Cloud Computing Solutions
Здесь есть возможность читать онлайн «Cloud Computing Solutions» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Cloud Computing Solutions
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:3 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 60
- 1
- 2
- 3
- 4
- 5
Cloud Computing Solutions: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Cloud Computing Solutions»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
The main purpose of this book is to include all the cloud-related technologies in a single platform, so that researchers, academicians, postgraduate students, and those in the industry can easily understand the cloud-based ecosystems.
Audience
Cloud Computing Solutions — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «Cloud Computing Solutions», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
Figure 2.5: Software as a service (SaaS).
Programming services provided to the customers incorporate enterprise services close to work process administration, coordinated effort administration, digitized signature, supply chain management, programming conveyance services, financial administration, customer relationship management (CRM) and so on. Web 2.0 applications can include metadata administration, gateway services, social networking, blogs, etc.
To assist these service conveyance models, a few important services ought to be incorporated:
Service management and resource allocation, operations administration, SLA administration, QoS administration, specialized help and reinforcements.
Security administration which incorporates approval and confirmation, interruption avoidance, affirmation, control, review, infection insurance and firewalls.
Allied online support based on the client’s inclinations, personalized announcements.
Collaborating with and incorporating the services through heterogeneous field is also something to think about.
2.4.5 Network as a Service (NaaS)
Although not a hosted server/application cloud-based service model, we feel Network as a Service (NaaS) needs a quick introduction at this point. The NaaS model allows your business to outsource the day-to-day burden of running your wide area network (WAN) connectivity. You can even outsource your LAN infrastructure if required. The network provider becomes responsible for your overall network connectivity when using NaaS; theretofore, you can enjoy time and cost savings due to overall simplification and performance gains.
NaaS providers, such as Amber Networks, are also capable of providing hosted cloud services over high speed connections directly from their core network (“on net”). This means that the traffic for your hosted cloud services does not have to traverse the public internet, but rather travels directly from your site to your NaaS provider’s network, and then directly to your hosted cloud service.
2.4.6 Desktop as a Service (DaaS/VDI)
One further step that is becoming increasingly popular is removing most of the desktop support element from your local IT team by using the Desktop as a Service (DaaS) model. In this service model the provider hosts, manages and supports the virtual desktop infrastructure (VDI) environment and delivers that service securely either over the public internet or via a private network.
Your IT team can manage your own virtual desktop images and applications or have the provider perform that function for you.
2.4.7 Recovery as a Service (DRaaS)
The Recovery as a Service (RaaS) model (also known as DRaaS) allows you to use a single managed platform for all of your backup and disaster recovery needs. The RaaS provider’s platform will allow you to backup and recover server operating systems, applications and databases.
RaaS is a cost-effective backup model that can help your business reduce the impact of downtime due to hardware and application failure by providing backup services for critical data and applications. RaaS can replicate your production services to a diverse backup infrastructure, so transitioning to the backup environment is quick and seamless.
2.5 Security Paradigms and Issues of Cloud Computing
Cloud computing relies on a change in perspective with ramifications in computational issues. Ideal models moving to cloud computing are the fundamental mainstay of progress in traditional computational models for addressing problems concerning information security and protection. The various components concerned with security and protection types of problems are shown in Table 2.1and discussed below.
Table 2.1 : Shared responsibility model for security of cloud computing.
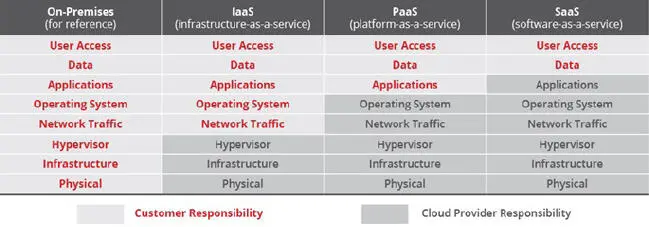
User information restrained by third-party service: Currently, domination is surrendered to the third-party services; thus, extraordinary security and protection problems concern allied unapproved ingress, information ingress restraint, information debasement, upgrading non-static allotment methodologies, restraining sensitive data stream and so forth. As far as third-party service is concerned, customers store their precise information in the database and storage service provided by a third party. Thus, outsiders have the obligation to keep up the security and protection of the information, which is the reason why outsiders need to empower an inspecting service. As per information systems control and audit, IT reviewing could be characterized as a procedure of conglomerating and assessing confirmation to choose whether a computational information framework shields resources, maintains information trustworthiness and secures sensitive user information, accomplishes hierarchical goals adequately and expends physical and computational resources proficiently.
Information is stored in different locations which are regulated by numerous associations: Cloud services are provided by various CSPs, which maintain hardware components, such as processors, memory and storage, in individualized parts. Therefore, the user information is stored in numerous locales which are controlled by a few associations. Thus, the purported “issue of numerous ways” could emerge based on the capacity of specialists and/or people to process and manage the administration by the accumulation, utilization, distribution and revealing of their personal information by others. Boundless universal information utilization, information sharing and pools of information storage among the associations would become an issue in the perplexing association of cloud services. It is very hard to verify who will assume the liability if anything undesirable happens to stored information. All the logging information must be checked and should keep information acquisition, information transmission or information change.
Accountability: This is another part of protection and security. Sufficient data is needed with respect to how information is overseen by the CSPs so they can keep track of information acquisition, information transmission or information change. That is the reason why the representatives of associations authorize the standards and directions used to maintain bookkeeping records.
2.6 Major Cloud Service Providers
This section discusses some popular CSPs, including Amazon, Microsoft, Google, Sun and Yahoo, which epitomize utilization of cloud computing. These CSPs are being used by individual customers having the extensive ventures discussed below.
2.6.1 IaaS CSPs
Amazon Elastic Compute Cloud (EC2):This is a business web service which enables clients to lease personal computers on which to run and convey their personal computer applications. EC2 permits versatile arrangement of office applications by providing a web services interface and an organization platform over which a client can make virtual machines (VM), for example, server cases, where the client can put and run the product of their choice.
Amazon announced a limited public beta test of EC2 on August 25, 2006. Access to EC2 was allowed on a first-come, first-served basis. For the most part, EC2 turned out to be accessible on October 23, 2008 with the help of Microsoft Windows Server.
Amazon.comfacilitates customer access with EC2 cloud as one of a few web services advertised under the sweeping title Amazon Web Services (AWS). 1It started its service as IaaS clouds with a variety of services, including S3 (for storage), CloudFront (content delivery), SimpleDB (for structured data storage), SQS (for reliable messaging), CloudFront Streaming (for video streaming), RDS (for relational database), and Elastic MapReduce (for information processing).
Читать дальшеИнтервал:
Закладка:
Похожие книги на «Cloud Computing Solutions»
Представляем Вашему вниманию похожие книги на «Cloud Computing Solutions» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «Cloud Computing Solutions» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












