Optical SensorThe optical sensors convert light beams into an electronic sign; it gauges a physical amount of light and changes into a coherent structure, possibly advanced structure. It recognizes the electromagnetic vitality and sends the outcomes to the units [17]. It includes no optical filaments. It is an extraordinary aid to the cameras on cell phones. Additionally, it is utilized in mining, substance industrial facilities, processing plants, and so forth. LASER and LED are the two distinct kinds of the light source. Optical sensors are fundamental pieces of numerous regular gadgets, including PCs, copiers, and light apparatuses that turn on consequently in obscurity. What is more, a portion of the basic applications incorporates alert frameworks, coordinated for photographic flashes, and frameworks that can recognize the nearness of articles [18].
Gas SensorA gas sensor or a gas identifier is a gadget that distinguishes the gas in a region, which is extremely useful in security frameworks. It is a rule, recognized a gas spill in a zone, that outcomes are sent to a control framework or a small-scale controller, that at long last closes down [19]. It can identify ignitable, combustible, and harmful gases.
The IoT architecture varies from their functional and their resolution. IoT engineering innovation principally comprises of four significant parts (Figure 3.3):
Sensor: Sensors are the contraptions that can verbalize, recognize, and process data over the framework. They may relate these sensors either through wired or remote. A large portion of the sensors needs availability through the sensor’s entry ways [20]. The association of sensors can be through a Local Area Network (LAN).
Gateway and Networks: A huge amount of information is delivered by this sensor and need fast entry ways and networks to interchange the material. This system can be type of LAN (Wi-Fi, Ethernet, etc.).
Cloud Service: Cloud goes under the management services which create the information through assessment, the leading group of the device, and security controls. Other than these safety controls and devices, the officials who use the cloud move the data to the end customer’s application, for instance, retail, healthcare, emergency, and energy.
Application Layer: The application layer actualizes the working of IoT. For this, an application is required with the relating gadget to finish the necessary assignment.
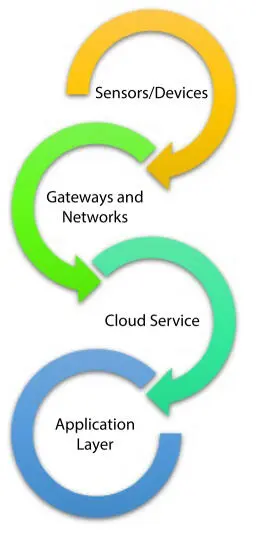
Figure 3.3IoT architecture.
3.5 Challenges and Issues in IoT
IoT has enough challenges and resolutions according to its behavior approach. In this section, our main approach is to understand the issues and use of the IoT accordingly.
Lack of Outdated DevicesThe use of outdated devices is the major factor to lack the security in IoT [21]. There should be advanced technology so that devices can communicate properly and well known about the recent threats.
Connectivity IssueThis is, perhaps, the most disregarded test since the information network has immensely improved. However, there still exist a few zones where information availability is an IoT usage challenge. It includes how IoT gadgets converse with the passage and the cloud and what information position does they create. Most IoT doors accessible are good with GPRS and Wi-Fi/LAN. In this way, the need is for a reasonable edge layer that interprets transport and information group conventions to send information to the IoT stage [22]. Defining the precise blend of these resolutions before ongoing with an IoT implementation will help in going far.
Information Security IssuesClients are uncertain about information security. There is additionally an opportunity of corporate secret activities to increase licensed innovation [23]. Thus, IoT specialist co-ops need to guarantee that their information
will be protected. It can take this information care by utilizing an extensive administration mode, which gives secure access to touch reports and information. This period of planning that defines different information related to security arrangements is critical for effective IoT execution.
Vulnerabilities
Ordinary hacking of prominent targets keeps this threat continually in the rear of our psyches. The results of treachery and disavowal of administration could be undeniably more genuine than a trade-off of protection [24]. Changing the blend proportion of disinfectants at a water treatment plant or halting the cooling framework at an atomic force plant may put an entire city in impending peril.
ScalabilityThis is not quite a bit of an issue; however, they bound it to turn into an issue essentially comparable to nonexclusive buyer cloud as the number of gadgets inactivity rises [25]. This will build the information limit required, and the time required for confirming exchanges.
Limited Sensor AvailabilityPrincipal sensor types, for example, temperature, light, movement, and laser scanner, are effectively accessible. Ongoing advances in microelectronics, combined with progress in strong state sensors, will make the uncovered sensors less of an issue [26]. The test will be in making them all the more separating in swarmed, uproarious, and increasingly complex situations. The use of calculations like fluffy rationale vows to make this less of an issue.
Analytics ChallengesWe comprehend the certified estimation of an IoT plan through huge encounters got from the assembled IoT data [27]. This demands an unrivalled assessment stage fit for dealing with the proportion of data to be added to the game plan at a later point. Data analytics accessories need to recall this while thinking up the IoT execution building to incorporate data planning, decontaminating, and depiction. Accordingly, enough space for extensibility to incorporate a nonstop or insightful assessment to an IoT game plan can help disentangle this fundamental IoT execution challenge.
Usage of Energy-Based EquipmentEnergy utilization is a significant issue in IoT giving an energy source they consider to different savvy questions and issue. Remote force innovations are an intriguing exploration region wherein force can be transmitted at some separation to the savvy objects [28]. Another exploration territory is a directing improvement in WSN to decrease energy utilization by choosing the best course.
3.6 Future Opportunities in IoT
Increased Usage of IoTWe expect the Web of Things gadgets, for example, machines and sensors to expand their use in 2025. IoT will develop at a compound yearly development pace of 22.5% from 2022 to 2025. IoT web innovation is the following significant advance in making the world an associated place.
6G IoT Need6G is energetic to the IoT or single scheme for millions of consumptions. In 10 years, time period from 2032 to 2040, IoT devices will grow over 160 billion, and the development from 5G to 6G in develop IoT is substantial. With a 5G organize, a solitary cell can deal with, up to one million gadgets.
Increased Client AdoptionNext 10 years, you will see an immense change in IoT when the move away will occur from the consumer-based IoT like the market lemon of robotics. The subsidizing development of the shopper-based IoT will diminish, and the future will be the year for the mechanical IoT foundation and stage [29]. This IoT trends will expect time to develop.
Smart Homes ConceptsBefore, we have seen the IoT applications have flooded with brilliant home innovation, and this will have proceeded in the blink of an eye so the home can get progressively intelligent [30]. Individuals would not immediate the gadgets; rather, the gadgets will mention to the individuals of the house what they ought to do.
Читать дальше













