Mike Wills - The Official (ISC)2 SSCP CBK Reference
Здесь есть возможность читать онлайн «Mike Wills - The Official (ISC)2 SSCP CBK Reference» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:The Official (ISC)2 SSCP CBK Reference
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:4 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 80
- 1
- 2
- 3
- 4
- 5
The Official (ISC)2 SSCP CBK Reference: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «The Official (ISC)2 SSCP CBK Reference»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
The Official (ISC)2 SSCP CBK Reference
SSCP Study Guide
The Official (ISC)2 SSCP CBK Reference
The Official (ISC)2 SSCP CBK Reference — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «The Official (ISC)2 SSCP CBK Reference», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
Proper software license management and software inventory management can often save money by eliminating duplicate or overlapping licenses, or by restricting usage of a particular app or platform strictly to where it's needed.
Data Storage
Whether you think of it as data or information , it is either in use, in motion, or being stored somewhere in the information architectures and systems you are keeping safe and secure. Data can be used by endpoints, servers, or the infrastructure itself. Data is in motion when it is being transferred across networks, communications links, or even to and from a storage device temporarily attached to an endpoint computer or smartphone. Data can be stored – be at rest – in endpoint devices, in removable media, and in storage subsystems that are part of an on-premise network or hosted in a public or hybrid cloud. Chapter 7, “Systems and Application Security,” will look in greater depth at security issues relating to data storage in the cloud and within your networks and their servers. What remains is the vexing problem of data storage on paper and on removable storage media and devices, and when those storage media and paper documents are being moved around.
Information Lifecycle
Information has a natural lifecycle, but as with most things in the IT world, there are many different models for this lifecycle, with different emphasis placed on different phases of the data's existence. For example, ISO 27002 defines this cycle with five phases: creation, processing, storage, transmission, and deletion/destruction (see Figure 1.2). Other models, such as those built into many systems management platforms such as SAP, may combine creation and use with processing; then add a retention phase in which the data is not actively used but cannot be disposed of because of legal, regulatory, or liability reasons; and finally end with a disposal and destruction activity.
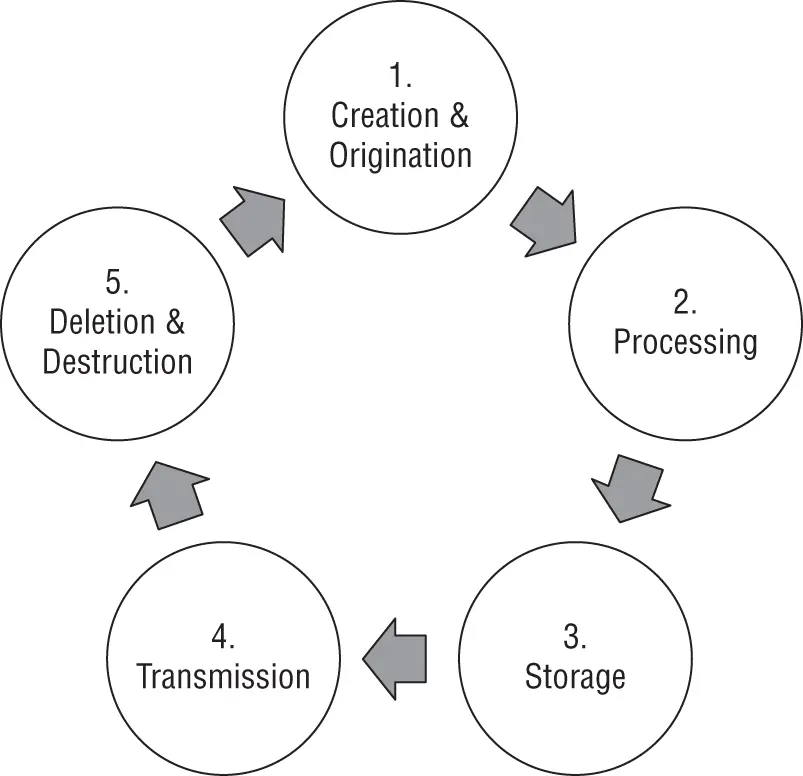
FIGURE 1.2 ISO 27002 phases
Security is an important consideration at every phase, but the level of importance can vary, depending on the phase. The formats and media used in the various phases can also affect the security considerations.
