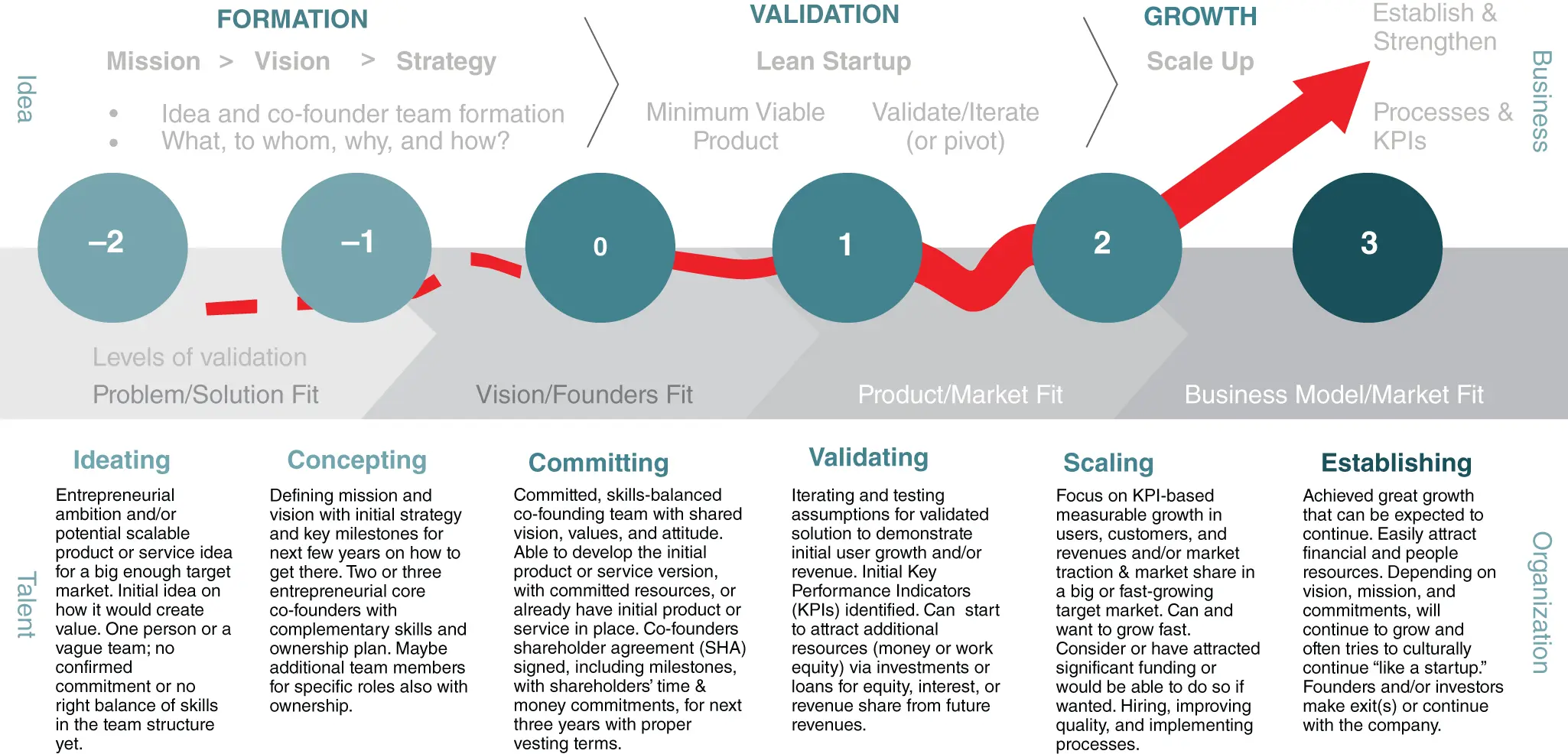
FIGURE I.1 Startup Development Phases – From Idea to Business and Talent to Organization
Source: Startup Key Stages by Startup Commons is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
PART ONE Fundamentals
CHAPTER ONE Minimum Security Investment for Maximum Risk Reduction
An ounce of prevention is worth a pound of cure.
– Benjamin Franklin
NO ONE PLANS ON THEIR START-UP not making it past a year of business, so you should also plan for your investment and planning in cybersecurity to scale into the future. While selecting the bare minimum may seem and feel counterintuitive and is certainly against the opinion of many cybersecurity professionals, it will ensure the continuation of the business.
Читать дальше