Consider, for example, design documents for a new product or technology. When those documents/data are new, they are valuable and actionable, especially if a competitor acquires them. Once the product or technology is in production and is being sold on the market, those same documents could be near the end of their lifecycle. At this point, one could argue that the documents would do less damage in the hands of a competitor, but they still need to be afforded some level of protection, right up to the moment they are destroyed. In this example, even though the creators have benefited from the “rush to market” advantage, the design documents themselves could still contain sensitive data, such as a proprietary production method, which the organization plans to reuse in future products.
There are several important points to take from this example. First, the security impact may vary depending on where the information is in its lifecycle. Next, even though the impact may vary, there can be negative outcomes for the organization at any phase. Finally, phase five, the deletion and destruction phase, is important because destruction of unneeded assets reduces the organization's attack surface. Data at the end of its lifecycle only introduces risk, with little to no benefit.
The lifecycle view shows that datasets (or information assets) are constantly going back and forth from storage to use; throughout that ever-repeating cycle, your systems designs should protect the information while it is at rest, in use, and in motion. Currently, well-chosen encryption systems can protect data in motion and at rest and by means of digital signatures offer the stored copies protection in time as well. ( Chapter 5goes into this in further detail.) However, thus far there are not many solutions to protect data while it is being used from compromise or loss, since most operations on data and its use by humans needs to have the meaning of the data readily available.
Apply Resource Protection Techniques to Media
Protecting the information on storage media requires that you can control or limit the onward use, copying, or other redistribution of that information; it also requires you to protect your systems from being contaminated by information from a classification level that does not belong on your systems. For example, the Biba and Bell–LaPadula access control models to show how different models emphasize confidentiality or integrity. Both choices can be undone by putting the wrong level of information onto the wrong removable media and then introducing that media into another system. You'll see a variety of standards and practices in use that may place different emphasis on protecting either the information (and its confidentiality, nonrepudiability, or integrity) or the systems (by protecting their integrity, and hence their availability and authenticity).
Before covering the methods for properly managing media, it's important to acknowledge that these methods will vary based on the types of media used. The umbrella term of media or information system media could mean legacy analog formats, such as hard-copy documents, photos, and microfilm. It could also (more likely) be in reference to a wide range of digital formats, such as external hard drives, floppy disks, diskettes, magnetic tape, memory cards, flash drives, and optical disks such as CDs, DVDs and Blu-Ray disks.
As you might expect, making secure but removable media work requires successfully integrating your security classification schema, your device-level identity management and access control, and the management of all endpoints' capabilities to use removable storage—including on the endpoint itself.
Marking
Handling sensitive or classified information involves everything necessary to meet its protection requirements; handling storage media refers to all processes, be they human, electronic, or mechanical, which are involved in mounting, dismounting, storing, shipping, using, reusing, and ultimately destroying the media. This protection requires a combination of marking the media and establishing and using administrative and logical processes that perform those tasks in controlled, reliable, and auditable ways. The marking achieves nothing without the procedures being understood and used properly!
Marking involves labeling in both human-readable and machine-readable manners so that it is immediately obvious what the highest security classification level of data on that media can be and should be. Humans are known to put “for unclassified use only” disks into drives and then write secret, proprietary, or private data to them, either deliberately as part of an exfiltration attempt or accidentally. The labeling should clearly link to the proper handling procedures for that level of security classification. Done properly, your device-level identity management and access control systems can then use this marking to authenticate the media when it is first mounted and then authorize each attempt to read or write data or metadata to it.
It's strongly recommended that your IT or security teams be the ones who purchase, label, initialize, and inventory storage media used for sensitive, proprietary or other data security classifications your company uses. When teamed with user-facing policy directives, this can significantly reduce the compromise of classified information due to a user forgetting to properly label a piece of media.
Читать дальшеИнтервал:
Закладка:
Похожие книги на «The Official (ISC)2 SSCP CBK Reference»
Представляем Вашему вниманию похожие книги на «The Official (ISC)2 SSCP CBK Reference» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «The Official (ISC)2 SSCP CBK Reference» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












